We have previously talked about LinkedIn having an endpoint for Outlook profile cards. This endpoint is receiving email addresses as input and returns the complete profile information (name, company, location, etc.). These sorts of APIs can be abused for OSINT.
To reproduce the set-by-step tutorial your will need an Outlook account (@hotmail.com, @live.com or outlook.com email), the latest version of ZAP and our WebSocket plugin.


To reproduce the set-by-step tutorial your will need an Outlook account (@hotmail.com, @live.com or outlook.com email), the latest version of ZAP and our WebSocket plugin.
Linking your Outlook profile to LinkedIn
Grabbing a valid session token
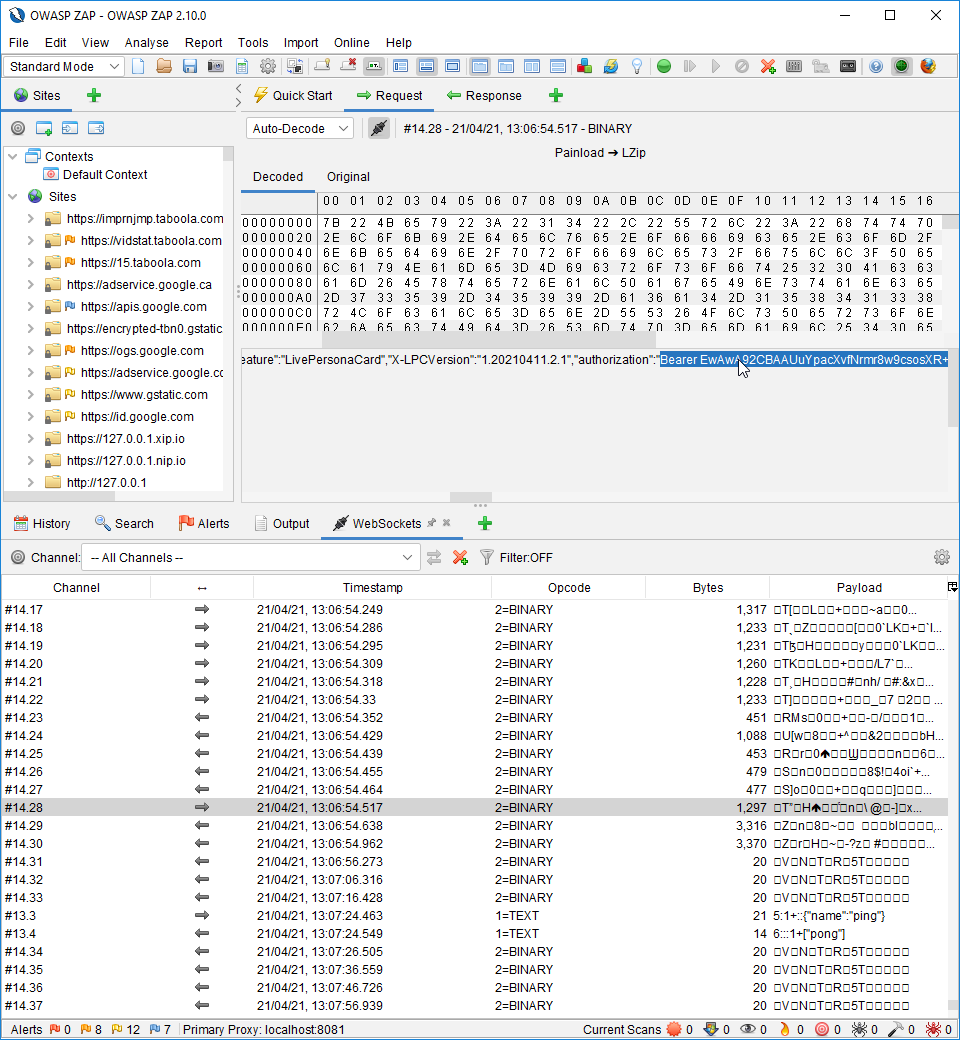
Linking both Outlook and LinkedIn profile will grant you a Bearer token. This token will not be refreshed frequently. To see this token you will need ZAP and our WebSocket decoding plugin. It is available for download at : https://github.com/GoSecure/zap-autodecode-view/releases/tag/version-1.0.0
Automating profile queries
Place the emails you want to test in a file. We will call it “email_list.txt”. Keep in mind that there is limit of approximately 1000 emails queries per day per LinkedIn account (token).
Next, you need to obtain a copy of the proof-of-concept script at https://github.com/GoSecure/linkedin-osint.
Executing the tool will look like this:
> cat email_list.txt
*******@yahoo.com
*******@gmail.com
*******@hotmail.com
*******@libero.it
*******@hotmail.com
*******@soton.ac.uk
*******@hotmail.com
*******@inmovement.org
*******@hotmail.com
>python outlook_http_client.py samples_demo.txt > profiles_demo.json
[+] *******@yahoo.com: Not Found
[!] Nb failures: 1
[+] *******@gmail.com: Found
[+] Summary: Paul *******, "Attorney and Counsel" at "*******", "Waltham, Massachusetts, United States"
[+] *******@hotmail.com: Found
[+] Summary: David *******, "Engineering Specialist*******" at "*******", "Greater McAllen Area"
[+] *******@libero.it: Found
[+] Summary: antonio *******, "******* Professional" at "*******", "Naples, Campania, Italy"
[+] *******@hotmail.com: Not Found
[!] Nb failures: 1
[+] *******@soton.ac.uk: Found
[+] Summary: Tom *******, "Student *******" at "", "Southampton, England, United Kingdom"
[+] *******@yahoo.com: Found
[+] Summary: Madhukar *******, "Financial Crimes*******" at "*******", "New York City Metropolitan Area"
[+] *******@inmovement.org: Not Found
[!] Nb failures: 1
[+] *******@hotmail.com: Found
[+] Summary: Shaun *******, "Strategic *******" at "*******", "Bismarck, North Dakota, United States"*********@gmail.com|{"displayName":" ********* ","headline":" ********* ", "companyName":" ********* ", "companyLocation ":"", [...]



CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Détection et réponse sur le réseau GoSecure TitanMC (NDR)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC