Blogue GoSecure
Understanding the Microsoft Outage BSOD Incident: Navigating Security Challenges with GoSecure
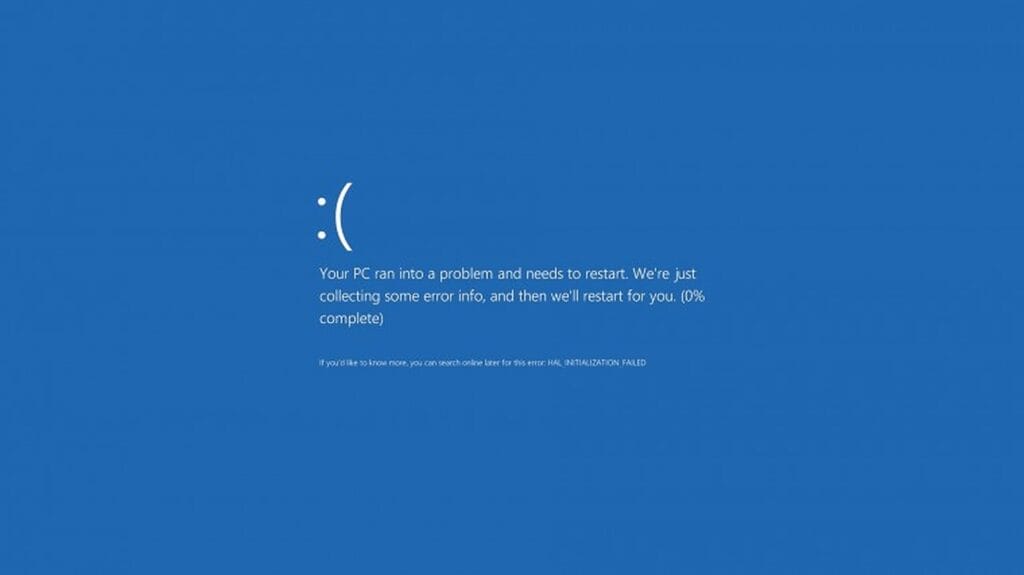 Today, reports detailing a Blue Screen of Death (BSOD) issue impacting Microsoft systems with CrowdStrike’s Falcon sensor installed has had worldwide implications and outages. The BSOD issue arose following an update to the CrowdStrike Falcon sensor. This malfunction caused affected systems to crash, presenting a blue screen error, a situation that can disrupt business operations and compromise security by leaving systems unprotected.
Today, reports detailing a Blue Screen of Death (BSOD) issue impacting Microsoft systems with CrowdStrike’s Falcon sensor installed has had worldwide implications and outages. The BSOD issue arose following an update to the CrowdStrike Falcon sensor. This malfunction caused affected systems to crash, presenting a blue screen error, a situation that can disrupt business operations and compromise security by leaving systems unprotected.
Malicious Hacker’s Command Line Proficiency Level
 As part of my 15-week internship within the GoSecure research team, I was given the opportunity to work on Remote Desktop Protocol (RDP) attacks. I was tasked with the codification of attackers’ behavior in RDP recorded sessions. During this part of the research, I developed an interest in the use of Command Line Interface (CLI) by attackers.
As part of my 15-week internship within the GoSecure research team, I was given the opportunity to work on Remote Desktop Protocol (RDP) attacks. I was tasked with the codification of attackers’ behavior in RDP recorded sessions. During this part of the research, I developed an interest in the use of Command Line Interface (CLI) by attackers.
In this blog, I will present my findings concerning CLI use, what my expectations were and how my perception has changed since doing this research.
Navigating the RDP security consequences of TLS vs. NLA from a threat exposure perspective
 Discover the evolving Remote Desktop Protocol (RDP) security environment through our insightful exploration of using Network Level Authentication (NLA) rather than keeping the basic Transport Layer Security (TLS) only. Join users, organizations, and researchers in navigating the dynamic cybersecurity landscape, contributing to a safer digital future.
Discover the evolving Remote Desktop Protocol (RDP) security environment through our insightful exploration of using Network Level Authentication (NLA) rather than keeping the basic Transport Layer Security (TLS) only. Join users, organizations, and researchers in navigating the dynamic cybersecurity landscape, contributing to a safer digital future.
North Korean Actors Exploit Weak DMARC – Security Policies to Mask Spearphishing Efforts
 A recent FBI advisory unveils a chilling narrative: North Korean state actors, exploited weak DMARC security policies to mask their spearphishing campaigns. Such revelations underscore the critical need for robust defense mechanisms. GoSecure Titan® Email Security, which bundles GoSecure Titan® Secure Email Gateway (SEG) and GoSecure Titan® Incident Detection and Response (IDR) is not merely a tool; it’s a bastion of digital safety, meticulously designed to counteract these tactics. As the machinations of these actors unfold, our solutions stand ready, turning potential vulnerabilities into fortified defenses.
A recent FBI advisory unveils a chilling narrative: North Korean state actors, exploited weak DMARC security policies to mask their spearphishing campaigns. Such revelations underscore the critical need for robust defense mechanisms. GoSecure Titan® Email Security, which bundles GoSecure Titan® Secure Email Gateway (SEG) and GoSecure Titan® Incident Detection and Response (IDR) is not merely a tool; it’s a bastion of digital safety, meticulously designed to counteract these tactics. As the machinations of these actors unfold, our solutions stand ready, turning potential vulnerabilities into fortified defenses.
Maximizing Employee Protection by Rethinking Expectations of Phishing Awareness and Email Security
 Blaming users for falling victim to phishing emails overlooks the unrealistic expectation for every employee to be a cybersecurity expert. In this blog post, we explore the diminishing effectiveness of phishing awareness programs over time and the financial complexities of implementing such employee cybersecurity training programs. We also discuss solutions that empowers users to obtain real-time email analysis by a human expert with just a single click. A potentially ideal solution to offer efficient protection against email threats without burdening IT teams or users.
Blaming users for falling victim to phishing emails overlooks the unrealistic expectation for every employee to be a cybersecurity expert. In this blog post, we explore the diminishing effectiveness of phishing awareness programs over time and the financial complexities of implementing such employee cybersecurity training programs. We also discuss solutions that empowers users to obtain real-time email analysis by a human expert with just a single click. A potentially ideal solution to offer efficient protection against email threats without burdening IT teams or users.


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Surveillance des événements liés aux informations de sécurité GoSecure TitanMC (SIEM)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC
Notre SOC
Défense proactive, 24h/24, 7j/7