
Social identity seems to influence password choice and the virtual identity of users must be understood through the broader social identity behind it. The objective of this research is to determine whether the criminal nature of an online community influences password characteristics and strength.
To explore the degree to which a user’s environment influences password creation strategies, we present a blog post series in which we consider several different perspectives. In our last blog on the influence of different macrosocial factors on password strength, we saw that users are impacted by a number of variables in their environment associated with the country in which they reside. Other studies also show the impact on users’ passwords on variables like sex, age, language, religion or the web services used. In other words, social identity seems to play a role in password choice and the virtual identity of users cannot ignore the social identity behind the human. The objective of this research is to determine whether the criminal nature of a community influences password characteristics and strength. Two hypotheses lead the analysis of this article. First, it is expected that the characteristics of the passwords vary from one group to another. It is also believed that individuals within a community of online offenders will be more likely to choose stronger passwords than individuals in a non-offenders community.
Analysis
The influence of the criminal nature of a community is observed by comparing two databases of passwords that have leaked on the Internet: (1) from a non-offenders social network and; (2) from a hacker forum.
The sample associated with offenders comes from a data leak of OGUsers website. OGUsers was a hacking forum that was known for the sale of stolen social media accounts hacked through SIM-swapping attacks, credential stuffing attacks, and other means. In other words, offenders visit this site to sell stolen accounts or to buy stolen accounts. The database found online contained 200,551 hashed passwords. Our team succeeded in cracking 62,61% of them for a total of 125,560.
The second sample, associated with a community of non-offenders, was also found on the Internet but was already cracked: the passwords were in clear text and ready to analyze. This sample comes from the leak of an online game called Grinderscape. It is a fantasy online role-playing game taking place into the medieval realm. It is a massive multiplayer network that ran for years. The leak contained a total of 1,358,535 accounts.
Logistic regression was performed to identify the variables associated with the criminal group and with the non-criminal group.
Results
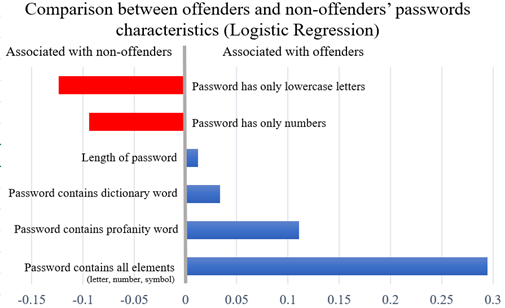
The figure below represents the results: On the left end (in red), the variables associated with non-offenders and on the right end (in blue), the variables associated with offenders. All the variables were statistically significant. Characteristics related to strong passwords, that is, longer passwords and passwords containing all the different elements (like lower case, upper case, and symbol) are associated with offenders. The presence of dictionary words, and the presence of profanity words were also associated with the offenders’ network. Characteristics related with weak passwords, that is, composed entirely of lower cases or of numbers are associated with non-offenders’ network.
Why Do Hackers Have Stronger Passwords?
Two hypotheses could help explain the results. First, the offender sample consisted of online crime offenders. Offenders who visit OGUsers website used it to sell or buy online stolen accounts. This means that they know how to steal accounts and/or what to do with them and therefore they have superior digital skills compared to most people. Individuals who are conscious of the danger and understand how it works are more likely to choose better passwords to protect their own interests.
The second hypothesis to explain why offenders are better than non-offenders in terms of strategies for password security is that they have something to hide, relative to people who use online games for fun. If an offender’s credentials are revealed, their account might become part of an investigation by law enforcement which could lead to actual arrests. Online games might not produce this type of fear of being hacked and therefore the necessity for a stronger password is not as important. Individuals tend to use better password security strategies when they are created for important accounts (e.g., bank account).
Besides password strength, another observation was made comparing the two samples: offenders tend to use more profanity words in their passwords compared to non-offenders. This observation is insightful to contribute to specialized password-cracking lists.
It is important to note that the original leak of OGUsers database contained 200,551 hashed passwords. Our team succeeded in cracking 62,61% of them. This means that 74,991 passwords were not cracked and could not be analyzed in this study. Those passwords are strong passwords as the usual tools and techniques to crack the passwords were not able to uncover them. We believe that this limit in the manipulation of data, however, does not impact the results of this study as offenders were considered better at choosing strong passwords already. The inability to crack the entire list of passwords is another indicator reinforcing the fact that this community is better at choosing stronger passwords.
In Summary
- Password Strategies Vary ACROSS Communities: There is a difference between offenders and non-offenders concerning password creation strategies. Users within the same group tend to have passwords with similar characteristics; and those characteristics show marked differences from the other group analyzed. This seems to indicate an informal alignment of password strategies between people within the same community.
- Password Strategies Are Similar WITHIN Communities: The exploratory investigation of identifiable trends in password formulation across groups allows a better understanding of the social context of password creation.
- This Insight is Actionable: These insights contribute to the constantly changing knowledge base surrounding the lists of frequently used passwords that are not recommended and can be used to improve other related password defenses.
We have seen that environment impacts password choices, including not only location-based factors, but also digital skills as well as specific knowledge around protections and risk – as demonstrated by the analysis of the sample of online offenders – are elements that improve password strategies and tend to increase password strength. As we seek to protect all users, it is important to share these insights around protection tactics and techniques and to inform the community at large about the different aspects of and requirement for a strong password. The next blog will aim to deepen the base of knowledge in that sense and will hopefully empower users in their protection journey.
We would like to thank William Tremblay for his password-cracking assistance.


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Détection et réponse sur le réseau GoSecure TitanMC (NDR)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC