Isn’t there a better moment than the Holiday season to release a major update of our RDP Attack and Eavesdropping tool PyRDP? That’s right, pour yourself a little glass of eggnog, sit in a comfortable chair, put on some Christmas music and read about the PyRDP updates by the fire.
Isn’t there a better moment than the Holiday season to release a major update of our RDP Attack and Eavesdropping tool PyRDP? That’s right, pour yourself a little glass of eggnog, sit in a comfortable chair, put on some Christmas music and read about the PyRDP updates by the fire.
On Comet, on Cupid, on Donner and Blitzen!
Like flying reindeers, pyrdp-convert, the tool to convert RDP captures into video, is fast and it got 6x faster with the last release! Additionally, we made it more robust by reducing the number of crashes, more flexible by allowing greater conversion flexibility and by improving session identification in Pcap files.
Had a very shiny nose…
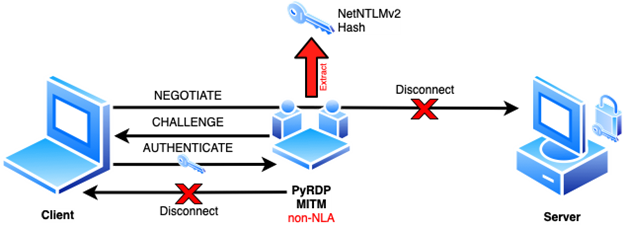
The headline feature for this release is the ability to capture NetNTLM hashes on any connection we can intercept. A feature we documented in a blog post earlier this year:
This feature offers password cracking and pass-the-hash opportunities to the attacker and the ability to detect and prevent this type of attack is quite limited.
As you can see from the above video demo, the potential certificate error is never displayed to the user. Certificate validation happens after the NetNTLM exchange under RDP’s Network Level Authentication (NLA) which is why it is never displayed. We reported this issue to Microsoft and they told us it works “as designed”. Since then, our advice has always been the same: RDP shouldn’t be used on untrusted networks like public Wi-Fi. It needs to be wrapped in a VPN.
Also recently added to this release is the ability to set the Net-NTLM challenge to a predefined value which can significantly accelerate hash cracking.
You would even say it glows…
Other polish and improvements include:
- New protocol versions supported: RDP 10.9 and 10.10
- A bind-address option for the Monster-In-The-Middle (MITM component)
- Documentation updates including improved certificate extraction instructions to mount RDP NLA Attacks
Then one foggy Christmas Eve…
This release includes fixes to an important memory leak when converting very large captures to video.
There is also a security update backported from rDesktop for vulnerabilities that Checkpoint found and disclosed in 2018.
Important fixes around device redirection (for file capture) and clipboard stealing were also made recently. If you had PyRDP stall on you during file transfers, you should give this version a try since this hard-to-debug long-standing issue has been resolved once and for all.
Won’t you guide my sleigh tonight?
Starting with this version, we are now packaging PyRDP in ARM64 docker images. Docker ARM64 images pave the way to future embedded RDP attacks. One day, Santa could install a transparent RDP interceptor on a Raspberry Pi in your network as he brings gifts to households!
We also significantly improved our testing infrastructure to catch errors sooner and validate the PRs we receive.
You’ll go down in history…
Most of the changes discussed in this blog post were featured in last year’s BlackHat Arsenal. Descriptions of attack scenarios and mitigation advice can be found in presentations that we have given recently around RDP Attacks.
Last but not least, we did some backward incompatible changes of concern to those who consume the JSON event stream that you can read about here.
You can grab version 1.2.0 from our GitHub repository.
A special thanks to the contributors of this release: Alexandre Beaulieu, Lisandro Ubiedo, Francis Labelle, Lukas Kupczyk, simonhuang, Jonas and Flare Systems!
Happy Holidays and see you next year!