TL;DR
We are announcing the first “official” release of malboxes, a tool meant to help build safe and featureful Windows machines for malware analysis. Accessible to anyone, it even uses trial versions of Windows if one doesn’t have his own license.
Cut the Red or the Blue Wire?
When performing malware analysis one must be careful to avoid infecting one’s machine or triggering a trap door inside the malware. Consequences can vary from the leak of internal information, products or licenses, to the identification of an organization’s IP addresses all the way to wiping the infected computer. This is the reason why malware analysis needs to be done in isolated physical or virtual machines.
Configuring such a virtual machine takes a while and when someone has built one, they tend to add tools to it, update it and stick to it. Copy and paste of disk images and snapshots are then usually used before starting a new analysis. A whole chapter in the reference book on malware analysis – Practical Malware Analysis – is dedicated to the topic of setting up a Virtual Machine in a safe way. Automating and speeding up this process would be the natural evolution of this practice.
Leveraging the DevOps Ecosystem
A few years ago, based on a successful experience using Vagrant to manage development environments, we decided to look at the options to manage Windows virtual machines. Unfortunately, at the time Vagrant didn’t natively support Windows guests and so we moved on. A year ago, we re-evaluated the possibility and it turned out that it is now possible thanks to Microsoft and its maturing DevOps ecosystem.
However, one problem faced using Vagrant and Packer directly is that the Windows-specific configuration required is non-obvious. Instead of building our own complex configuration files and invoke Packer or Vagrant directly we decided to do an abstraction layer focused for people interested in malware analysis and thus is born malboxes.
Introducing Malboxes
There is nothing like a demo to understand the amount of work that is saved by using this tool:
What can be seen here is that by using two simple commands (build and spin) malboxes built a Windows 10 Enterprise Evaluation virtual machine (VM) template and then launched a copy of it with the current folder shared on the Desktop of the VM.
The following tools are installed as part of the build process:
- windbg
- The whole sysinternal suite
- Fiddler
- Wireshark with npcap (a Windows 10 compatible winpcap replacement)
- IDA Pro remote debuggers (if IDA Pro is installed on the host)
The following changes are made to the guest operating system:
- Disables automatic updates
- Disables Windows Defender
Doing all of this by hand might take half a day but with malboxes it’s a matter of minutes.
Getting One’s Hands Dirty
Once installed, the tool is meant to be used on the command-line.
To list supported profiles:
$ malboxes list
supported profiles<span class="token punctuation">:</span>
win10_32_analyst
win10_64_analyst
win7_32_analystTo build a Windows 10 64-bit analysis machine:
malboxes build win10_64_analystOnce that process is done, a vagrant box is imported. From there, that base box can be re-used as much as needed for individual analysis tasks. For example, let’s say one analyzes a sample of Sirefef. It’s only a matter of generating the proper vagrant config referring to this base box. malboxes provides a convenient wrapper to generate the proper Vagrantfile:
$ mkdir Win32<span class="token punctuation">.</span>Sirefef<span class="token punctuation">.</span><span class="token constant">EV</span><span class="token operator">/</span>
$ cd Win32<span class="token punctuation">.</span>Sirefef<span class="token punctuation">.</span><span class="token constant">EV</span><span class="token operator">/</span>
$ malboxes spin win10_64_analyst Win32<span class="token punctuation">.</span>Sirefef<span class="token punctuation">.</span><span class="token constant">EV</span>
Creating a Vagrantfile
Vagrantfile generated<span class="token punctuation">.</span> You can move it <span class="token keyword">in</span> your analysis directory and issue a <span class="token template-string"><span class="token string">`vagrant up`</span></span> to <span class="token keyword">get</span> started <span class="token keyword">with</span> your <span class="token constant">VM</span><span class="token punctuation">.</span>
$ vagrant upThe analysis VM is now ready!
Malboxes’ Architecture
In a nutshell, malboxes wraps together:
- A packer configuration
- Windows unattended installation configuration
- PowerShell recipes to disable security features (Defender, auto-updates, firewall, etc.)
- A set of malware analysis focused tools installed using the Windows package manager chocolatey
- A Vagrantfile generator so that the VMs can be managed with Vagrant
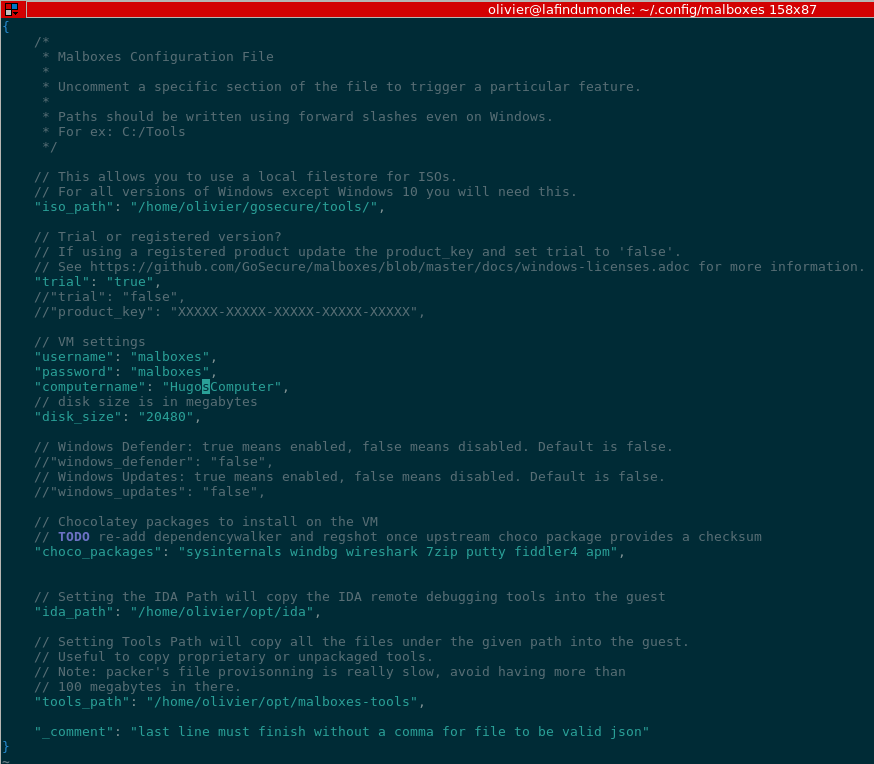 Malboxes Configuration Example
Malboxes Configuration Example
Benefits of this architecture include leveraging chocolatey packages. This means one can install anything available in the extensive chocolatey package gallery with a single command. The default list of packages installed can be modified in malboxes’ configuration file. Additionally, packaging for chocolatey is straightforward so there is a huge network effect around chocolatey right now which we benefit from.
Another benefit is that malboxes, packer, vagrant and the PowerShell scripts all stay out of the guest. There is no custom guest agent on the VM and we have plans for further automated cloaking and multiple hypervisor support.
Malboxes is built in Python 3 and supports the following host operating systems:
- Windows
- MacOS
- Linux
The Future
We will cover more use cases in upcoming blog posts, namely:
- A team analysis workflow where an investigation is shared among analysts
- Ways to automatically customize the VM in order to use it as a honeypot VM for a specific threat
We invite anyone interested in contributing but who doesn’t know where to start to look at our TODO file, located in the repository. Ideas and issues are also welcome, of course.
We believe there are more people working in IT Security than malware authors. However, malware analysis is still considered an art reserved to a skilled few. With our tool, we hope to make malware analysis more accessible by providing easy to build, batteries included, virtual machines. With this tool and others like the Cuckoo sandbox, more IT Security professionals or students eager to learn will be able to look at suspicious binary files and inspect them manually and safely.
Special thanks to Hugo Genesse for his help on this blog post.
 Malware analysis is like defusing bombs. The objective is to disassemble and understand a program that was built to do harm or spy on computer users (oops, this is where the bomb analogy fails, but one gets the point). That program is often obfuscated (ie: packed) to make the analysis more complex and sometimes dangerous. This blog post introduces a tool that we have built that creates Windows Virtual Machines (VMs) without any user interaction. Those VMs are preconfigured with malware analysis tools and security settings tailored for malware analysis. We will then explore how to use the tool, its architecture and where we want to take it.
Malware analysis is like defusing bombs. The objective is to disassemble and understand a program that was built to do harm or spy on computer users (oops, this is where the bomb analogy fails, but one gets the point). That program is often obfuscated (ie: packed) to make the analysis more complex and sometimes dangerous. This blog post introduces a tool that we have built that creates Windows Virtual Machines (VMs) without any user interaction. Those VMs are preconfigured with malware analysis tools and security settings tailored for malware analysis. We will then explore how to use the tool, its architecture and where we want to take it.


