Having an asset inventory is a common security practice. Yet, keeping that inventory up to date seems to be less common. GoSecure penetration testers report encountering unmaintained asset inventories quite often, allowing them to exploit forgotten servers hosting known vulnerabilities. This blog post highlights findings related to asset inventory maintenance uncovered through our research on Cybersecurity Perceptions Versus Reality.


Having an asset inventory is a common security practice. Yet, keeping that inventory up to date seems to be less common. GoSecure penetration testers report encountering unmaintained asset inventories quite often, allowing them to exploit forgotten servers hosting known vulnerabilities. This blog post highlights findings related to asset inventory maintenance uncovered through our research on Cybersecurity Perceptions Versus Reality.
Download the complete Cybersecurity Perceptions Versus Reality report, also available in French.
Defenders: Asset Inventory Matters
Respondents were asked whether they maintained a complete inventory of their external assets (IP addresses and domains) and internal ones (IP addresses, servers, and domains). As shown in Figure 1, most respondents (77.1%) said that they kept a complete inventory of their assets, while 17.8% said no, and 5.08% did not know. While it is very encouraging to find so many organizations maintaining an asset inventory, it is the accuracy of said inventory that comes into question during a penetration test.
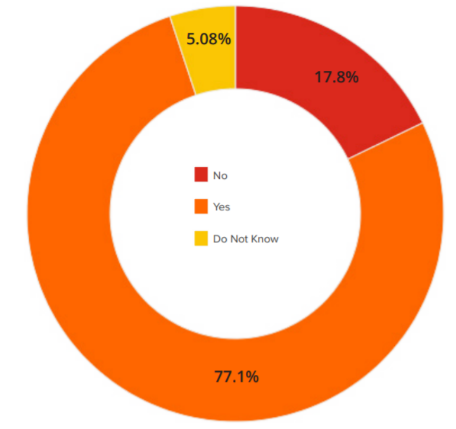
Figure 1 – Asset Inventory
Pentesters’ Experience: The Hard Task is Updating Asset Inventories
Overall, GoSecure pentesters mentioned that most companies have an asset inventory. However, the inventory is, most of the time, in an unknown state or not entirely up to date. During penetration tests, for example, pentesters have leveraged forgotten and unmaintained servers to enter a company’s network. They even mentioned stealing laptops during red team engagements (security tests that allow physical access as well) and most of the time, the employees did not notice that a device was missing!
Pro Tips on Asset Inventory
As a reference for readers, below are some pro-tips related to maintaining an up to date asset inventory on corporate networks.
- Ensure that your current IT asset inventory is updated and there is a process to maintain it. The NIST has extensive resources on the topic.
- Consider using offensive security tools to assess your asset inventory. Open source tools like BloodHound (this presentation at DerbyCon explains how to use this tool as a blue team expert) or ADRecon will allow you to have the “attacker’s view” of your assets. This can change the IT team’s view of assets, while potentially uncover assets that were not in the formal inventory.
- In the long term, establish a comprehensive strategy for the management of assets throughout their life cycle as the basis of other security processes such as risk management, patch management, and disaster recovery.
Conclusion
These findings are part of the Cybersecurity Perceptions Versus Reality report that highlights the key results of a two-year long study that aimed at understanding a disconnect that exists between how defenders perceive the value of their implemented security controls, and the most common attack vectors leveraged by penetration testers acting as potential attackers. The report is available in French and the microdata of the survey is available online.



