
Download the complete Cybersecurity Perceptions Versus Reality report, also available in French.

Download the complete Cybersecurity Perceptions Versus Reality report, also available in French.
Defenders’ Perceived Security Maturity of their Organization
The survey started by asking respondents about their perception on the overall security maturity of their organization. “On a scale from 1 to 5, how mature is the information security of your organization?” As shown in Figure 1, about 24% responded 1 or 2, which is little security maturity, 32% said 3, and 44% said 4 or 5, which represents high security maturity.
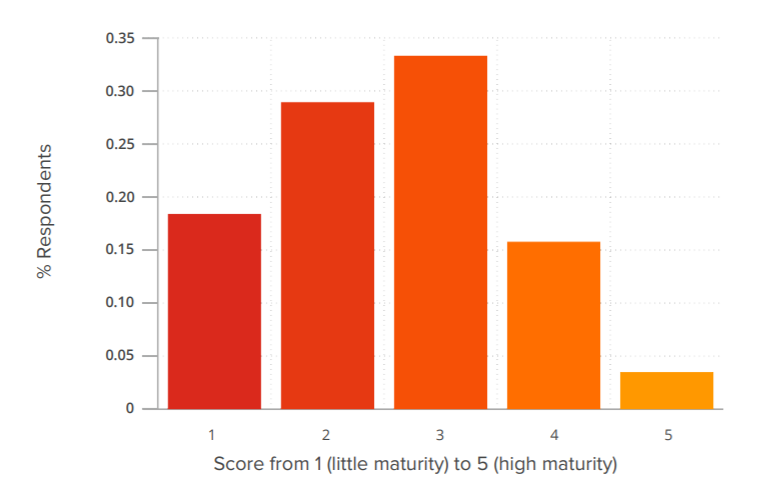
Figure 1 – Respondents’ Perception on the Overall Security Maturity of their Organization
Defenders’ Perceived Security Versus their Implemented Security Measures
The survey inquired about seven security measures, asking respondents if they implemented them in their respective organization. To estimate if respondents’ perceived maturity security of their organization significantly correlated with having implemented these security measures in their respective organization, we computed a statistical model called an Ordinary Least Square (OLS) regression. For curious readers, the model and the results are thoroughly explained in the report’s Appendix.
The model showed that five security measures, reported as implemented, significantly and positively correlate with respondents’ perception of the security maturity of their organization. They are presented in the left column of Table 1. On the other hand, the two measures on the right of Table 1: minimum password requirements and investigating products for features that could represent a risk, are not correlated with participants’ perceived security maturity.
| Significant | Non-Significant |
|
|
Although the model’s results are based on respondents’ perceptions (and do not infer anything about actual security measures being implemented), they indicate that there might be potential biases in the defenders’ mindset. Indeed, why are these two security measures, on the right column of Table 1, not correlating with perceived security maturity? These biases become more obvious once we cross correlate the results with penetration testing data presented below.
Attackers: The Most Common Attack Vectors
We investigated 65 reports on penetration testing (internal, external, and Web applications) and extracted a total of 182 findings. Table 2 presents the top 10 vulnerabilities and/or missing controls ranked from medium to high in severity, found in the reports. We also provided a definition of each of these findings along with pro-tips to overcome them. These ten findings could represent a checklist for any cybersecurity professional wanting to secure the most common attack vectors used by penetration testers. For efficiency purposes, they could be validated and mitigated before purchasing penetration testing services.
Please note that we mixed the different engagement types (internal, external, and Web applications) for the “most common attack vectors” list because the results were interesting. However, we recognize that the presence of NetBIOS/LLMNR and cross-site scripting are two different findings that do not arise from the same context. Future research should focus on a breakdown of the different engagement types.
| Pentest Finding | Definition | Pro-tips |
| 1. Weak password requirements | A weak password is a password that is short, common, a system default, or something that could be rapidly guessed by executing a brute force attack. | Consult pro-tips available in the blog post: The Easy Way in for Attackers: Passwords |
| 2. Corporate Services Using Single-Factor Authentication | Corporate services using single-factor authentication represent a security process that requires either something a user knows, something a user has, or something a user “is” to confirm a user’s identity. The use of a password is the most popular method for single-factor authentication even though users are known to use weak passwords or reuse them across multiple Websites. | Consult pro-tips available in the blog post: Defenders versus Pentesters on Multifactor Authentication |
| 3. Windows credential stored in memory | This finding is related to several Windows authentication protocols that involve sending the user’s password to the target machine. Several of these protocols are enabled by default and store users and service credentials in restricted memory zones, under the protection of the SYSTEM account. That information can be retrieved in clear text using local administrative privileges. |
|
| 4. Password reuse | This finding is related to situations where multiple workstations share the same local user and password combination allowing lateral movement through re-use. It is also common to observe domain users sharing the same passwords. |
|
| 5. NetBIOS/LLMNR protocols | These obsolete protocols are typically used in the process of resolving hostnames as multicast but offer no authentication mechanism. This makes them vulnerable to multiple identity theft attacks at the network level. | Consult pro-tips available in the previous blog: The Easy Way In: Products’ Features Vulnerable by Default! |
| 6. Inadequate vulnerability management process | This finding refers to the cyclical practice of identifying, classifying, and remediating or mitigating vulnerabilities, especially in software and firmware. Vulnerability management programs are considered inadequate when many systems in production are missing security patches or are running on vulnerable software versions | Consult pro-tips available in the previous blog post: Patch Management: A Cybersecurity Priority Yet to be Fully Implemented |
| 7. No HTTP Strict Transport Security (HSTS) | HSTS is a security feature implemented in browsers to locally store the digital certificate of visited HTTPS Websites and map them to their respective domain name. Each subsequent visit to a protected Website is redirected automatically to HTTPS and triggers a validation of the certificate presented by the Web server against the one that was previously stored. If the certificates do not match, the browser will restrict access to the Website, as it is detecting ongoing malicious activity. Browsers will only use this feature if a Website sends the HSTS HTTP header. |
|
| 8. Domain controllers or servers with Internet access | This finding means that the domain controllers and servers hosted on the corporate network had access to the Internet. Current security standards and best practices advise against this. |
|
| 9. Cross-Site Scripting | An application is vulnerable to Cross-Site Scripting (XSS) when user input is reused as-is in the response page. |
|
| 10. Inadequate storage of sensitive information | This finding refers to the methods used to safeguard sensitive information, such as personal information about customers or employees, passwords, banking information, or any information likely to cause harm if known to a malicious individual. Storing this information in plain text in a document, on a workstation, or on a network share is a risky practice. |
|
Asymmetrical Information between Attackers and Defenders
What is striking from the results presented above is that the two security measures that are not associated with respondents’ perception of the security maturity of their organization are related to major vectors of attacks found in penetration testing reports. These two security measures are meeting minimum password requirements and product investigation for features vulnerable by default. The major vectors related to them and found in penetration tests are weak password requirements, password reuse, windows credentials stored in memory, and presence of NetBIOS/LLMNR. Indeed, when minimum password requirements are not met, penetration testers can leverage weak passwords, through attacks like password spraying or brute force, to enter a network. Worse, if multiple workstations share the same credentials, testers may leverage this password reuse to compromise new devices and move through the network undetected.
Moreover, Windows password stored in memory and presence of NetBIOS/LLMNR are two features enabled by default on Windows that represent a vulnerability. These features are exploited by penetration testers all the time. Investigating products for features vulnerable by default should become a priority for information security professionals as even the most robust firewall cannot mitigate this, leaving the organization at high risk.
Conclusion
Overall, we find that there is asymmetrical information between ethical attackers and defenders: the security features that are not found to be related to cybersecurity professionals’ sense of security are part of the attack techniques most often used by ethical attackers to break systems. These findings illustrate that, although there are real efforts in the industry to protect systems, there is still a lot of information that is not yet processed and accounted for by defenders. These misaligned perceptions need to be rectified and, by doing so, it is also likely that real attackers would be defeated more often.
These findings are part of the Cybersecurity Perceptions Versus Reality report that highlights the key results of a two-year long study that aimed at understanding a disconnect that exists between how defenders perceive the value of their implemented security controls, and the most common attack vectors leveraged by penetration testers acting as potential attackers. The report is available in French and the microdata of the survey is available online.


