 Author: Andréanne Bergeron
Author: Andréanne Bergeron
Blaming users for falling victim to phishing emails overlooks the unrealistic expectation for every employee to be a cybersecurity expert. In this blog post, we explore the diminishing effectiveness of phishing awareness programs over time and the financial complexities of implementing such employee cybersecurity training programs. We also discuss solutions that empowers users to obtain real-time email analysis by a human expert with just a single click. A potentially ideal solution to offer efficient protection against email threats without burdening IT teams or users.
Too often, the blame for falling victim to phishing emails falls squarely on the user. Within IT circles, it’s all too common to hear that the user is the weakest link of chain of cybersecurity. However, these narratives overlook a crucial point: Users have their own tasks and don’t have the time or expertise to protect themselves from cyber threats. Research indicates a positive correlation between employees’ workload and their susceptibility to clicking on phishing links. It’s unreasonable to expect every individual to possess an expert-level understanding of cybersecurity. After all, their primary focus is on fulfilling their job responsibilities, not becoming cybersecurity experts.
Even if we were to demand heightened vigilance from users, it’s not a sustainable solution. The tactics employed by fraudsters are increasingly sophisticated, making detection a challenging task even for seasoned professionals.
The Problem With Employees’ Awareness and Training
Numerous studies have explored the efficacy of phishing awareness programs and education training programs for employees. While past research has highlighted the positive effect of anti-phishing training in reducing susceptibility to phishing attacks, an important question persists regarding the sustainability of its benefits.
We have conducted an exhaustive analysis, considering the scientific literature of the past 15 years accessible via Google Scholar, to compile a comprehensive overview of research evaluating the effectiveness of phishing awareness programs (see Table 1). The vast majority of studies (58%) within this review assessed the impact of the effectiveness immediately after the training.
It is widely acknowledged that skill retention diminishes over time, a phenomenon well-documented in the literature. Technical knowledge tends to degrade more rapidly than practical application knowledge, with both types of expertise typically eroding within a month post-training. This phenomenon is represented by the forgetting curve, a psychological model illustrating how memory fades over time. Crucially, this decay isn’t a consequence of technological shortcomings but rather inherent to human cognition.
|
|
Number of scientific articles – N (%) |
| Testing effectiveness immediately after training | 22 (58%) |
| Testing effectiveness 5 to 150 days after training | 12 (32%) |
| Testing effectiveness more than 5 months after training | 4 (10%) |
| Total | 38 (100%) |
Table 1. Number of scientific articles for each testing time frame.
Researchers have made intriguing discoveries regarding the longevity of employee training effectiveness in combating phishing threats. While initial studies revealed that most employees retained their ability to spot phishing emails for up to four months post-training, the onset of forgetfulness became evident around the six-month mark. This underscores the necessity for regular training intervals, with a suggested minimum frequency of every 4-6 months to maintain vigilance against phishing attempts.
To truly comprehend the effectiveness of training over the long haul, we must explore the realms of learning and forgetting theories. By understanding the dynamics of memory retention and decay, we can develop more nuanced approaches to training that prioritize sustained knowledge acquisition and retention. While this subject is best left to psychologists to unravel, let’s focus on what cybersecurity professionals can do to fortify defenses against phishing threats.
What about Reminders As A Solution?
Interestingly, the effectiveness of persistent interventions in improving phishing email detection remains a matter of debate. While some studies indicate positive outcomes, others suggest that additional practice post-training fails to enhance an individuals’ ability to differentiate between legitimate and phishing emails after a mere two-month period. Discrepancies in research findings may be attributed to variations in intervention methodologies. For example, researchers showed that sending by email a one-page reminder of what employee learned during the training not only proved ineffective but also potentially create unintended side effects. They suggest that participants may develop a false sense of security post-training, warranting further investigation into the psychological impacts of such programs.
Moreover, the issue of training fatigue has emerged as a significant concern. Ongoing research indicates that despite repeated workshops, employees tend to plateau in their ability to identify phishing attempts. Even with directed online phishing training, people who tend to click on phishing show minimal improvement, suggesting a diminishing return on investment for traditional training methods. Other researchers also show that exposing employees to phishing during continuous training increases the probabilities of falling for it.
Recent studies cast doubt on the efficacy of current training methodologies, such as annual awareness or continuous customized phishing training, suggesting they may offer little to no added value compared to no training at all.
Cost of Cybersecurity Training Is Also To Be Considered
According to researchers, the average cost for cybersecurity training per employee falls within the range of $20 to $25. However, the sophistication of the training correlates with its expenditure. Some companies are opting for a more personalized approach by enlisting the expertise of professionals who conduct tailored training sessions, specifically addressing the unique risks faced by each organization. While this level of instruction may come with a hefty price tag ranging from $10,000 to $20,000, the researchers argue that its effectiveness surpasses that of generic courses by leaps and bounds.
Yet, quantifying the financial impact of such training remains elusive. Researchers suggests that attempting to measure the effectiveness of cybersecurity education, training, and awareness programs solely through a financial lens is currently impractical. This is primarily due to the dearth of comprehensive statistics on data breaches and cyber threats, compounded by the inherent complexity of these threats, which makes precise measurement challenging. However, organizations can gauge the performance of their employee cybersecurity training programs in specific areas, providing a more nuanced metric of effectiveness beyond mere financial considerations.
What Is The Solution Then?
Significant strides have been taken collectively to enhance user protection. Notably, in 2015, the Internet Engineering Task Force introduced the Domain-based Message Authentication, Reporting, and Conformance (DMARC). This protocol is designed to fortify email domains against unauthorized usage, including email spoofing, aiming to thwart business email compromise attacks, phishing, scams, and various cyber threats. While major email service providers such as Microsoft and Google have adopted DMARC, its evolution hasn’t kept pace with the escalating sophistication of phishing emails. Consequently, there’s a pressing need for the development of additional solutions.
A significant portion of scientific research focuses on studying the efficacy of solutions to counter phishing through applications equipped with sophisticated algorithms designed to identify malicious emails. These solutions are integrated directly into users’ inboxes, employing machine learning techniques to meticulously analyze both incoming and outgoing emails for signs of malicious intent. When these systems detect anomalies (like atypical attachments, unfamiliar sources, or irregular requests from known contacts) the emails in question are either deleted, quarantined, or flagged.
Yet, despite their advanced capabilities, these technological safeguards are not perfect. Cybercriminals continually adapt, devising increasingly clever methods to bypass these digital defenses. As a result, even with the most cutting-edge technology at our disposal, a significant number of phishing emails manage to evade detection. This persistent vulnerability underscores the urgency of exploring additional, complementary strategies to fortify our defenses against phishing attacks for employee protection.
Given the considerations outlined here, one solution that stands out as particularly adapted is the implementation of an email protection add-in. Scientific research demonstrates that deploying a phishing reporting button for the user is highly effective. It allows to effectively detect a significant number of new phishing campaigns in real-time, maintaining a manageable operational load and sustained employee engagement in identifying phishing. While only a handful of companies provide such solutions, notable options include Barracuda, Broadcom, Bitfender. To delve into the specifics of this solution, let’s examine GoSecure’s offering: Inbox Detection and Response (IDR). This innovative solution streamlines the resolution of email threats by automating the process directly within the user’s inbox, as depicted in Figure 1.
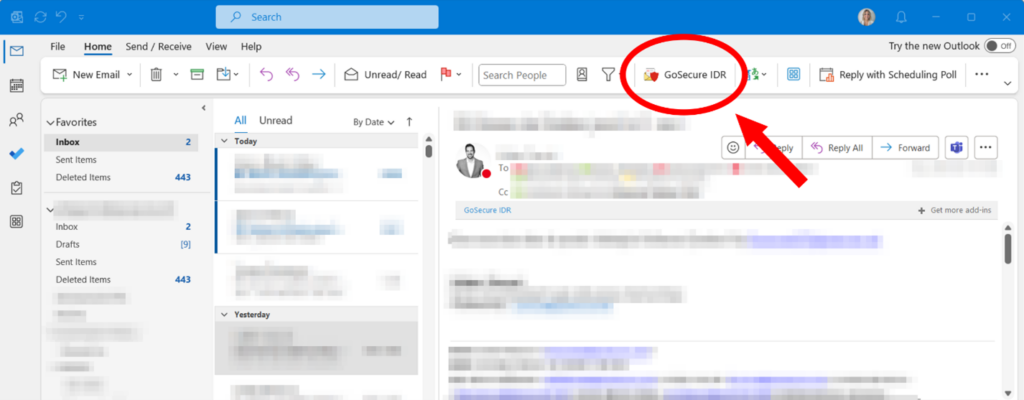 Figure 1. Screenshot showcasing the integration of the real-time email analysis button directly within the Outlook interface.
Figure 1. Screenshot showcasing the integration of the real-time email analysis button directly within the Outlook interface.
In the event that an attacker manages to slip past your current email security gateway, GoSecure IDR empowers employees to effortlessly submit suspicious emails. Upon submission, the email is immediately removed from the user’s inbox and placed into quarantine where it awaits the final disposition. If deemed a threat, the email remains in quarantine and if deemed not a threat, the email is returned to the user’s inbox. These emails are processed through advanced machine learning filters and expert human analysis who do a real-time email analysis for each one you submit. Within minutes, the email is either verified as legitimate or neutralized, all without burdening IT teams or causing disruption to end-users. This type of solution represents the most functional defense against phishing threats, offering efficiency and ease of use.
Conclusion
Rather than assigning blame to users, it’s imperative to recognize that combating phishing demands a collaborative effort. While user vigilance is essential, organizations must also invest in robust cybersecurity measures. Solutions like IDR embody our commitment to safeguarding the users we serve. When coupled with comprehensive practical application knowledge training, these solutions are likely to offer better protection.
In conclusion, the battle against phishing and malicious emails is an ongoing challenge that necessitates a comprehensive approach. While email security screening systems are vital components of our defense, they are not perfect. Blaming users serves no constructive purpose; instead, let us unite in fortifying our defenses and fostering a safer digital landscape for all.


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Surveillance des événements liés aux informations de sécurité GoSecure TitanMC (SIEM)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC
Notre SOC
Défense proactive, 24h/24, 7j/7