
Defenders: Are You Investigating Products’ Features Enabled by Default?
Many features of products are vulnerable by default and exploiting them makes the life of pentesters much easier! First, survey respondents were asked, based on their experience, how secure proprietary products
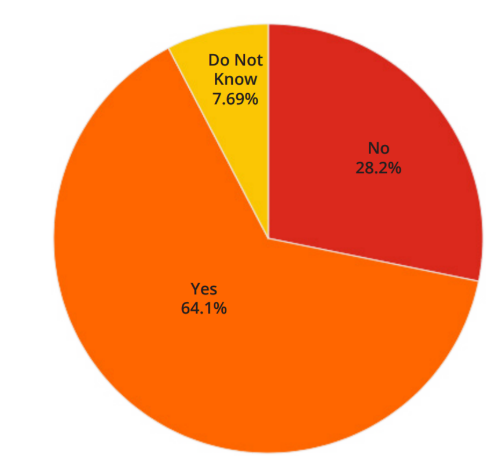
Figure 1 – Investigating Products Default Configuration
Pentesters’ Experience: Currently the Most Common Attack Vector Exploited!
Features vulnerable by default in products represent either a vulnerability (a pentester can leverage the feature to access the systems) or a missing control (an additional feature that helps pentesters in their attack process) that could be mitigated for. Overall, these features are pentesters’ key attack vectors, which they, in their opinion, overuse. Indeed, they estimate that in about 80% of the penetration tests, a system is compromised via these attack vectors. Features that have rarely been seen deactivated during pentesting include NetBIOS and LLMNR –legacy protocols that could allow the capturing of all forms of encoded credentials. Other features include but are not limited to: default passwords, Windows credentials stored in memory, unsecured DNS zones, IPV6 activated by default, and functional ARP spoofing. Pentesters were thus surprised to find that 64% of respondents said that they mitigated that risk. Maybe they have accepted the risks associated with these features. However, and more likely, companies may have investigated the security of a product by asking a penetration test of the product or an audit, such as reviewing the product’s architecture, before deployment. The product may seem very secure in security reports, but its deployment in the company’s environment may be quite different than the environment in which it was first tested. Safe in a vendor’s lab and safe in your environment are likely two very different forms of “safe”.
Pro Tips on Products Configuration
As a reference for readers, below are some pro tips related to investigating products’ features enabled by default that could represent a risk on corporate networks.
- If your enterprise uses Windows and you have no legacy operating systems (such as Windows NT) in your environment, disabling the NetBIOS and LLMNR protocols is an easy quick win for the security of your internal network.
- If NetBIOS is needed in the environment, segregate the assets that require it from the main corporate network, implement a WINS server for NetBIOS name resolution, and configure those computers to use the WINS server by pushing the corresponding registry key via GPO. Furthermore, considering the importance of this attack vector for pentesters, a strong emphasis should be put on deactivating features vulnerable by default in products. Unfortunately, an exhaustive list cannot be provided as there are simply too many products to enumerate.
- In the long term, establish a hardening configuration standard for the different types of systems existing in the organization. The Center for Internet Security (CIS) with its CIS benchmarks, a globally recognized standard, offers extensive configuration guidelines for various technology groups.
Conclusion
These findings are part of the Cybersecurity Perceptions Versus Reality report that highlights the key results of a two-year long study that aimed at understanding a disconnect that exists between how defenders perceive the value of their implemented security controls, and the most common attack vectors leveraged by penetration testers acting as potential attackers. The report is available in French and the microdata of the survey is available online.


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Détection et réponse sur le réseau GoSecure TitanMC (NDR)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC