 Author: Andréanne Bergeron
Author: Andréanne Bergeron
As Xiaomi smartphones show an increase in popularity, a surprising pattern emerges: cybercriminals are following the same trends as everyday users. Our research uncovers a striking overlap between popular consumer devices and those favored in illicit online activities. Are attackers simply adopting what’s widely available, or does brand loyalty extend into the cyber underworld?
In September, media reports highlighted significant research findings by Counterpoint Research: Xiaomi surpassed Apple in August 2024 to become one of the world’s largest smartphone brands. This milestone underscores Xiaomi’s growing presence in the smartphone market. According to Counterpoint Research’s graphic (see Figure 1), Samsung and Apple frequently alternate in holding the top position, but Xiaomi tends to rise in popularity, especially during Apple’s predictable seasonal declines.
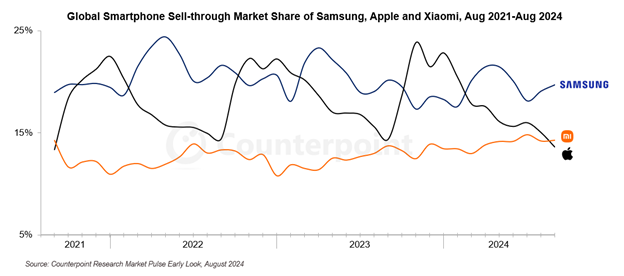
Figure 1. Counterpoint Research’s graphic from their website
The media totally exaggerates the significance of Xiaomi smartphones, especially when we take a global look at the figure above. While Xiaomi has gained attention for its growing market presence, it remains far behind industry giants like Apple and Samsung in terms of both sales volume and overall popularity. Nevertheless, Xiaomi has shown steady growth, carving out a respectable portion of the market. This consistent increase suggests that, although Xiaomi may not rival the market leaders yet, it is establishing itself as a notable player with a promising trajectory.
Given that these three brands command the largest share of the smartphone market, it raises the question of whether cybercriminals, compared to the general population, follow similar trends in device preference.
To explore this, we analyzed data collected from our research honeypots and our open-source tool, PyRDP. PyRDP is an advanced tool that captures and analyzes attacks on remote desktop protocol (RDP) connections, logging essential details such as the “client name” (the name of the device connecting to our systems). From February 2021 to December 2023, we collected data on 29,169 unique hits containing client names, allowing us to determine the type of devices that attackers use to access our honeypots.
Phone usage to connect to RDP
One of the interesting observations of our honeypot data was that attackers do not exclusively use computers to connect to our system through RDP. There are also instances of phone usage. Our findings indicate that a small subset of attackers—0.85% (or 250 cases)—connected via smartphones rather than traditional computers.
With our data, it is impossible to know for sure what are the reasons why a malicious actor might use a phone over a computer to access our system through RDP, but we came up with some hypotheses. Besides the fact that smartphones provide better mobility than a computer, phones may have different network identifiers (e.g., mobile IP addresses or VPNs) that are less likely to match known malicious patterns that Intrusion Detection Systems (IDS) might flag. Some cybersecurity defenses might not prioritize phone connections in their alerting protocols, potentially lowering the chances of detection. In the same vein of avoiding detection, mobile devices often leave a smaller digital footprint, particularly if the actor is using temporary or “burner” phones. Phones can connect through different networks, avoiding association with known malicious IP addresses tied to desktop environments. Finally, connecting over mobile data rather than a potentially monitored Wi-Fi or wired network can provide an extra layer of obscurity, as mobile network IPs rotate more frequently.
Device Popularity Across Brands
In Table 1, we present a detailed list of all smartphone brands used to connect to our RDP system, along with the frequency of their usage over the past three years. Our data reveals a striking trend: attackers connecting via smartphones show a strong preference for iPhone, Xiaomi, and Samsung—remarkably similar to the order of brand popularity in the general population. This alignment suggests that cybercriminals’ choices in mobile devices often mirror general consumer preferences.
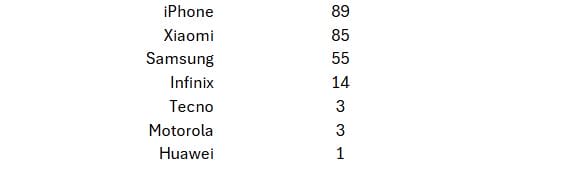
Table 1. Frequency of each smartphone brand used to connect to RDP
In a previous blog, we noted a similar finding in browser preferences, observing that attackers tend to favor the same popular browsers as the broader public. This reinforces the notion that cybercriminals may not be as different from typical users as one might expect. Their tech preferences align with mainstream trends, suggesting that even within the realm of illicit online activity, brand and tool preferences follow familiar consumer patterns.
This observation underscores an interesting point: while motivations may differ, cyber delinquents remain influenced by the same technology trends and brand loyalty that shape the broader digital environment.
Popularity Trends Over Time
To observe the increase of popularity over time, we mapped the number of instances in which an attacker would connect with one of the biggest smartphone brands over three years. One of the initial observations drawn from this (see Graph 1) is the marked increase in smartphone usage for accessing RDP in 2023. This upward trend indicates a shift in attacker behavior, suggesting that mobile devices are becoming more prevalent tools for cyber activities traditionally conducted on computers. This rise may reflect advancements in smartphone technology, making them powerful and accessible enough to support complex operations, as well as the growing availability of mobile-based hacking tools and techniques.
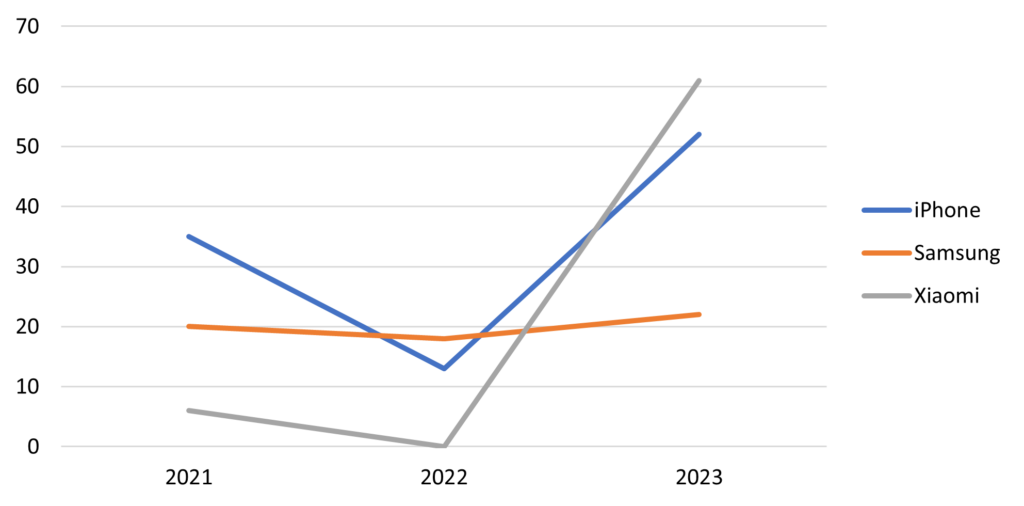
Graph 1. Use of the different smartphone brands over time by attackers in our system
When examining the brand usage trends over time, we observed a notable shift in 2023. Xiaomi showed a marked increase in popularity, even surpassing iPhone. In the CounterPoint research Figure presented at the beginning of this blog, we see that Xiaomi wins in popularity for only a certain period of the year, and this, only when iPhone is at an all-time low. The trend that we observed with our data is different in the sense that the rising prevalence of Xiaomi devices is way more notable than what is observed in the general population trend. This increase not only reflects Xiaomi’s growing appeal but also suggests that cybercriminals may be capitalizing on its accessibility, performance, and global availability.
Samsung usage shows a stable presence in the general consumer market as a trusted and widely-used brand. Similarly, among attackers, it is also a brand that has remained consistently steady. This trend aligns with broader market patterns, where Samsung continues to maintain a loyal user base across various demographics. Similarly, the iPhone has sustained its popularity over time. This enduring popularity highlights Apple’s strong brand loyalty and the widespread appeal of its devices, which remain attractive for their user-friendly interface, security features, and ecosystem integration. These patterns suggest that both brands are able to retain their appeal in both legitimate and illicit contexts.
Specificity of Xiaomi’s target market
Xiaomi initially focused on the Chinese market but has since expanded rapidly to India, Southeast Asia, and Europe. In India, it has been especially successful, frequently topping sales charts due to its competitive pricing and targeted marketing strategies. The brand’s popularity remains strong in densely populated regions, particularly China, where the sheer market size and demand provide a stable customer base over time.
Xiaomi’s appeal extends beyond general consumers to tech-savvy users, including some features that could attract malicious actors. One potential draw for these actors is Xiaomi’s MIUI, an Android-based operating system known for its high level of customization and frequent updates, which introduce new features and enhancements. MIUI’s versatility appeals to users who value personalization but also presents potential opportunities for exploitation.
Additionally, Xiaomi fosters a robust online user community, where fans discuss device features, customization options, and software updates. This community-driven environment encourages brand loyalty but also offers a resource that could be exploited by malicious actors. These forums provide a wealth of information, which, while intended to support users, could be leveraged by threat actors to identify vulnerabilities or tailor malicious strategies.
Conclusion
Our analysis reveals that cybercriminals’ smartphone preferences align closely with mainstream consumer trends, with iPhone, Xiaomi, and Samsung emerging as the most popular brands among both attackers and general users. Notably, Xiaomi has shown a marked increase in usage in 2023 in our data, surpassing iPhone, which suggests a growing appeal for attackers. This trend could be driven by Xiaomi’s accessibility, performance, and availability.
Also, the observed increase in smartphone use to access RDP in 2023 further indicates that mobile devices are becoming versatile tools in cyber activities, reflecting advancements in mobile technology and the proliferation of mobile-based hacking tools.
This blog post focuses on smartphones as tools for malicious actors rather than as direct targets. Our data did not allow us to determine whether the most popular smartphones are also primary targets for these actors. However, these findings underscore an interesting intersection between consumer technology trends and cyber behavior. Understanding these preferences provides valuable insights into cybercriminal practices, suggesting that broader market dynamics may indeed shape the tools and devices chosen by attackers.



