It should come as no surprise that cybercriminals are using the COVID-19 pandemic as a phishing lure. Popular media events always result in new attacks. But with the heightened level of awareness (panic?), end-users are likely more susceptible than usual. GoSecure Inbox Detection and Response (IDR) has blocked several new variants, each with varying levels of complexity to the phishing lure but almost all looking to install a remote access trojan. As remote access trojans (RAT) are known for many nefarious activities (log keystrokes, access the camera, steal credentials stored in browsers, open a reverse shell, upload/download files, view the vi desktop, perform process, file, and registry manipulations and more), it’s unknown what the endgame is, but it’s safe to assume it’s nothing good.
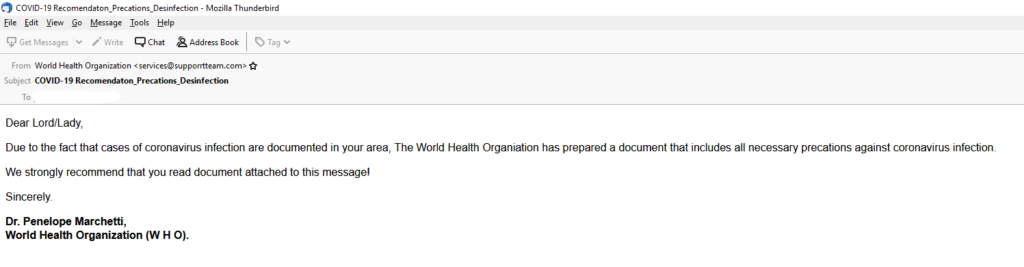
In this example, and a commonly used tactic in COVID-19 attacks, the phishing lure purports to come from the World Health Organization (WHO). This one is exceedingly simple in its design, including the continually infamous use of misspellings and poor English grammar.
And, no, Dr. Penelope Marchetti does not appear to be a real person.
Attached to the email is a macro-enabled Microsoft Excel add-in file, COVID-19 Recomendaton_Precaution_Desinfection.xlam (note misspelling of disinfection). By default, Microsoft Outlook is cautious about opening attachments, but other email clients are not as diligent. And most users are unlikely to note the XLAM extension, which they rarely ever see.
Once opened, the XLAM attachment connects to a dynamic web site via dynamic DNS duckdns.org. This technique allows the attacker to change the location of the malicious download, thus allowing the campaign to have a longer life. Once connected, the malicious website delivers njRAT, a remote access trojan first observed in 2012. Many variants of njRAT have been created since it’s initial observation. More in-depth analysis by GoSecure indicates this version is the BLADABINDI variant. Even amongst BLADABINDI there are multiple variants as the underlying RAT has a myriad of capabilities. It’s BLADABINDI’s customizability and seeming availability in the underground that makes it a prevalent threat.
Digging into the mechanics of sending this email, the sending domain of supporrtteam.com reuses the misspelling technique, knowing that most end users won’t notice. Bigger question should be why the WHO is sending email from a non-related domain? Here again, with all the media attention surrounding COVID-19, most users won’t notice or ask. Also, the sending domain does not resolve via a DNS lookup, always an indicator of suspicion.
The use of COVID-19 phishing lures will continue until they are no longer effective. This is just one example that GoSecure has seen, and we will report on others as we have the details. Please consider the mitigation actions noted below to protect your organization immediately. GoSecure Inbox Detection and Response will also protect your users from wherever they view the email.
Mitigation Actions
- Block DNS lookups to duckdns.org
- This may impact legitimate DNS lookups
- Block incoming email from supporrtteam.com
- Prevent all email clients from opening XLAM attachments