 Author: Andréanne Bergeron
Author: Andréanne Bergeron
To study credentials attacks on RDP, we operate high-interaction honeypots on the Internet. We analyzed over 2.3 million connections that supplied hashed credentials and attempted to crack them. This article will highlight insights from these attacks and provide mitigation advice.
The Remote Desktop Protocol (RDP) allows users to connect to computers remotely. The pandemic radically increased the amount of people using RDP services to work from home. The high number of computers accessible via RDP, and the popularity of default usernames and weak passwords, has made RDP a favorite point of entry for criminal hackers looking to break into an organization’s network. It is therefore likely that any computer exposing RDP to the Internet is of interest to criminal hackers and is likely to be the subject of frequent attacks. This blog post contributes to the development of knowledge around the protection of organizations using RDP by describing the danger, looking at the volume and frequency of attacks, and some of the different strategies employed in attempting to guess usernames and passwords on RDP-exposed systems.
To study credentials attacks on RDP, we operate high-interaction honeypots on the Internet. We analyzed the connection attempts over two different periods of time: July 2022 and September 2022. Our sample includes 2,348,152 collected hashes (1,130,770 in July and 1,217,382 in September) from the attempts to connect to our server. Among them, 1163 attacks provided the right username and password combination to gain access to our fake system.
Origin of the Attacks
IP addresses used on the Internet are allocated geographically, so it’s possible to discover approximately where in the world the login attempts on the honeypots came from. To avoid detection, it’s common for attackers to use proxies or compromised computers that can be operated from anywhere around the globe. As such, the location of the IP addresses used to make login attempts is unlikely to reveal anything about where the attackers were located, but it can indicate where the proxies or compromised computers are.
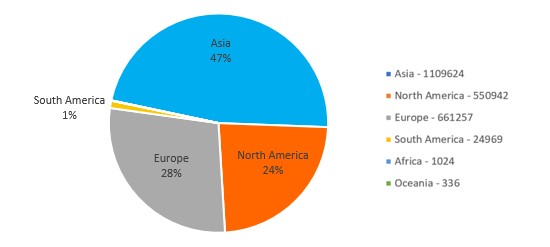
The list of login attempts by continent appears in the graphic below. Please note that attacks from Russia have been classified in the continent of Asia.
Login Attempts by Continent
For more precision about the parts of the world implicated in those attacks, the top 10 countries from where the attacks originated appears below.
Login Attempts by Country (Top 15)
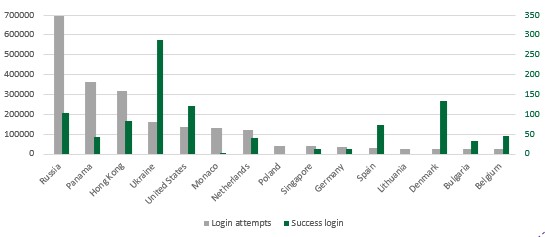
Most attacks come from Russia, Panama, and Hong Kong. This result is similar to other research identifying Russia as the primary origin of attacks on RDP.
If we analyze the countries that successfully broke into our honeypots, we can find that Denmark (for September) and Ukraine (for both months) are the countries with the highest number of successful logins. However, these countries attack a lot. The countries with the highest success rate are Palestine in July (10% successful attacks out of 86) and Romania in September (58.7% successful attacks out of 75). Note that our honeypots’ credentials are intentionally weak, so these results do not reflect an advanced skill-level and are included only as an observation.
Username-related Attacker Strategies
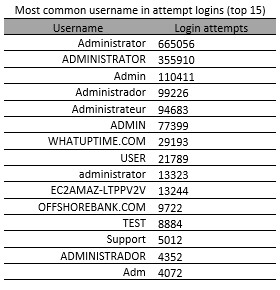
An account with the username Administrator is setup by default on a Windows Server. It’s unsurprising then, that username Administrator is by far the most popular with attackers and was used 665,056 times against our honeypots. It is also noteworthy that ADMINISTRATOR is the username that is most frequently used in attacks from across all countries.
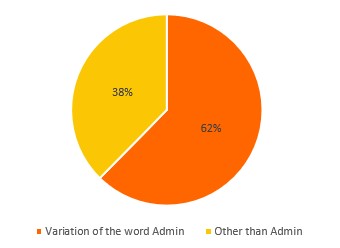
All variation of the word administrator appearing in the graph below represent 62% of all attempts to connect.
Proportion of Usernames Using a Variation of the Word Administrator
Countries Specialization in Username Strategies
When usernames are analyzed in relation with the country of origin of the attack, one can identify specialized strategies utilized by each country.
- OFFSHOREBANK.COM, the domain name in our RDP certificate, is strategically used as a username by attackers from Hong Kong (9445 attacks – 97%) and Russia (277 attacks – 3%).
- The username adm is used exclusively by attackers from Nicaragua (82%) and Panama (18%) in July and, probably because of the absence of attacks coming from Nicaragua in September, this username is used almost exclusively by Panama (46%) and Russia (53%) in that time period.
- Attackers from Hong Kong, Netherland, Panama and Russia tend to be very diversified in the usernames they try. In September, the only variation is that the United States were added to the list of countries with the most diversified username attempts.
- EC2AMAZ-LTPPV2V is the hostname of the honeypot which can be retrieved via nmap using the rdp-ntlm-info script. Connection attempts using this username come from China, Hong Kong and Russia exclusively.
- 75% of attacks using WHATUPTIME.COM as the username come from the Netherlands. Trying this username is a strategy that assumes that the client used the WhatUpTime template to install Microsoft Windows Operating System on a cloud provider that doesn’t support it.
- 67% of attacks using JOKER20047@OUTLOOK.COM as username come from the United States. There is a hacker who offers likes on social media post and dollar credit on Digital Ocean. This email address is given to connect.
Cracking 2.3M Attackers-Supplied Credentials
Our full interaction honeypots consist of our open-source RDP interception tool, PyRDP, in front of Windows Server environments. Since earlier this year, PyRDP supports capture the of Net-NTLMv2 hashes of all connection attempts not only the successful ones. With this in place, we managed to collect more than 8M hashes since the beginning of the year. Of these, we decided to focus our cracking on specific months to avoid wasting too much electricity. We picked a subset of the 2.3M attacker-supplied Net-NTLMv2 credentials from connections that happened in July and September of this year.
Our ethical hacking team assisted us in cracking the hashes with their dedicated hardware. The server holds four RTX A6000 cards and can perform 19 GH/s on Net-NTLMv2, that’s 19 billion password attempts per second! We decided to crack hashes for approximately 6 days, and we used two lists: the ethical hacking team’s best-of-breed and one custom-built for that honeypot, reusing as many words and context as is leaked by our hostname and certificate information and then passed in mangling rules.
Now, we wanted a way to convey just how many attempts would happen over 6 days of cracking at 19 billion attempts per second. That number is huge, 9.8496 × 10^15 to be precise (or 9.8 million billion), but we wanted to provide context in the form of visualization so we could better grasp the sheer vastness of that number. Since this post is about cracking passwords, we thought it appropriate to pick a type of nut of a consistent size. The nutcracker, get it? So, if we add a typical walnut for each password attempt made, we would obtain a certain volume of walnuts – let’s try and visualize how large a volume that would be. For reference, it would be roughly the equivalent of the volume of water in the Manicouagan Reservoir filled with walnuts! The Manicouagan Reservoir is one of the world’s largest, located in Quebec, Canada and is visible from space. It’s worth noting that this reservoir is 4 times larger than the Hover Dam’s Lake Mead reservoir. Put another way, that volume of walnuts is more than 2000 times the combined volume of this list of the world’s largest man-made buildings. That’s a lot of nut-cracking!

“If each password attempt we made was a walnut seed, we would have done enough to fill one of the world’s largest reservoirs, the Manicouagan reservoir located in Canada and visible from space.”
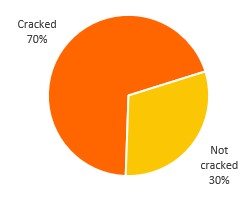
Now onto the results. In July, there were 1,130,770 login attempts. Our team cracked 56.4% of the passwords used in those login attempts. In September, there were 1,217,382 login attempts and our team cracked 69.6% of the hashed passwords. Even though our team used the same hardware and the same techniques as well as the same duration in cracking the hashes from both samples, the results we obtained were very different. As the number of collected hashes is higher in July, we can argue that the set of attempted passwords in July were more complex. The question that emerges from this observation is whether there is a trend in time regarding login attempt strategies.
Total of cracked vs uncracked
passwords for July
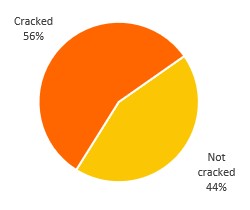
Total of cracked vs uncracked
passwords for September
Password-related Attackers’ Strategies
In the table below, the top 25 passwords used in July and in September are compared because of the significant difference. The top 25 represents 21.3% of the total list of cracked passwords in July compared to 3.6% in September. This shows that September saw significantly more password variations than July.
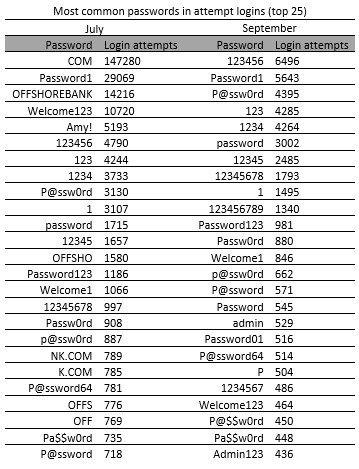
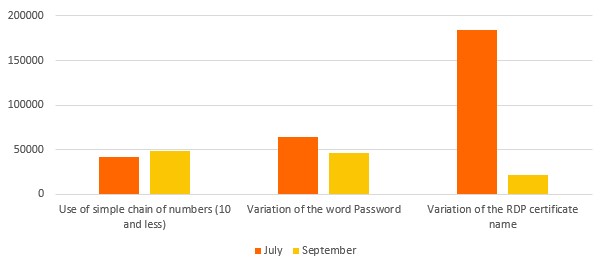
There are 3 distinctive tendencies that can be drawn from the top 25 most common passwords: (1) the use of simple chain of numbers; (2) the variation of the word password and; (3) the variation of the honeypot’s certificate name (offshorebank.com) in July. This last point represents the major difference between both samples: the top 25 most common passwords in July include 7 variations of the certificate name while none were found in September. If the overall samples are considered, there is a 16.3% use of the domain name in password attempts in July and only 1.81% in September. Using information about your target in password-guessing attacks is a well-established tradecraft among offensive security teams and online adversaries. Why was there such a decline between July and September? Additional research is required.
Strategies of Login Attempts Regarding Passwords
Username and Password Combination
The table below shows the top 12 username and password combinations where the password was successfully cracked.
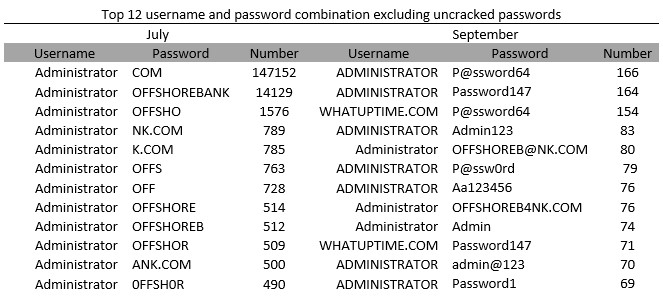
Again, we see that Administrator is the most tried username and that it is tried with many different versions of the certificate name for July and with variations of the word password for September.
Mitigation
The major mitigating insight that emerges from the results is that even if RDP is used by an increasing number of organizations, security around passwords remain of critical importance. Attackers are creative and motivated. They will use a range of strategies to uncover passwords including leveraging the RDP certificate name and computer hostname. Having strong passwords on all usernames is critical and should be considered a baseline requirement.
Based on our penetration testing engagements experience, we know that credential stuffing works best if combined with contextual information about the target (company name, industry-specific words, etc.). Real-life opportunistic attackers seem to follow that advice given the list of the most popular passwords attempted on our systems in July as shared earlier. Add to that the fact the NIST recommends checking for users’ passwords against existing breaches in 2017 a practice that would have prevented almost all attacks against our honeypots from succeeding. Luckily, two approachable alternatives can help mitigate this risk. First, the open-source Lithnet Password Protection for Active Directory (AD) can be deployed on-prem and can block existing compromised passwords and custom words along with an automatically generated list of their common variants. Second, existing Azure AD customers can and should use Azure AD Password Protection in both cloud and on-prem configurations.
Next, choosing a username is equally important in mitigating risk. We observed that default usernames like administrator are the most popular strategies used when attempting to login. Disabling the Administrator account or changing the default username is imperative as it reduces the chances of having the right combination of username-password to get access to your system.
Finally, the results remind us that hackers do not take time off and are constantly adapting their techniques and strategies. Users should be prepared to protect their systems at all times.
The Yet Unsolved Mystery
Both samples were very similar on most aspects except for one: the passwords. There was no variation between the two samples in the use of our certificate name in the username in the attacks. However, the top 25 passwords used in July present 7 variations of our certificate name. None however, appear in the top 25 of the September dataset. In July there were 184,162 passwords containing the certificate name: representing 16.3% of all attempts to connect. In September, there were 22,021 passwords containing the certificate name: representing 1.81% of all attempts to connect. Another important observation is that our team was able to crack a higher number of passwords in September. The same system and the same strategies were used in both cases which indicate that the passwords used to connect in September were less complex than those used in July.
This information leads us to consider whether the attackers changed their strategies, if there were different attackers depending on the period of the year or if we were attacked by different attackers in September. In reality, it’s likely a combination of all three of these factors.
Techniques for using the certificate name and its variations in passwords were significantly higher during the summer. Maybe this strategy is used by more experienced hackers who are more sophisticated and who do not only use popular cracking lists to uncover passwords. It’s possible they are more active during the summer months in order to take advantage of the summertime period during which people are more likely to be away on vacation: creating ideal timing for an attack.
We will continue to investigate this variation of strategies in time and the complexity of passwords in order to better understand the attackers and any patterns we are able to identify. Stay tuned!
We would like to thank William Tremblay, Julien Pineault and Maxime Nadeau for their password cracking assistance and Olivier Bilodeau for additional research and writing.



