Summary of a research that uncovers the sextortion spamming scheme
This week, our cybersecurity researcher presents the Spams meet Cryptocurrencies: Sextortion in the Bitcoin Ecosystem research results, at the Advances in Financial Technologies (AFT) academic conference in Zürich. This research, also covered by the MIT technology review, is extensive: it involves an analysis of over 4 million sextortion spams and their associated payments in the Bitcoin ecosystem, to estimate the lower-bound revenue of this new extortion scheme. The research was completed in collaboration with Matteo Romiti and Bernhard Haslhofer from the Austrian Institute of Technology and Tomáš Charvát from VirusFree. The blog post below is a quick review of the main research findings.

Credit: teguhjatipras & mohamed_hassan from Pixabay
Basically, sextortion spams aim at extorting money from spam recipients with the threat that compromising photos or videos will be sent to the recipients’ contacts if an amount, asked in Bitcoin, is not paid. An example of such a spam is presented below (reproduced “as is”, mistakes and wording kept for authenticity) :
I know *** one of your pass word. […] Well, I actually installed a malware on the adult videos (porno) site and do you know what, you visited this web site to have fun (you know what I mean). When you were watching video clips, your browser started out working as a Remote control Desktop that has a key logger which provided me access to your display and web cam. after that, my software gathered all of your contacts from your Messenger, Facebook, and email . […]
You get two different choices. […]:
1st solution is to dismiss this message. In this instance, I will send your actual video recording to just about all of your personal contacts […]
Number two solution should be to compensate me $1000. […]
You will make the payment via Bitcoin (if you do not know this, search for « how to buy bitcoin » in Google).
BTC Address to send to: 1GYfPNat1uQzrBBKTzftMtZ5TgzNdNmTL9
Classifying over 4 million of these spams into 35 specific campaigns and tracing their transactions in the bitcoin ecosystem, the main conclusions are that spam sextortion is not quite sophisticated, yet it represents a lucrative and cost-effective business.
Not Quite Sophisticated
Spammers sent the emails via the Necurs botnet. To find emails and their related passwords, they obtained data leaks and pastes already available online. Indeed, with a list of 632,688 unique cleartext passwords found only once in the email dataset (to avoid passwords such as 12345), 25% of them were randomly selected to see if they could be found in 21 publicly available data breaches (e.g., MySpace, Linkedin, Twitter, Yahoo, 665KK). More than half (51%) of the passwords in the dataset were found within these existing breaches.
The basic structures of sextortion spams are always very similar, with little variations in the phrasing or the threat. Indeed, using clustering heuristics out of the four million spams investigated, 35 specific campaigns were found (all sent in various languages). The distinctive features of the first 15 are presented in Table 1 below.
Table 1 – Key Distinctive Features for Each Campaign
| A | A Trojan virus exploited the device and an anti-virus can’t detect it as a « Trojan Driver » updates the signature every 4 hours |
| B | RDP was exploited with a keylogger and the device was infected while watching compromising videos |
| C | The primary goal was to lock the device and ask for money, but a sextortion ransom was asked instead |
| D | The attacker is a member of an international hacking group and knows all of the recipient’s secrets |
| E | A RAT software was installed on the device and discovered compromising videos |
| F | A virus infected the device via porn Websites and two options are presented: to pay or not to pay |
| G | The attacker is known on the DarkNet and hacked the recipient’s mailbox a long time ago |
| H | The attacker is from China and the e-mail is a last warning |
| I | The recipient’s password was intercepted via a porn website and malicious software now intercepts the password every time it is changed |
| J | A Trojan with remote access was installed on the device and the device was additionally hacked through porn Websites |
For example, Campaign D’s distinctive feature is that the attacker is a member of an international hacking group, while campaign G states that the attacker is known on the « DarkNet ». Beyond these features, the threat is always the same: pay a certain amount in bitcoin or compromising information will be sent to your contacts. The spam messages are always filled with English spelling mistakes and syntax issues.
The spammers do not seem to attempt to refine their deceptive scheme: they reuse bitcoin addresses across spamming campaigns and regardless of the language in which the spam is sent. By reusing these addresses, they cannot assess which campaign is most successful or which language yields most payments. Moreover, in terms of pricing strategy, they do not ask for higher ransoms for spams in which a password or a phone number was mentioned (usually provided in data leaks or pastes). This is surprising: such information could be considered valued and worthy enough for asking higher amounts.
The only sophistication found in the scheme is related to the pricing strategy regarding the language in which the spams are sent. Spammers ask for higher ransom amounts (based on pairwise t-tests) for spams sent in English, Slovenian and Korean and for lower amounts for spams sent in Polish, Italian and Spanish, regardless of the campaign, as shown in Figure 1.
Figure 1 – Average amounts asked per Language and per Campaign
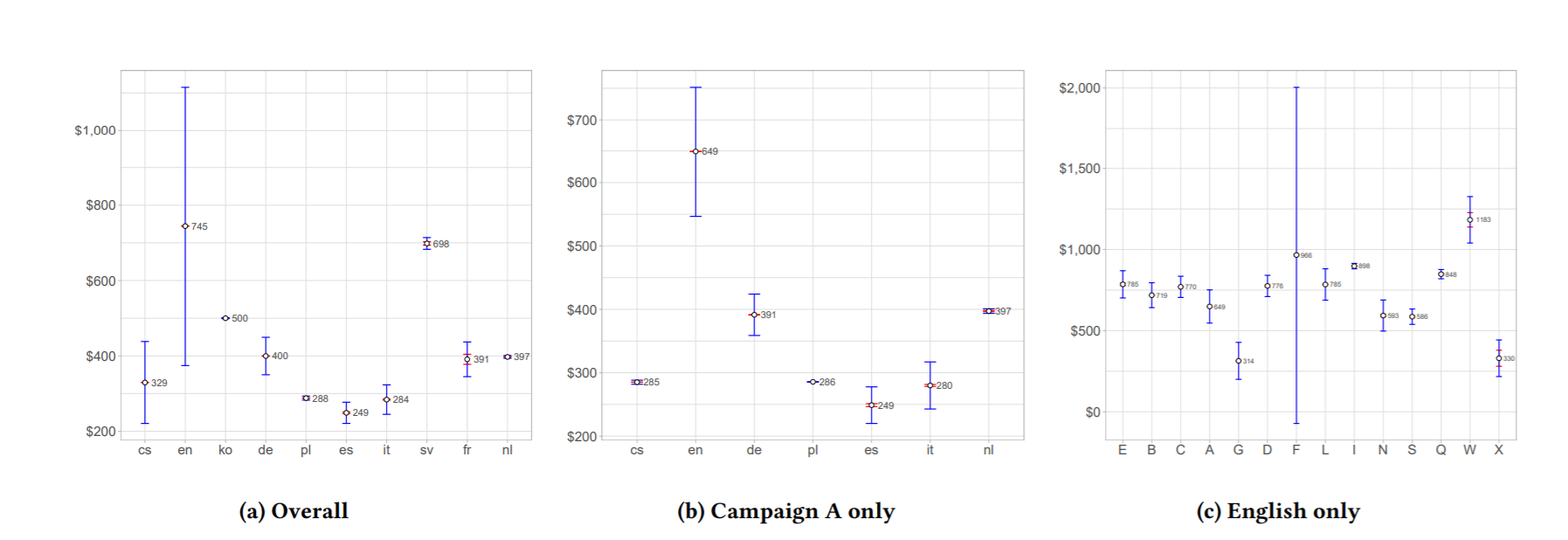
lucrative and cost-effective business
Although not quite sophisticated, sextortion spams seem to be a lucrative business. Indeed, filtering out unrelated transactions, the research shows that sextortion spammers generated a lower-bound revenue of $1,300,620 for an 11-month period, representing approximately a minimum revenue of $122,933 per month. Revenues from traditional spams (i.e. dating sites, pharmaceutical or counterfeit products), on the other hand, were found to range from $3.5 million to $12 million per year. Sextortion spam may thus, at first, seem less profitable than traditional spam campaigns.
Yet, traditional spamming requires far more logistics, in terms of operations: once a spam has reached an inbox, traditional spammers usually have to orchestrate and plan an elaborated operation to avoid URL and domain blacklisting, as well as Website take downs by Internet Service Providers (ISPs) and registrars. Moreover, they have to provide reliable payment processes and banks that will accept to receive such payments (for more details on the operations that traditional spammers have to go through, see Levenchenko et al., 2011).
Sextortion spammers, on the other hand, are involved in a much simpler scheme: they only have to send spams that are somewhat convincing and hope that email recipients will pay the ransom. The process requires the use of a botnet, a credible threat and some bitcoin addresses. Sextortion spammers do not have to face the costs associated to the upper-end of the spam supply chain. Avoiding these intrinsic costs make their business simple, cost-effective and thus, lucrative.
Unlikely to stop
Considering how cost effective the business is, the threat is unlikely to stop. Instead, those behind these schemes will evolve and develop new strategies and potentially try new cryptocurrencies that are less traceable. The anti-spam community should focus on preventing these spams reaching users’ inboxes, by tagging messages that include cryptocurrency addresses, sextortion wording, and that come from IP addresses that are known to be part of botnets.
To read the entire story, see the Spams meet Cryptocurrencies: Sextortion in the Bitcoin Ecosystem paper.


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Détection et réponse sur le réseau GoSecure TitanMC (NDR)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC