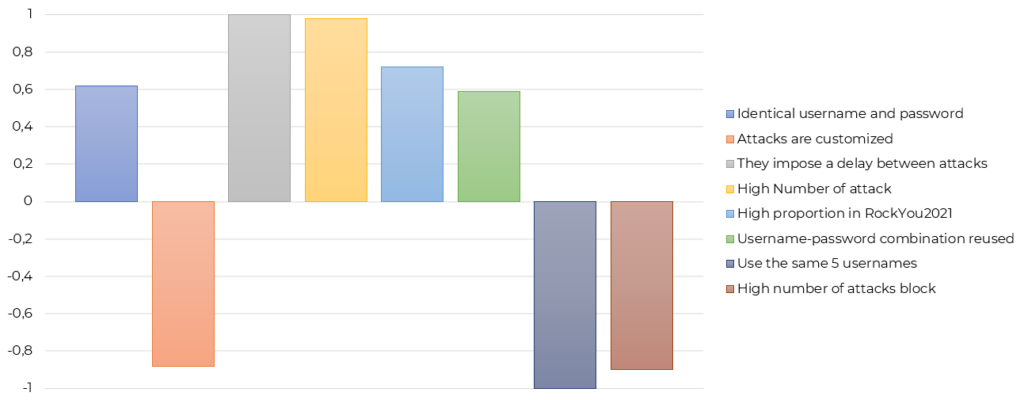Author: Andréanne Bergeron
Characterizing attackers gets us closer to reveal who they are. Our study categorizes the behavior of Remote Desktop Protocol (RDP) attackers. Based on 3.4 million login attempts, we reveal five different clusters of brute force attacks strategies.
This exploratory research identifies the different profiles of attackers based on their strategies. The dataset used in this study comes from 3 months of traffic on our honeypot. We launched a set of high-interaction honeypots on the internet exposing Remote Desktop Protocol (RDP) access. RDP is a Microsoft protocol allowing users to access the graphical interface of remote computers.
We analyzed data that we monitored on our research honeypot from July 1 to September 30, 2022, which represents 3,427,611 login attempts. The data collected about each login attempt include: 1) timestamp; 2) IP address; and 3) the credentials tried by the attacker. Many observations can be made from these three pieces of information. The attempt logins were then grouped by IP addresses to study the behavior of attackers. There was a total of 1,529 unique IP addresses involved in the attacks.
Latent Class Analysis has been used to explore the different profiles based on the different elements observed in the sample in terms of strategies. Each element used to form the profiles is presented in the table below.
| Identical username and password | The attacker is using the same character sequence for the username and the password. |
| Attacks are customized to the target | There is the presence of the honeypot certificate name or computer name in the credential used. |
| Delay between attacks | There is a short delay between attempt logins. |
| High number of attacks | More than 50 login attempts by the same attacker. |
| High proportion in RockYou2021 | More than 60% of the passwords used in attempt logins are present in RockYou 2021. |
| Username-password combination reused | The attackers use the same username-password combination more than once. |
| Use the same 5 usernames | Instead of trying different combination of username and password, the attackers focus on 5 usernames and try them with a large number of different passwords. |
| High number of attacks block | Login attempts are usually performed in a rapid sequence. In some cases, there are long pauses in the attack pattern. The rapid login attempts followed by a pause is what is considered as an attack block. |
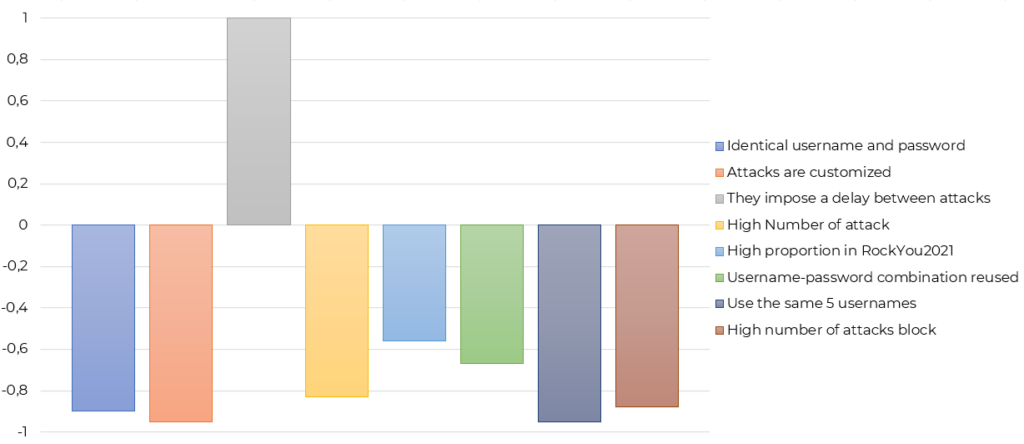
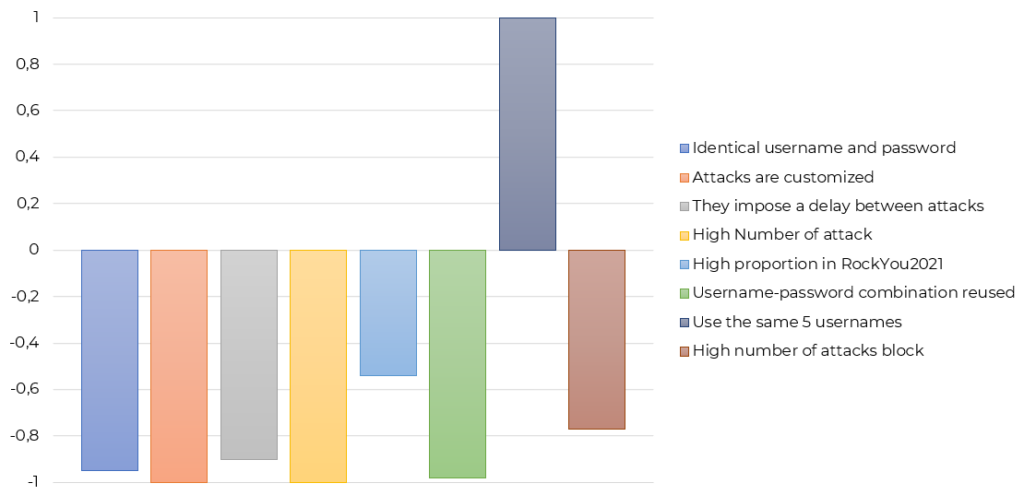
Below, we present the 5 clusters which came out of the Latent Class Analysis. The same graphic for each cluster presents the elements characterizing the cluster. The right way to read the graphics is to look at all the positive columns over 0.6 as they will be significantly associated with the cluster. The negative figure does not mean that the element is associated with its opposite, but rather that it is strongly not associated with the cluster. A name and an image have been attributed to each cluster to describe them better.
Cluster 1: The delayed timer

The element that characterizes this cluster is the fact that the attackers impose a delay between attacks. Usually, automated attacks include many attempted logins per second. However, some systems block, or slow down successive login attempts that are too quick for human behavior. Imposing a small delay between login attempts might be a great strategy to avoid these countermeasures and therefore avoid detection. This allows them to keep trying to brute-force their way in for a longer time.
Cluster 2: Vertical sprayer

Cluster 2 is characterized by the fact that they use the same 5 usernames with a bunch of different passwords. They seem to be very confident about their 5 usernames and try them as much as possible. This type of attack can be compared against user-spraying cyberattack in which the attackers are trying many different usernames with similar passwords (horizontal spraying). On the contrary, vertical login attempts would focus on a few different and generally common usernames (Administrator, support, etc.) with a larger set of passwords.
When it comes to the art of painting with spray cans, horizontal spraying is known to give better results. The reason is that it is easier to keep your wrist from sweeping if you are spraying horizontally rather than vertically. However, when it comes to brute-forcing systems, which technique is the most efficient is not so clear. On our systems, attackers had limited prior information on their target so we can assume that they strongly relied on common usernames in the short list they tried.
Cluster 3: Targeting crew
 The attackers of this cluster are characterized by the fact that they are heavy attackers, who impose delay between login attempts to avoid detection, but most importantly, who customized attacks. There was the presence of the target certificate name or computer name in the credentials (either for the username or the password). Those attackers are the most sophisticated compared to the other clusters. They went to find the information and try to leverage it to access the system. They also might use the same character chain for the username and the password, assuming that the RDP administrator uses the same for both.
The attackers of this cluster are characterized by the fact that they are heavy attackers, who impose delay between login attempts to avoid detection, but most importantly, who customized attacks. There was the presence of the target certificate name or computer name in the credentials (either for the username or the password). Those attackers are the most sophisticated compared to the other clusters. They went to find the information and try to leverage it to access the system. They also might use the same character chain for the username and the password, assuming that the RDP administrator uses the same for both.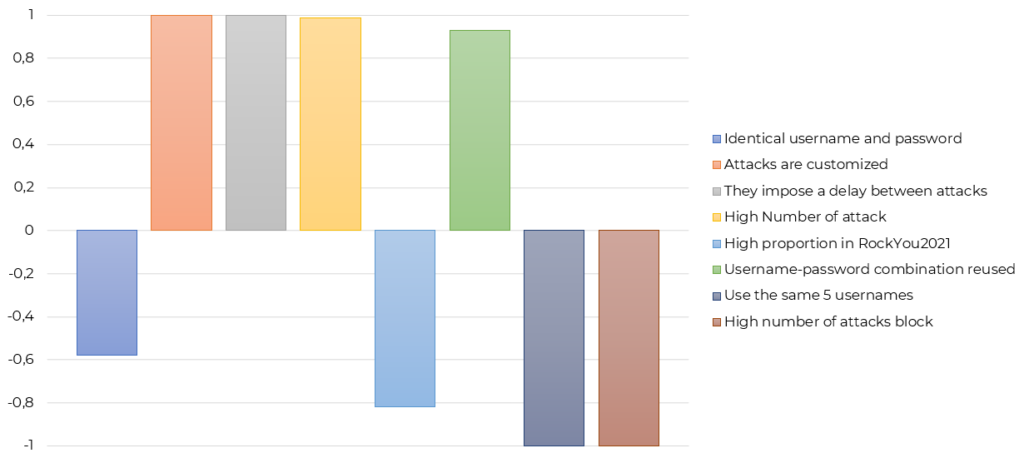
Cluster 4: Basic automation
 The attackers from this cluster are associated with the fact that their credentials mostly come from data leaks (RockYou2021) but more importantly, the cluster is significantly characterized by a high level of human intervention. Attackers in this group seem to be using short lists of credentials for which they have to launch a script that will go through the list. When the script is done with the list, someone has to manually start another one. Therefore, a high proportion of attack blocks suppose a high level of human intervention in the attacks. This high level of intervention is inefficient. That is why we consider the attackers of this cluster as basic. They tend to use data leaks that are readily available on the internet in their login attempts, and they need to intervene to launch their list instead of them to be automated.
The attackers from this cluster are associated with the fact that their credentials mostly come from data leaks (RockYou2021) but more importantly, the cluster is significantly characterized by a high level of human intervention. Attackers in this group seem to be using short lists of credentials for which they have to launch a script that will go through the list. When the script is done with the list, someone has to manually start another one. Therefore, a high proportion of attack blocks suppose a high level of human intervention in the attacks. This high level of intervention is inefficient. That is why we consider the attackers of this cluster as basic. They tend to use data leaks that are readily available on the internet in their login attempts, and they need to intervene to launch their list instead of them to be automated.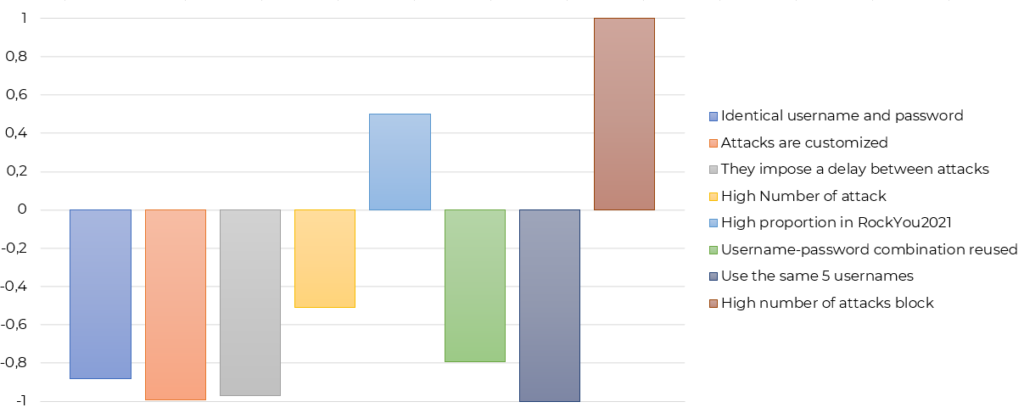
Cluster 5: Lost in the loop
 It is fair to say that attackers of this cluster do not seem to have one particular strategy: they are heavy attackers; most of the credential they use are part of the big credentials’ leaks list of RockYou 2021; they impose a delay between connections to avoid detection; they use the strategy of using a username identical to the password.
It is fair to say that attackers of this cluster do not seem to have one particular strategy: they are heavy attackers; most of the credential they use are part of the big credentials’ leaks list of RockYou 2021; they impose a delay between connections to avoid detection; they use the strategy of using a username identical to the password.
One observation is worth mentioning: They reuse the same credential combination more than once against our system. Since they are heavy attackers, it gives the impression that they might be a team of hackers working on the same targets and not communicating well on what has been tried. Or it can be a disorganized and not so sophisticated hacker. In any case, they look like the confused ones.
Mitigation related to clusters
In cluster 1, attackers impose a delay to imitate human behavior and avoid detection. However, the delay between login attempts is short so the attacks are still efficient. The more attempts they can fit in a day, the better. Calculating jitter between connection attempts might not be as efficient as it was before to discriminate between human behavior and automated behavior.
In cluster 3, attackers leverage our account information against us by adapting the credentials they try. The usual advice many organizations have given for years about credential hygiene is still relevant. Choosing strong passwords is still important but, changing the default Administrator username is essential. Not using personal information or company information in credentials is also important.
Cluster 4 reminds us that some attackers exclusively use passwords from data leaks. It is no longer recommended to establish passwords expiration policies, or in other words, to change our password every 3 months since it creates a habit of weak passwords among users (CompanyNameWinter123). However, changing our credentials after a data leak is crucial to secure our accounts.
One of the most efficient countermeasures for blocking heavy attackers’ brute-forcing is a lockout policy like the one established by Windows 11 by default. That policy automatically locks user accounts after 10 failed sign-in attempts. The account will be blocked for 10 minutes which will decrease the efficiency of brute forcing significantly and will be much more time consuming for attackers even if they use automation to try again after 10 minutes. Imposing a delay of a few seconds will no longer be efficient.
Conclusion
Our system is targeted by a login attempt on average every two seconds. The overall strategy of attack is, however, highly different from one threat actor to another. Documenting the different types of attackers is our way of sharing information to start a discussion about different prevention solutions. If you have mitigation ideas, do not hesitate to share!