During the holiday season, it is estimated that 800M packages are shipped via USPS between Thanksgiving and Christmas. Given these types of numbers, is it any wonder why scammers want to capitalize? With so many people expecting packages, a phishing attempt could easily work against an unsuspecting victim.
In one recent campaign identified by GoSecure Email Security Analysts, GoSecure Secure Email Gateway blocked almost a million phishing attempts against GoSecure clients. Here are a couple examples of recent attempts and how you can spot the scams.
Example #1: Maldoc Phishing Attempt
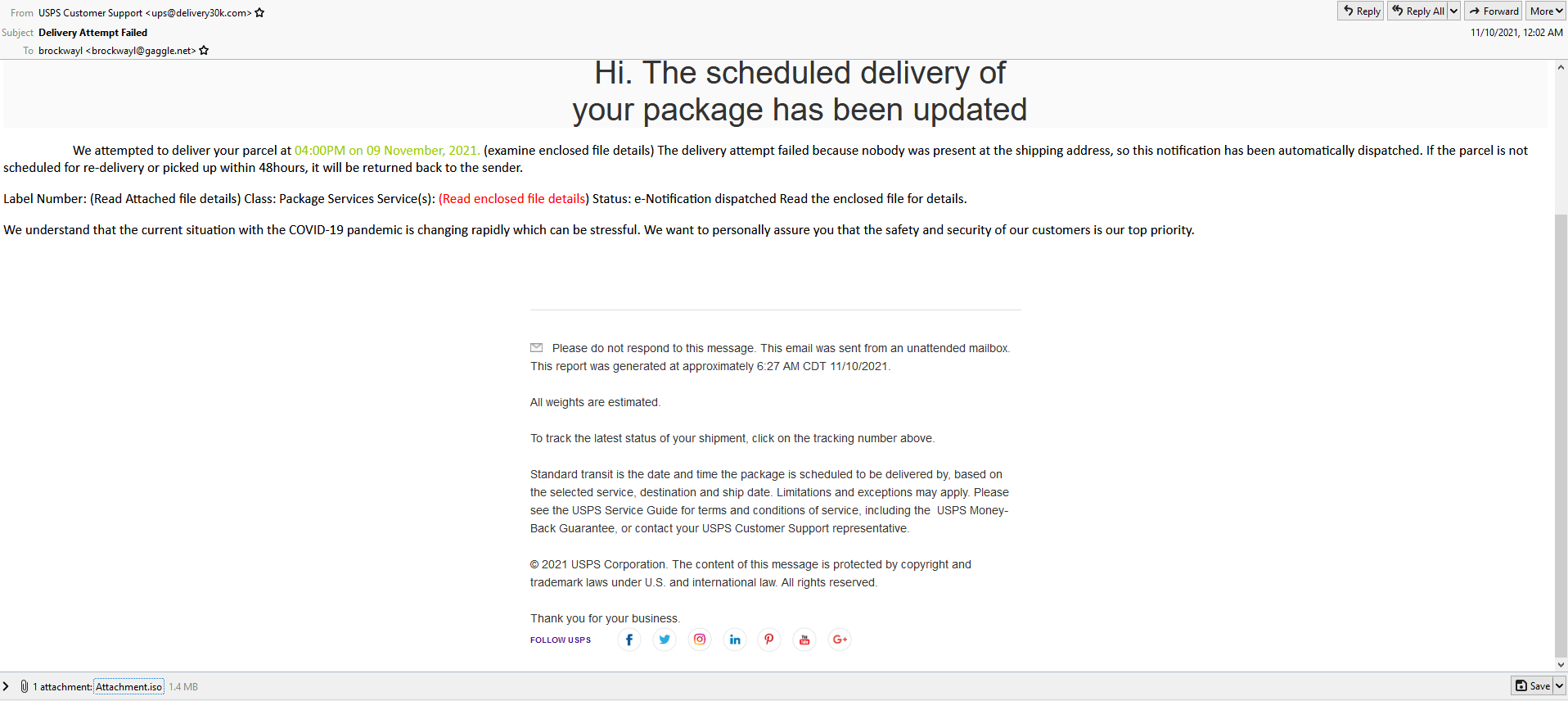
The first example below is a maldoc attempt. Here, the email seems to be indicating that the receiver has a package on the way but it was not able to be delivered.
The attached .iso file is an archive file which contains a file titled Delivery Pdf Doc.exe – this file when tested appears to reach out to hxxps://fetiqa[.]bl.files[.]1drv[.]com/ in order to download a malicious payload. The download site appears dead as of now so we are not sure what the payloads intention was, but rest assured, it was nothing good.
This type of maldoc is called a Trojan Downloader–the malicious payload is not attached to the email itself.
- It is important to note on any email the entire FROM header: “usps customer support” <ups@delivery30k.com> – delivery30k.com is not a legitimate domain name, any notification like this should come directly from a retailer where an item was purchased or from a legitimate delivery service such as usps.com, ups.com, dhl.com, etc.
- Any attachment to an email of this sort would be a .pdf file and nothing else. If you see any other type of file extension, there is cause for suspicion and it should not be downloaded or opened. If it is a .pdf file it should contain all of the information you need, if it is a link to somewhere else then DO NOT CLICK.
Example #2: Phishing Email with Phony Link
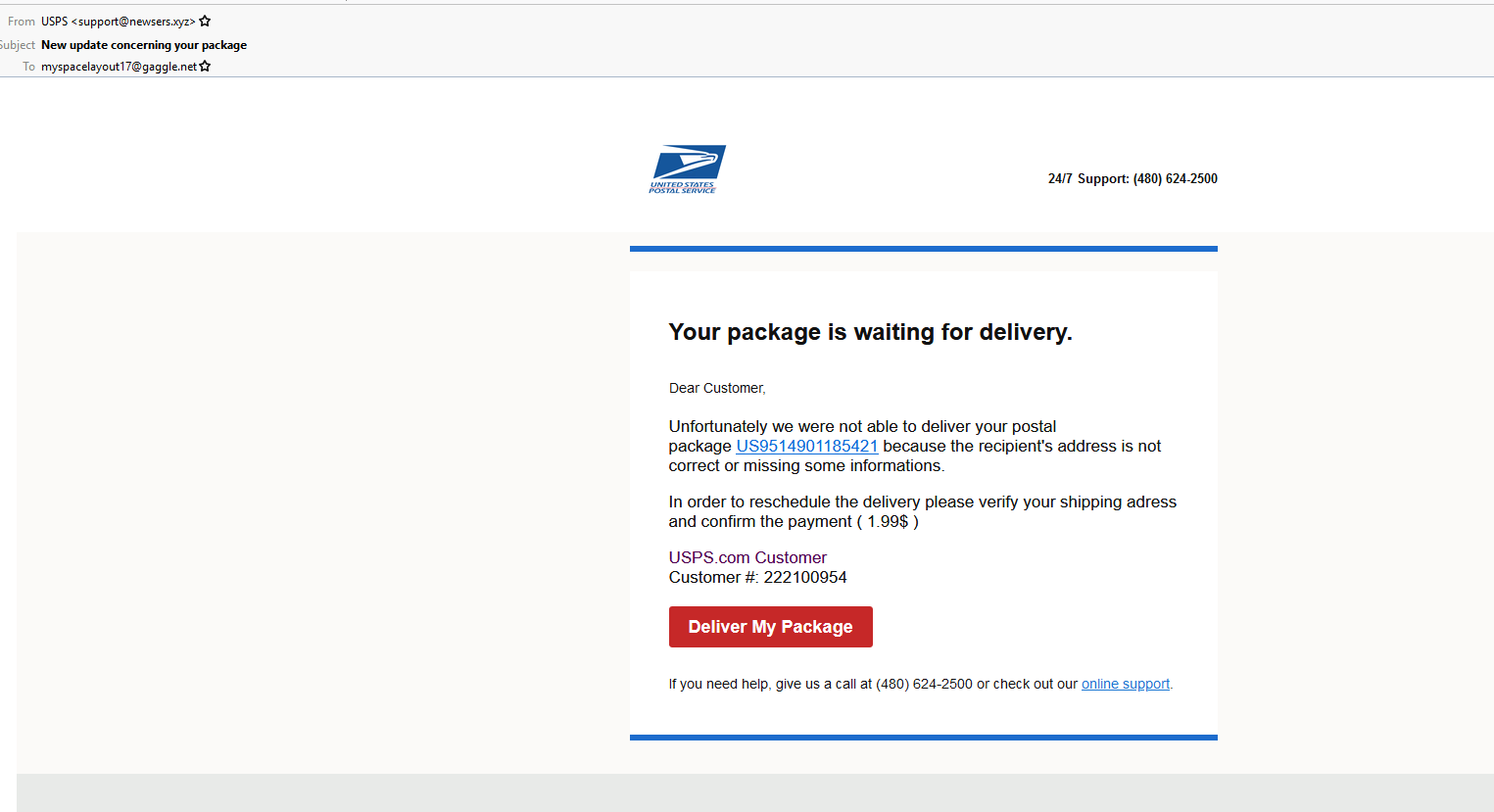
This example is a phishing attempt, where the scammer is trying to get the user to click on the link below to share personal information.
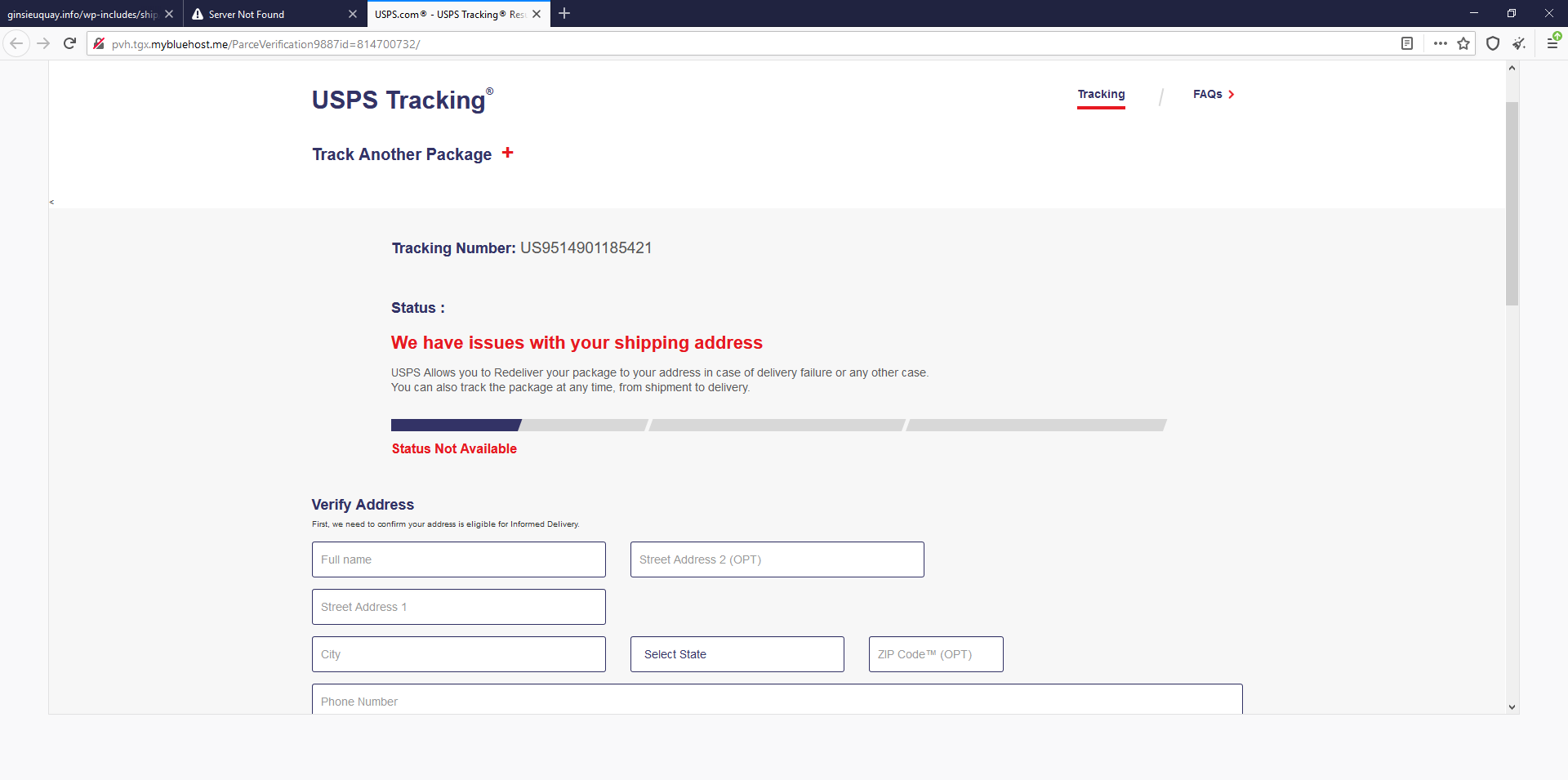
In this case the “Deliver My Package” link went to a USPS branded website:
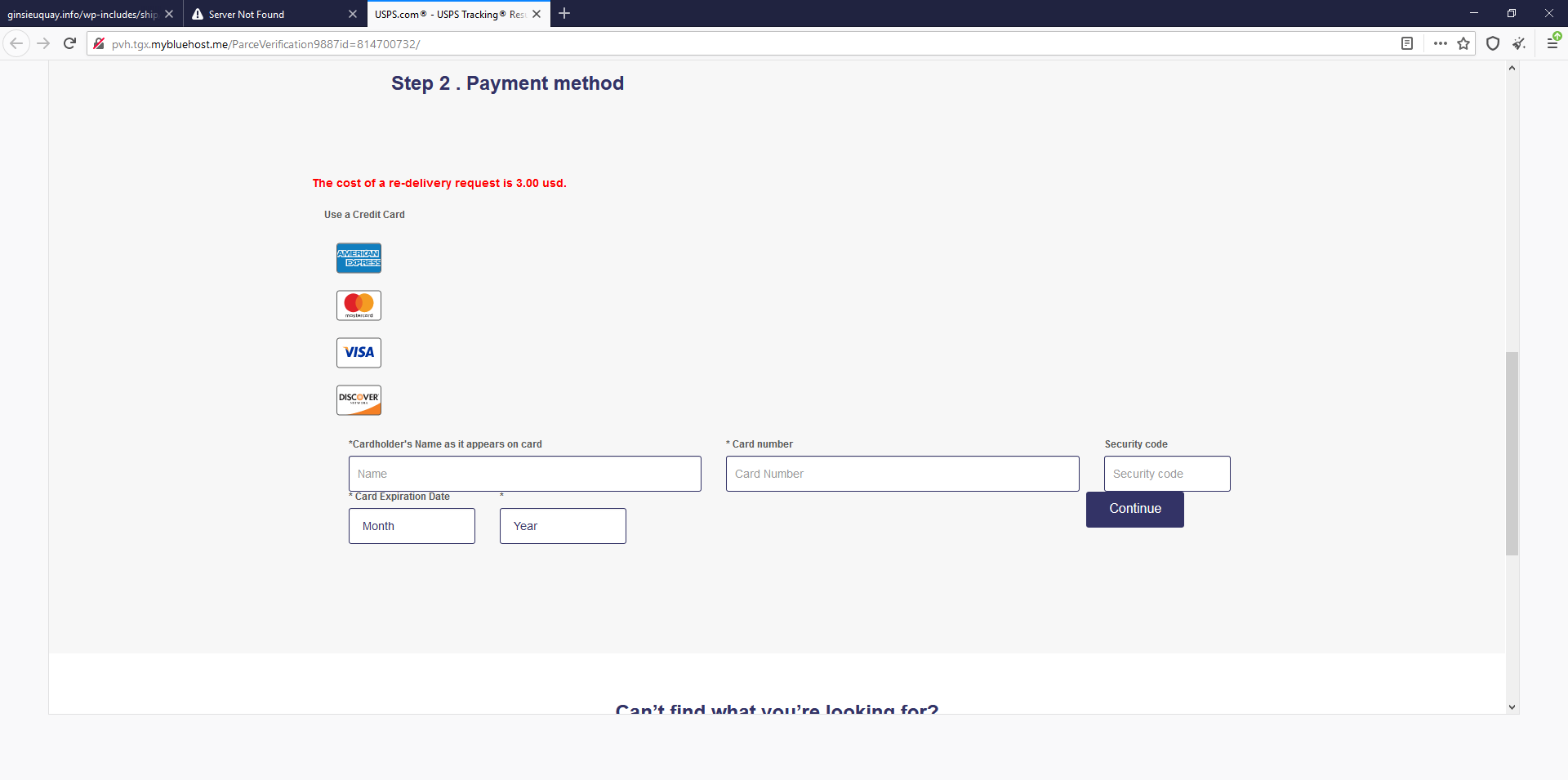
As you can see in the original email there is a supposed $1.99 re-delivery fee. So, the scammer is trying to not only get your personal information, but to steal your credit card information as well.
- On any email, check the FROM header. In this case the entire: usps <support@xxxsers.xyz>- xxxsers.xyz is not a legitimate domain name.
- Any notification like this should come directly from a retailer where an item was purchased or from a legitimate delivery service such as usps.com, ups.com, dhl.com, etc.
- It is also important to realize that USPS or other big delivery services DO NOT CHARGE for re-delivery.
- Be sure check the tracking number given on the original email to ensure it is a valid delivery.
Summary
The key to protecting yourself and your users this holiday season is awareness. At GoSecure, we offer an extra layer of support with our GoSecure Titan Inbox Detection & Response (IDR) service which allows users to easily send suspicious email for professional evaluation right from the inbox. With the quantity of these scams, security teams are swamped trying to keep up with the volume of questionable emails from both email security filters and employee submissions. GoSecure IDR can help take away that burden. The IDR tool combines machine learning with our experienced analysts to review the email submitted and either return those messages that are safe or remove them from the entire domain if they are malicious.
To learn more about GoSecure Titan IDR, check out this webpage. And be sure to follow us on Twitter and LinkedIn for more investigations and cybersecurity news.