We are on the upward trajectory of AI. AI can be used to write anything from a blog post to a news story, even a thesis. It’s an incredibly useful tool that will save hours of time and make writing anything an essentially seamless task. However, with anything good, someone always seems to ruin it…Enter the bad guy!
We are on the upward trajectory of AI. AI can be used to write anything from a blog post to a news story, even a thesis. It’s an incredibly useful tool that will save hours of time and make writing anything an essentially seamless task. However, with anything good, someone always seems to ruin it…Enter the bad guy!
In the past, it was somewhat easy to discern whether an email was a phishing attempt simply by looking at the language and grammar being used. Here are a few examples of what the GoSecure Email Security Analysts within the MXDR team sees on a regular basis:
In the example below, we see an attempt to pass a malicious document to the recipient.
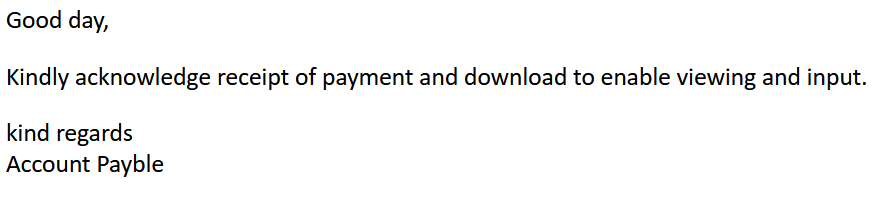
We can see multiple problems with this message.
1. A generic salutation, the sender does not know who is receiving this email
2. Poor use of words and grammar (ex. Download to enable viewing and input, Account not Accounts Payable)
3. Payment for what?
4. What am I downloading?
AI Generated example – All the red flags in the human generated phishing email above have been addressed by AI:
Dear Bill <Your company employee names are easily scrapped from the Internet>,
I hope this email finds you well. I am writing to let you know that we have received your invoice dated March 1, 2023, for the payment of $3500 for the services rendered. We have processed your payment and attached the receipt for your reference.
Please find the attached document for your records. If you have any questions or concerns regarding the payment or the receipt, please do not hesitate to contact us. We are always here to assist you in any way we can.
Thank you for your prompt payment, and we look forward to continuing our business relationship with you.
Please acknowledge receipt of this email by responding to <Bad Actors Email Address>. The sending email address is not monitored.
Best regards,
Jim Sweeny
Accounts Payable
How can I identify and protect myself and my company?
- Do you have any idea what this receipt is for? If not, don’t open any attachments or click on any links.
- Remember the threat actor is trying to entice you into opening the attachment. Notice the line $3,500 for services rendered. Take a minute and ask around if anyone has heard of this payment.
- Never respond to an unsolicited email address, this opens a new channel for the bad actor to try and trick you.
- Hit reply and look at the email address you would be replying to (note: don’t reply). Is it an address you recognize? If it is a company address you recognize, ask yourself why the sender is asking you to reply to a Gmail or other email address that you don’t recognize. Here is a good example of how hitting reply can help you identify a phishing email. In the example the name of the recipient company is used in the display name of the sender (rockisland) but after hitting reply, we can see that the actual reply to address will be a compromised address (sales@margilpartyrental.com)

- What if you recognize the sending email address and the bad actor is not asking you to acknowledge receipt to a different email address? Remember that email addresses get compromised all the time so ask yourself a few questions first: Does this email make sense? Did I/we make a payment that we are expecting a receipt for? We have paid this company before, and they have always mailed our receipt, or the receipt was always available online at any time including when the bill was paid.
- Get GoSecure MXDR and leave the analysis to the experts!
Let’s look at another common phishing attempt. The attempt below is trying to fool HR into changing an employee’s direct deposit information to the bad actor’s information.
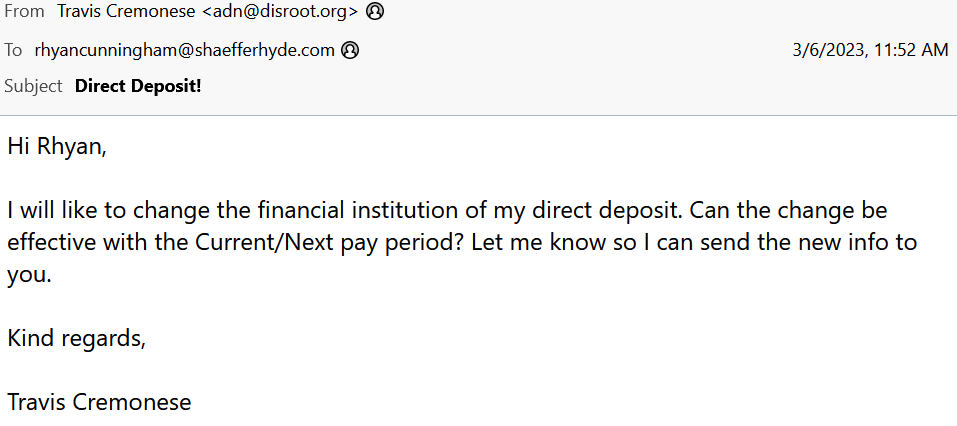
In this example, we can see a couple of problems.
1. Subject – Direct Deposit!
2. Poor use of words and grammar (ex. I will like to change, financial institution instead of bank/banking)
3. The sending email address does not appear to be from the company domain
4. No small talk (ex. How are you)
AI Generated example – Small talk, proper grammar, and additional language (provide me with any guidance, let me know any additional steps) that adds legitimacy to the request:
Dear Rhyan,
I hope you’re doing well. I am writing to inform you that I need to change my direct deposit information. I would like to have my paycheck deposited into my new bank account starting from next month.
Could you please let me know what paperwork is required for this change? Also, could you provide me with any guidance on the steps I need to take to ensure the process is completed smoothly?
Thank you for your assistance in this matter. Please let me know if there are any additional steps I need to take or if you have any further questions.
Best regards,
Travis
How can I identify and protect myself and my company?
- Hit reply and look at the email address you would be replying to (note: don’t reply). Is it an address you recognize? Is it the company domain name? In our example above we can see that the email contains the display element (Travis Cremonese) and after hitting reply the actual reply to address will be visible (adn@disroot.org). The display part of the email will be the name you might recognize; it may be your boss or the vice president or anyone else at the company. That is why it is imperative that you look at the whole email address, the bad guy will try and hide the real address and trick you by hoping the display name is enough. As you can see from our example that the reply to domain is disroot.org BUT the recipient company name is shaefferhyde.com. This is an example of a fraudulent request to change a person’s direct deposit and how simply hitting reply can help identify the bad request.
If you believe the request is legitimate, ask yourself these questions, have you had communication by email with this person before, is the language used what you would expect? Never respond to an unrecognized email address, this opens a new channel for the bad actor to try and trick you. If the supposed sender (ex. “Travis”) is emailing you from a free mail like Gmail or any non-company email address, never respond, call if a phone number is given, instead try to physically contact the employee, and verify the request. - What if you recognize the sending email? Remember that email addresses get compromised all the time: Does this request make sense (If it is your boss, would your boss make this request)? Always attempt to validate this type of request by any means EXCEPT replying to the original email or replying by phone if a phone number is given.
- Get GoSecure MXDR and leave the analysis to the experts!
Never let a good crisis go to waste…
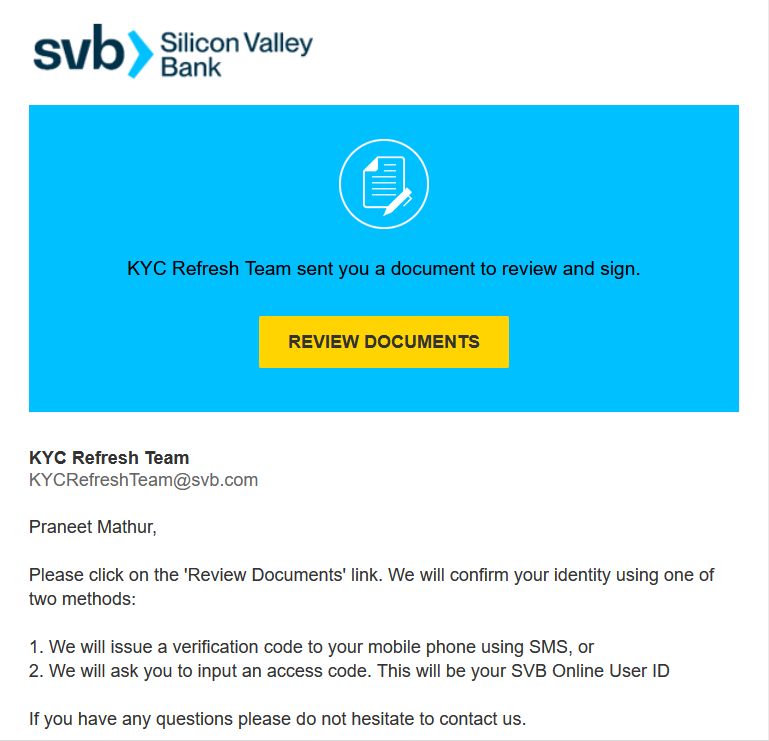
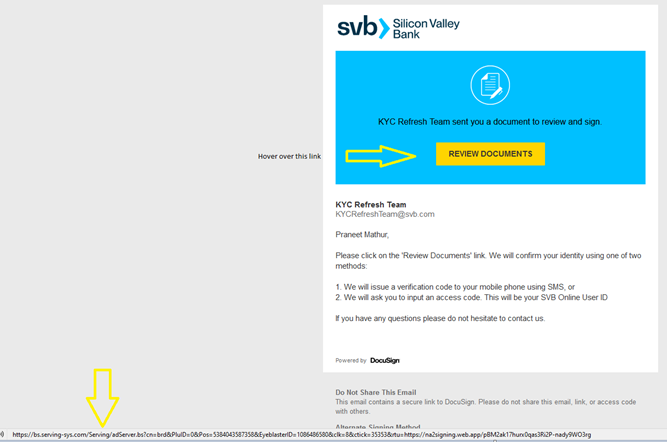
Undoubtedly by now, everyone has heard about the problems of Silicon Valley Bank (SVB). Threat actors will take advantage of any crisis. What if your company was a shareholder or member of SVB and you received the following email, designed to look like a DocuSign email? KYC is an end-to-end identification tool that many banks use to verify a user’s identity.
In this example, we can see a couple of problems.
1. They state “using one of two methods”. Two methods are not given for verification as number 2 is just an extension of method 1.
2. Poor use of words and phrasing (ex. “We will issue a verification code to your mobile phone using SMS” instead of “Via Text Message”. On number 2 the bad actor says we will ask you to input an access code, this would be in reference to texting an access code, but then the bad actor tells the recipient the code will be their SVB Online User ID.)
AI Generated example – Rewording of the received message:
Subject: Re-verification of KYC required
Dear Praneet Mathur,
We hope this email finds you well. We are writing to inform you that as part of our ongoing efforts to maintain the highest level of security and compliance, we need to re-verify your Know Your Customer (KYC) information.
To ensure the smoothest and most convenient process for you, kindly click the “Review Documents” link above, after agreeing to our new security policy, we will offer two methods for re-verification:
- Via text message – We will send you a unique code to your registered mobile number. You need to enter the code in the verification section of your account.
- Via email – We will send you a unique code to your registered email address. You will need to enter the code in the verification section of your account.
Please note that this re-verification is mandatory, and failure to comply may result in the suspension of your account until the verification is complete. Also, kindly note that the verification process may take up to 48 hours.
If you have any questions or concerns regarding the re-verification process, please do not hesitate to contact our support team at [Bad Actor Email Address].
Thank you for your cooperation in this matter.
Best regards,
SVB KYC Team
How can I identify and protect myself and my company?
- In our sample, the bad actor spoofed DocuSign, making it appear even more legitimate. The bad actor used a current banking crisis to try and steal your bank access credentials.
- The AI generated sample is good, but there are still a couple of things that you as a recipient could check. The bad actor would not use an actual SVB email address, hover over the [bad actor email address] and look in the bottom left corner of the email to see what email address is hiding behind the face of the email. Secondly, do the same thing with the “Review Documents” link, simply hover your cursor over the link and look at where the link actually goes. If it isn’t leading to DocuSign then don’t click the link. In our case, the link was going somewhere else, a redirector in which if clicked, came to a phishing page designed to look like an official SVB form. It is important to note that bad actors do use DocuSign for malicious purposes. You can see in our sample that the link does not go to DocuSign but to a malicious website. If the link did go to DocuSign and you clicked through to a page that just had a link to click to view the supposed document, DON’T CLICK that link.

- Get GoSecure MXDR and leave the analysis to the experts!
Additional tips on detecting phishing:
Remember that anyone’s email can be compromised and accessible by a bad actor.
- Be wary of receiving an out of context email from a known contact. The email may be out of the blue and may simply say “Please see attached” or “Please review” or the email may contain a link (which goes to a malicious website).
- If you are having a conversation with someone and they always address emails to you in a certain way but then out of the blue their tone turns formal or urgent, “I wanted to inform you that our company has changed our Automated Clearing House (ACH) information, please send the payment to this bank account now instead of the old account”
- Be wary if the person responds but doesn’t answer your questions or doesn’t address the email in context.
- If you are a CPA or financial institution, be wary of an email asking to start business with you, “I am looking for a new CPA for this tax year. Can you help? My last CPA is no longer working”. “I am the CEO of a company and I am looking to change my bank, I do $13M in business yearly”. Attempts like these may be openers by a bad actor and GoSecure Titan IDR recommends vetting before accepting any documents from the sender.
- Never blindly accept the request to change ACH information for someone you pay for without validating the request by phone.
- Never blindly accept a 3rd party request stating they have been retained by your client to perform an audit in which they request all outstanding invoices, without validating with your client by phone.
- Never blindly accept a demand letter claiming that you are in violation of a copyright for using an image on your website. Any demand for payment is not legitimate in this case. Consult a legal professional if you feel the demand might have merit.
- Always be wary of emails from anyone sharing a document with you, especially if you have no idea who sent you the document or what the document is in reference to.
- Always be wary of emails with no context that simply say, “Please see attached” or similar. The email may just say “Hi” in the body or in the subject.
When in doubt get GoSecure MXDR for total protection!