Download the complete Cybersecurity Perceptions Versus Reality report, also available in French.
Defenders: Importance versus Implementation
Interestingly, we noticed two trends in the data regarding regular password changes: 43.7% agreed that regular password changes (such as every 90 days) should be a minimum requirement while another 43.7% of respondents said the opposite: no or few password changes (once or twice a year or at the suspected compromise of passwords) should be the minimum requirement. Some people also selected both options.
This discrepancy in the results can be explained by the idea that mandated password change is a double-edged sword: it can mitigate a potentially compromised password, but also seems to be disliked by users, who end up finding simpler passwords or incrementing a number to their previous passwords to bypass this security policy. “Human acceptance” of a security feature is essential for it to be efficient: if end users do not like the security controls, they will always find a way to bypass it. Below you will find a good -and unfortunately true- story, told by one of our pentesters, on how a user had bypassed a password security feature:
“The password policy was preventing users from setting passwords that were used previously. Any of the last 6 passwords were blocked. To circumvent this policy, users could change their passwords six times in a row (within a short time window) and get back to their favorite password. One person did this every three months so that the password would always be the name of his/her cat.”
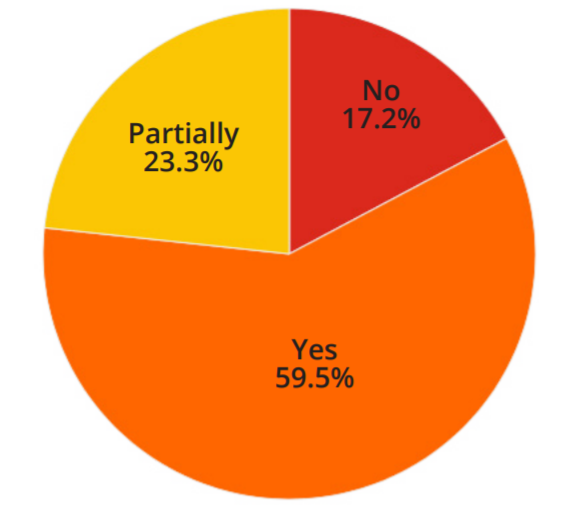
Figure 1 Organization meeting password minimum
Pentesters’ Experience : Passwords are the Weakest Link
Penetration testers often use two techniques to compromise systems with passwords: password spraying and password cracking. Password spraying consists of trying a popular password on a large number of accounts and finding the weakest link: the account with THE guessable password. Generally, when conducting such attacks, pentesters have a list of “all-star passwords”. This list includes simple passwords like Password123, Welcome1, Letmein1, SeasonYear, and Companyname123. When conducting password spraying on companies, pentesters reported being successful, on average, 25% of the time. Password cracking, on the other hand, requires that pentesters have access to a list of encoded/hashed passwords (possible through various attacks such as LLMNR spoofing) and try to find the plain text password by encoding/hashing a known list of passwords and testing them against the compromised list. In such situation, pentesters find, 20% of the time, passwords with name and four numbers, such as Julia1984, 4-5% of the time, passwords with vulgar words (you can probably guess examples) and 4-5% of the time passwords with vacation words in them, such as BeachCuba1. When performing password cracking, pentesters have reported being successful in finding at least one password most of the time.

Pro Tips on Good Password Enforcement Practices
As a reference for readers, we provide some pro-tips below related to enforcing good password policies on corporate networks.
- Block any words related to the company (with a password filter, for example), even though special characters or numbers are added to the password. If needed, you can use Microsoft’s password filter feature.
- Communicate to employees that passwords should not be related to information publicly available about them online on social networks, such as Facebook, LinkedIn, or Instagram. Pentesters often use such information when conducting external tests.
- When a security incident happens or an external person gets access to the active directory user database, enforce password changes on the whole network, including service accounts and most importantly, the krbtgt account, the most powerful service account in the active directory.
- Consider continuous password auditing activities to proactively track any potential weak passwords. For example, periodically extracting the user database, trying to crack their password hashes, and forcing password changes for all the successfully cracked hashes is an effective additional practice.
Conclusion
These findings are part of the Cybersecurity Perceptions Versus Reality report that highlights the key results of a two-year long study that aimed at understanding a disconnect that exists between how defenders perceive the value of their implemented security controls, and the most common attack vectors leveraged by penetration testers acting as potential attackers. The report is available in French and the microdata of the survey is available online.



