 Cybercriminals are exploiting a lesser-known Microsoft 365 feature called Direct Send, originally intended to support internal devices like printers, to send emails that appear to come from trusted coworkers. These spoofed emails often bypass standard security checks, making them especially dangerous.
Cybercriminals are exploiting a lesser-known Microsoft 365 feature called Direct Send, originally intended to support internal devices like printers, to send emails that appear to come from trusted coworkers. These spoofed emails often bypass standard security checks, making them especially dangerous.
Why It Matters
Internal Email Spoofing Without Login Credentials
Attackers are abusing Direct Send to send fake emails from your own domain,and in some cases, the message may even appear to be sent from you to you. This technique requires no credentials, no gateway access, and no login.
What’s Happening
Our GoSecure Titan® IDR team has observed campaigns abusing Direct Send by sending spoofed messages directly to Microsoft’s smart host (e.g., mail.protection.outlook.com). The attacker manipulates the email headers to make the message appear internal, even though it’s from an external, unauthorized IP address.
Here’s a sample from a flagged header:
Received: from [141.95.71.213] (141.95.71.213) by
SA2PEPF00003AEA.mail.protection.outlook.com with Microsoft SMTP Server
Why It Works
- No login required: Microsoft’s infrastructure accepts mail routed via Direct Send to internal recipients.
- Spoofed sender: The attacker sets the “From” address as any internal user.
- Bypasses filters: Microsoft’s filters treat the message as internal, making it harder to catch.
- Evades detection tools: These emails may avoid third-party tools looking for external signs of compromise.
How to Detect Direct Send Exploits
Header Red Flags
- Emails received through Microsoft smart hosts from unauthorized external IPs
- Authentication failures (SPF, DKIM, DMARC) on your own domain
- Mismatched X-MS-Exchange-CrossTenant-Id values
- Strange entries in SPF records
Behavioral Red Flags
- Emails sent from users to themselves
- Foreign or suspicious IPs
- Unexpected attachments or odd filenames
What You Can Do
Enable RejectDirectSend in O365
Reject Direct Send
Microsoft has introduced an opt-in feature to block unauthenticated Direct Send messages. Enable it using PowerShell:
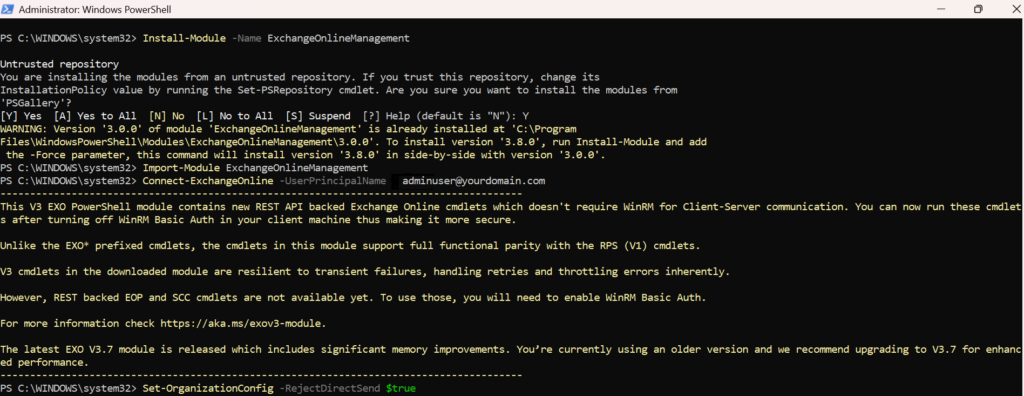
Once enabled, unauthorized messages will be blocked with:
550 5.7.68 TenantInboundAttribution; Direct Send not allowed for this organization from unauthorized sources
Additional Mitigation Steps:
- Implement a strict DMARC policy
- Flag unauthenticated internal mail for review or quarantine
- Enforce SPF hardfail in Exchange Online Protection (EOP)
- Set anti-spoofing rules in Microsoft Defender
Considerations
Please be aware that not all Direct Send emails are malicious. By enabling RejectDirectSend you may block some legitimate emails. Examples of legitimate use of Direct Send include:
- Automated reports from internal tools
- Scripted alerts or backups
- Authorized third-party platforms (HR, CRM, marketing)
If in doubt, do not click. Report it to your security team.
How GoSecure Is Helping
Our GoSecure Titan® IDR team is actively monitoring for this exploit and updating detection content. We’re also tightening backend rules in our infrastructure to reduce the likelihood of false internal trust.
If you need support reviewing your configuration or want help enabling protective measures, our team is ready.
Take Action Today
Sophisticated phishing threats can appear completely legitimate. If you’d like to assess your exposure or configure safer defaults, contact GoSecure today.



