Are things better? Undeniably. Can they be better still? Without question. But as long as the tech/people cycle continues, most organizations will never reach their cybersecurity goals because the goal will always be just out of reach by one person or one technology. To illustrate this, we’ll use the recent Exorcist 2.0 ransomware.
The Exorcist ransomware first appeared earlier in 2020. While not unheard of, it was still fascinating to find such a quick iteration to Exorcist 2.0 within only a couple of months. Quickly iterating malware tactics is commonplace for adversaries as it allows them to stay ahead of technique-based cybersecurity solutions. Think of traditional antivirus and its signature-based detections. Signatures are, in essence, a collection of tactics and techniques. Use a new technique, and it’s easy to bypass traditional antivirus. Next-Generation Antivirus attempts to address this limitation by adding automated analysis and correlation (i.e., machine learning) but, in reality, is only marginally more effective than traditional antivirus.
Now consider a behavior-based approach. Rather than relying on a relatively binary decision (is it known to be good or bad?), a behavior-based approach looks at the full sequence of events. Adversaries frequently change tactics, but the goal behind the tactics are universal – compromise an endpoint, move laterally, steal credentials, etc. So, when the GoSecure Active Response Center (ARC) saw familiar, yet slightly different, behaviors in late September, they knew something was up.
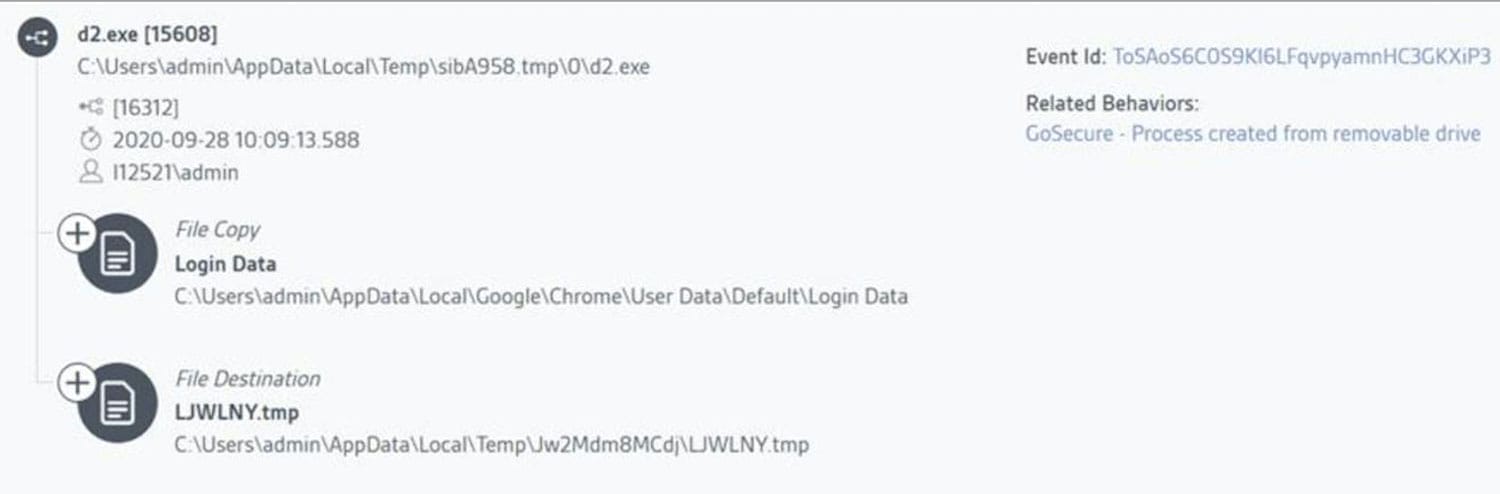
Running setup_install.exe is not, in itself, unusual, although the file name is suspicious. And a setup file creating several temp files is standard. But when the temp files start copying data from the installed browser’s directory into random text files, the game is afoot. Keep in mind, however, that none of this activity (so far) is known malicious. It has taken a behavior-based approach, combined with human review, to generate a level of suspicion. Even at this early stage, the GoSecure ARC is on high alert.
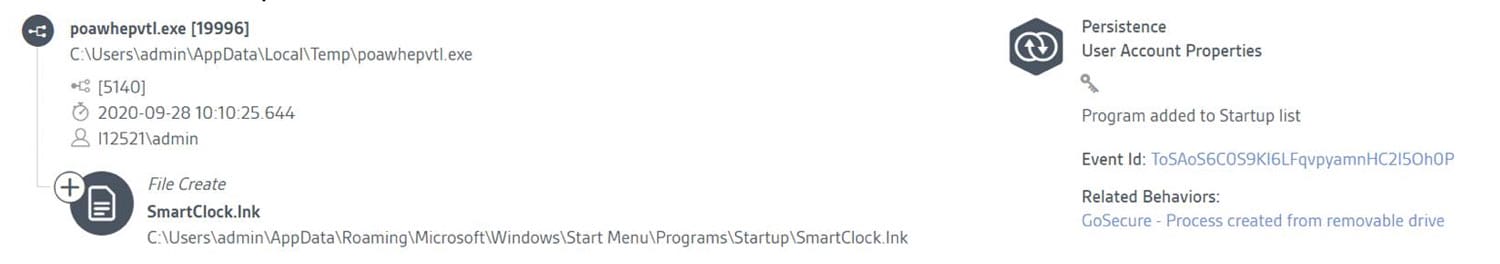
What follows are many actions not entirely unrelated to safe installer activities (delete temp files, install new files, create processes, etc.). But analyzed very closely, as the GoSecure ARC does every day, these actions are increasingly suspicious (create file oewvcabkhaw.exe, create a new process using this file, create more suspiciously named files such as poawhepvtl.exe). The coup de grâce comes when a malicious shortcut link, SmartClock.lnk, is added to the user’s startup folder. This shortcut links to a file that is activated using a Registry RunOnce entry, which is, subsequently, deleted.