Author: Andréanne Bergeron
Author: Andréanne Bergeron
Examining the brute-forcing attack patterns on our Remote Desktop Protocol (RDP) honeypot systems reveals the discernible behavior of automated scripts. Yet, upon closer inspection of the temporal patterns associated with these attacks, subtle nuances indicative of human behavior begins to emerge.
We’ve accumulated a wealth of data from attempted logins on our exposed RDP honeypot over time. In a previous blog, we delved into the human presence revealed by these login attempts. Now, turning our focus to the temporal attack patterns proves highly insightful, as they unveil valuable information crucial for understanding the tactics employed by attackers.
To visually depict attack patterns, we generated calendar-style heatmaps. Each heatmap provides a comprehensive view of one IP address’ activities throughout a month (July 2022). The Y-axis (vertical) corresponds to the day of the month, while the X-axis (horizontal) represents the hour of the day. Colors signify the attack frequency, with a unique legend for each attacker located on the right side of the graphic.
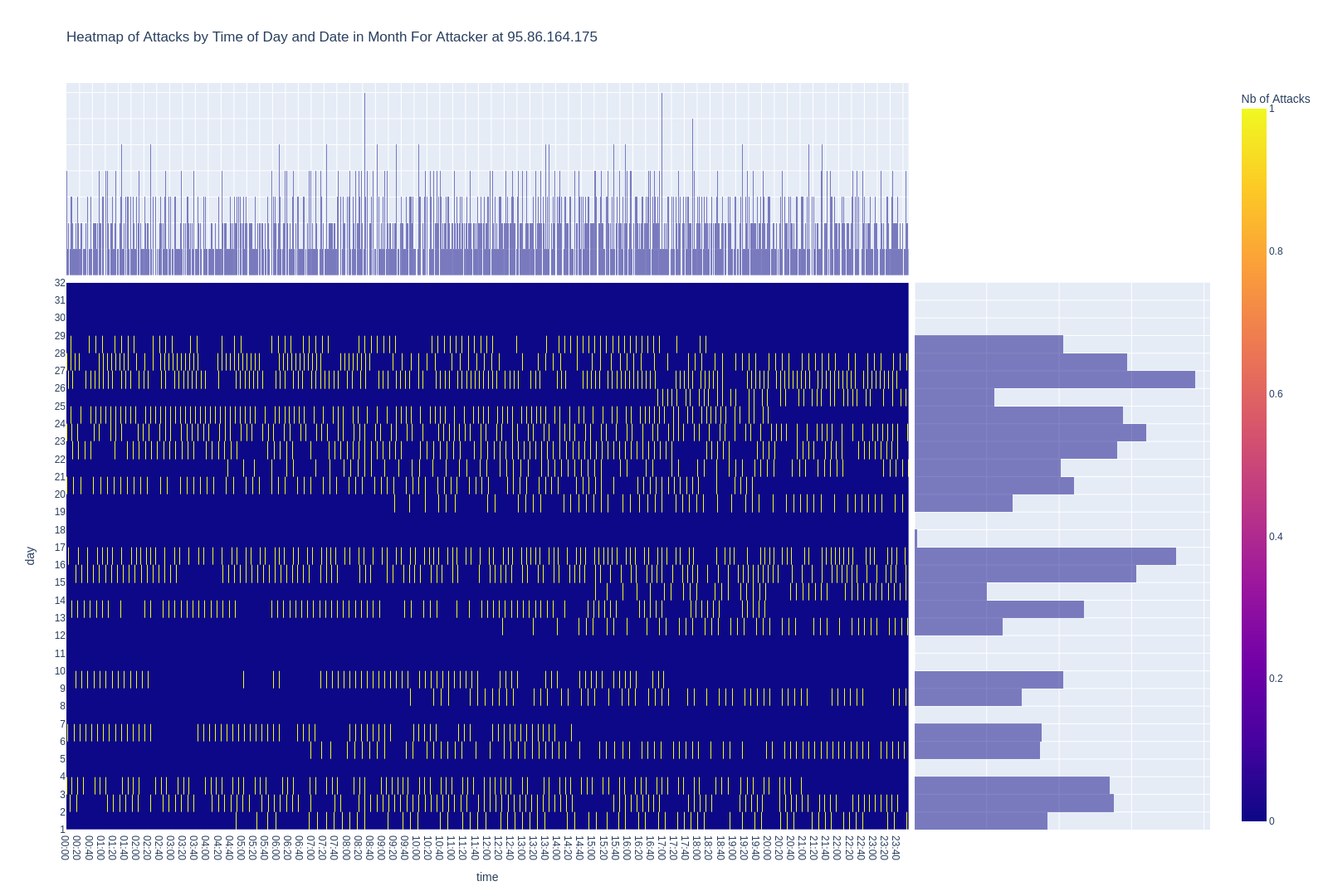
In the first scenario (see Graph 1), the activities exemplify the profile of a persistent attacker engaged in continuous, fully automated login attempts on our system.
The attacks are persistent, rapid, and relentless. One can envision a compromised computer tirelessly executing tentative logins on the target. Interestingly, this pattern was somewhat rare within our dataset (0.8%), unveiling other noteworthy attack behaviors.
Human Strategies in Attack Patterns
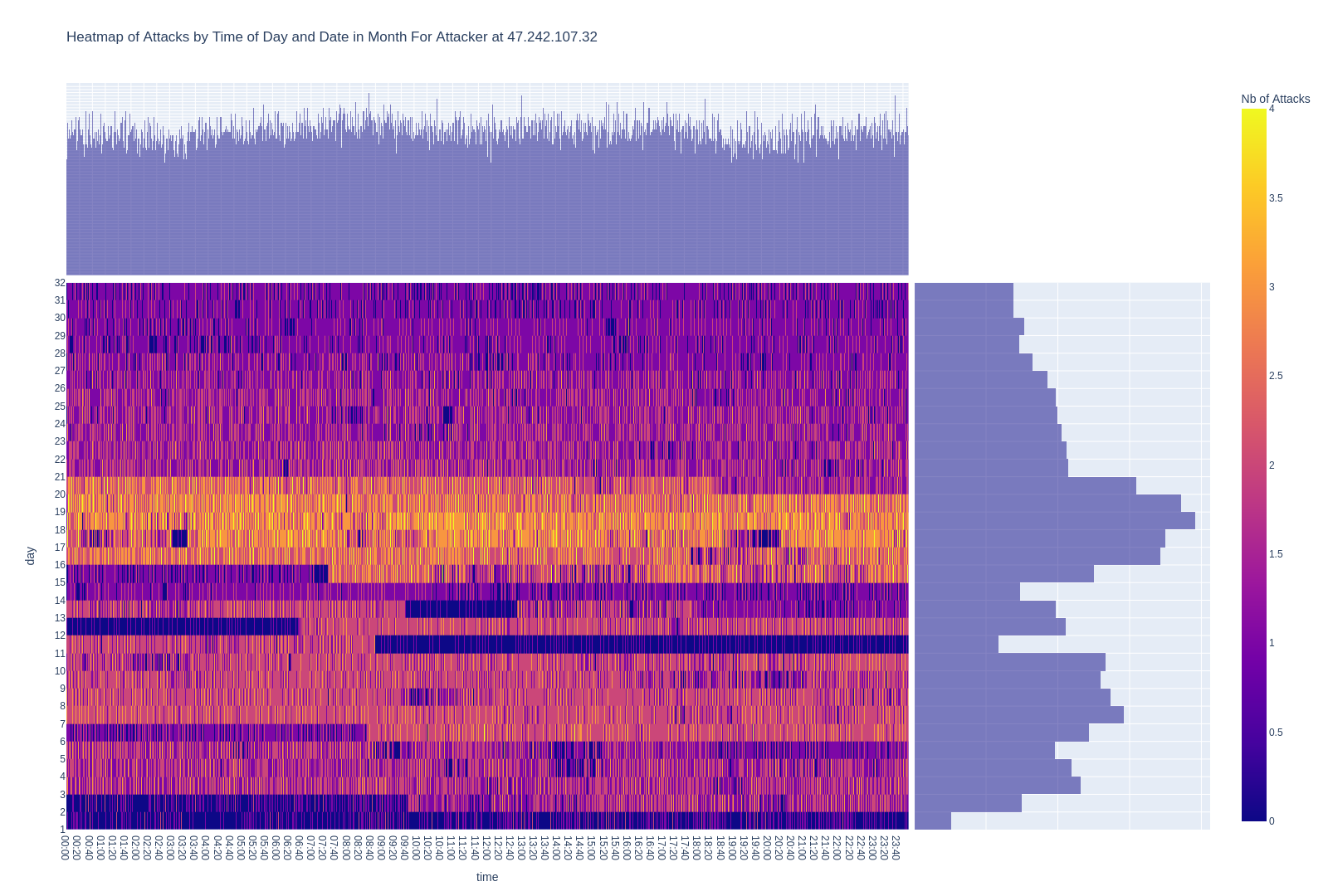
In the second scenario (see Graph 2), the attack dynamics leave constant onslaughts to instead present themselves in discernible blocks. Our working hypothesis suggests a distinctive approach by these attackers, involving the utilization of lists containing around 6,300 credentials. This strategy entails systematically testing each set of credentials for potential system entry. Upon completion of an automated attack list, the intervention of a human operator is necessary to initiate a new attack block, introducing a new set of credentials into the equation.
Also, the irregular pauses observed, seemingly arbitrary in duration and sporadically dispersed throughout different periods of the day, point to the human operator’s intermittent presence at the computer. These pauses, characterized by their randomness, introduce an additional layer of complexity to the attack pattern and represent approximately 14% of the behavior observed in our dataset.
Avoiding Detection and Weekend Patterns
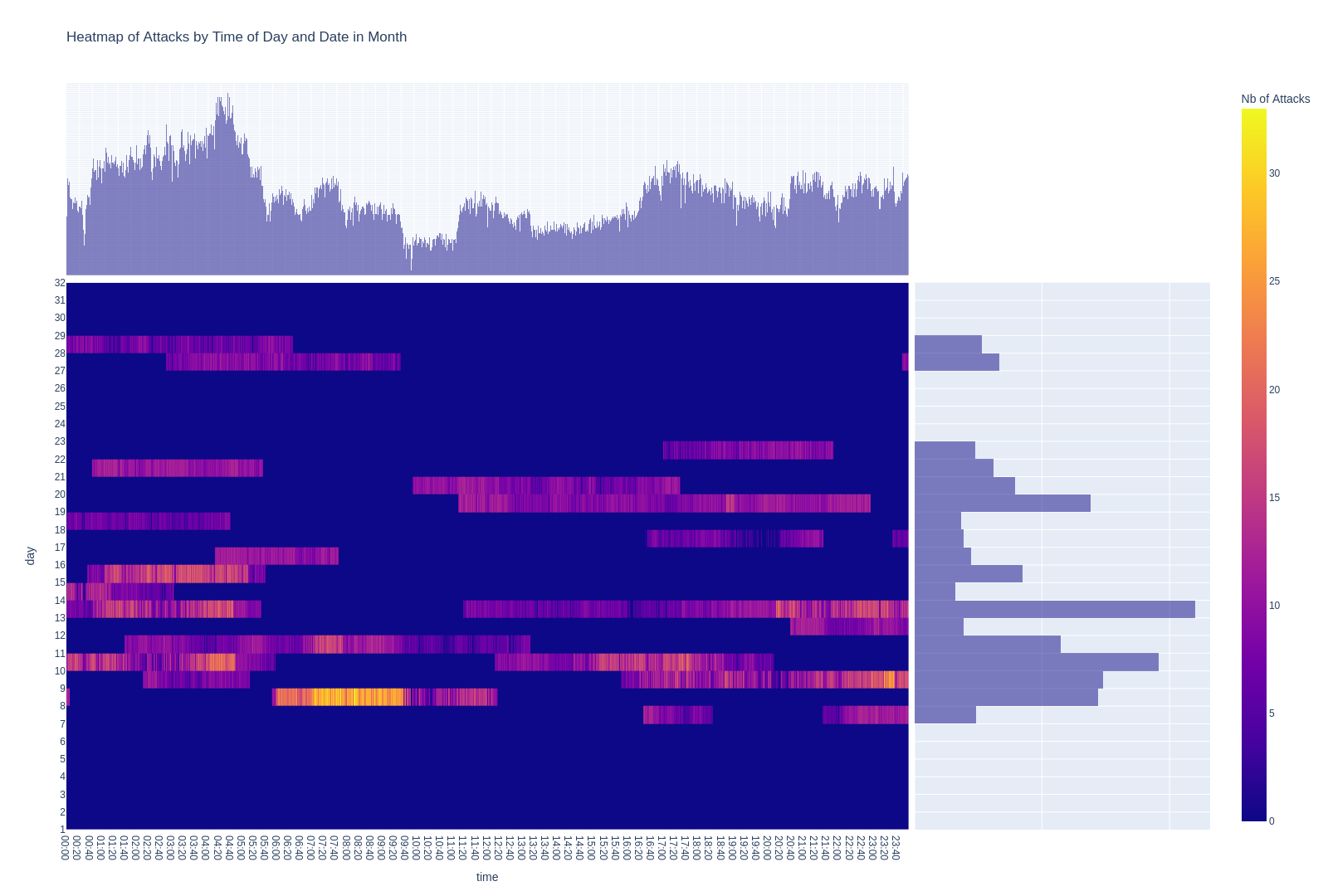
Attackers often employ a strategic approach involving the deliberate insertion of delays between successive attacks. The purpose of this calculated tactic is to effectively mitigate the risk of detection by security systems. This third scenario is exemplified below (see Graph 3), showcasing a pattern where each attack is strategically spaced apart by a couple of seconds. This pattern strongly suggests the implementation of an automated attack specifically programmed to incorporate intentional delays between each tentative login, enhancing its ability to evade security measures and operate with a deceptive resemblance to human interaction. The number of attackers imposing delays between attempt logins represents 32% of our dataset.
What adds a compelling layer of intrigue to this example is the strategic placement of pauses during entire days. When scrutinizing the calendar for July 2022, it becomes evident that the pauses align with weekends. Two hypotheses emerge to elucidate this distinct attack pattern.
The first hypothesis concerns the “office-like” hours of attacks. There have been documented instances and allegations of state-sponsored cyber activities involving China. The Chinese government has been accused of engaging in cyber espionage and hacking campaigns targeting various entities, including other countries’ government systems and organizations. These activities are believed to be carried out by different Chinese state-sponsored hacking groups.
One prominent example is the involvement of groups like APT1, also known as Unit 61398, which has been linked to the Chinese military. Reports and analyses by cybersecurity firms and government agencies have detailed their alleged involvement in cyber espionage operations targeting a range of sectors and industries.
Therefore, should the attackers indeed be federal employees adhering to regular office hours, their schedule would probably exhibit days off, mirroring typical weekends.
The second hypothesis posits that a computer has been infiltrated and is being utilized as a proxy for attacking the target. The owner of the compromised computer may be unaware of its compromise, unwittingly facilitating the hacker’s activities. This scenario could involve an office computer systematically powered down on weekends.
Nighttime Patterns
There is a fourth scenario (see Graph 4 below) unveiling another intriguing pattern: an 8-hour block where no attacks are initiated. The succeeding tentative logins might be running but there is a hole of 8 hours in which none are started. This observation is noted among 15% of attackers.
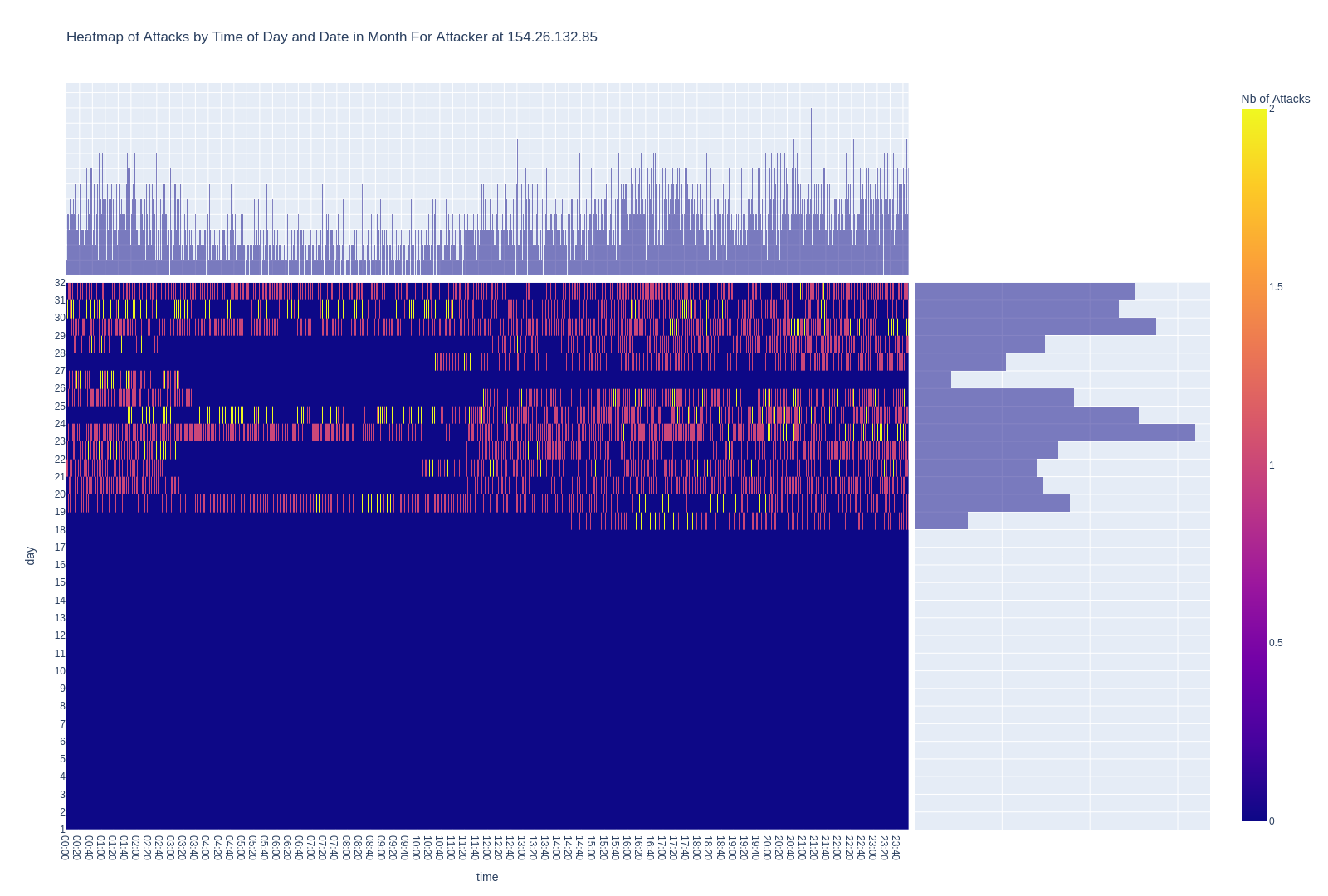
Several hypotheses can be explored here. First, when a human intervention is required to initiate the block of attacks, a natural period of dormancy occurs. For instance, adherence to sleep cycles renders individuals unavailable during specific hours, resulting in an observable 8-hour hiatus.
Beyond the sleep cycle, the 8-hour gap may also be indicative of a work cycle. Therefore, a second hypothesis suggests a scenario where the hacker initiates attacks while at home but abstains during legitimate employment hours, when they are away from home.
A third and final hypothesis is that the hacker is using a compromised computer that is shut down at a specific time, beyond their control. However, this hypothesis is less compelling, as the 8 hours blocks are not constant every night.
Conclusion
The human touch in automated attacks is strikingly apparent. Even within the realm of heavy attackers, distinctly human behaviors emerge. The observed sample of attackers on the RDP honeypot reveals the diverse strategies, from continuous assaults to deliberate pauses, reflect a nuanced understanding of the target. Notably, the alignment of attacks with weekends and sleep cycles hints at the attackers’ daily lives. The deliberate imposition of delays between attacks serves to mimic human behavior, aiding in evading detection. It’s essential to bear in mind that our adversary is human, not a machine.
Researchers: Here is the Code!
As a courtesy to the cybersecurity research community, we shared the code for the calendar heatmaps on our GitHub.
We would like to thank Olivier Bilodeau for his help in generating the calendar heatmaps.