 A staggering 87% of people believe that malicious hackers possess exceptional computer skills. One might assume they would predominantly use anonymity networks like Tor to mask their true identities. However, our study reveals that attackers share the same browser preferences as the general population and choose it in relation to their malicious intentions. In this blog, we explore the nuances of browser choices made by attackers who have compromised a system.
A staggering 87% of people believe that malicious hackers possess exceptional computer skills. One might assume they would predominantly use anonymity networks like Tor to mask their true identities. However, our study reveals that attackers share the same browser preferences as the general population and choose it in relation to their malicious intentions. In this blog, we explore the nuances of browser choices made by attackers who have compromised a system.
What if I told you that it’s possible to spy on malicious hackers and gather information about their actions without them knowing? In fact, this can be done thanks to PyRDP, an open-source tool developed by GoSecure’s research team. This opportunity to observe attackers provides many interesting avenues for research that has the potential to contribute greatly to the field of cybersecurity. In this blog post we will explore attackers’ behavior related to their preferred browser.
Browser preferences in previous studies
We all have our personal favorite browser, and that choice mainly depends on our preferences and needs. In other words, the features of a browser impact our choice when deciding which one we will use.
Researchers explored the five most popular web browsers (Chrome, Firefox, Internet Explorer, Opera, and Safari) and they conducted a pre- and post-test experimental study in which the 105 participants had to test the different features. Prior to the tests, the majority of students used Chrome. After the tests, while Chrome remained the most used browser, Firefox and Opera saw slight increases in usage. Meanwhile, Internet Explorer and Safari maintained consistent usage levels before and after the tasks. It is worthy to mention that participants notably considered browser responsiveness when making their choices of preferred browser.
Another study focused on security and privacy complications specifically for Opera, Chrome, Safari, Firefox, Internet Explorer, and Microsoft Edge. They found that Chrome and Safari are the two most used browsers. However, despite its widespread usage, Chrome also emerges as the most frequently targeted browser for hacking. Conversely, Firefox is touted as the most secure and reliable alternative. Users transitioning from Chrome to Firefox may experience positive changes in privacy.
The browsers mentioned above are tailored for users accessing what’s known as the surface web, consisting of indexed content accessible through traditional browsers. However, two other layers of the internet exists: the deep web, containing both indexed and non-indexed content, and the dark web, housing intentionally concealed content accessible only through specialized browsers like The Onion Router (Tor).
We know that cybercriminals find it advantageous to use Tor due to its privacy features, and that the most widely used browser among the general population, Chrome, is the most targeted browser for hacking attempts. But there appears to be a notable gap in the literature regarding knowledge about web browsers and their usage by cybercriminals. While the previous studies mentioned shed light on browser preferences among the general population, we wanted to explore the preferences among cybercriminals. No study examines browser preferences among cybercriminals or seeks to understand why certain browsers are favored over others by this group. To fill the gap in the literature, this research aims to primarily describe the behaviors of cybercriminals regarding their preferred browser.
Which browser do attackers use?
The research team deployed high interaction honeypots and collected the data using PyRDP, a powerful tool designed to intercept and analyze attacks on remote desktop connections by attackers. It includes various applications, notably those that can capture video recordings of attacks and log the attacker’s mouse movements. By analyzing 454 video captures that have been recorded between January 2021 and June 2023, we codified the characteristics and behaviors of each session in a comprehensive database. In the analysis of this research project, an emphasis has been put on analyzing the choice of browser of the attackers.
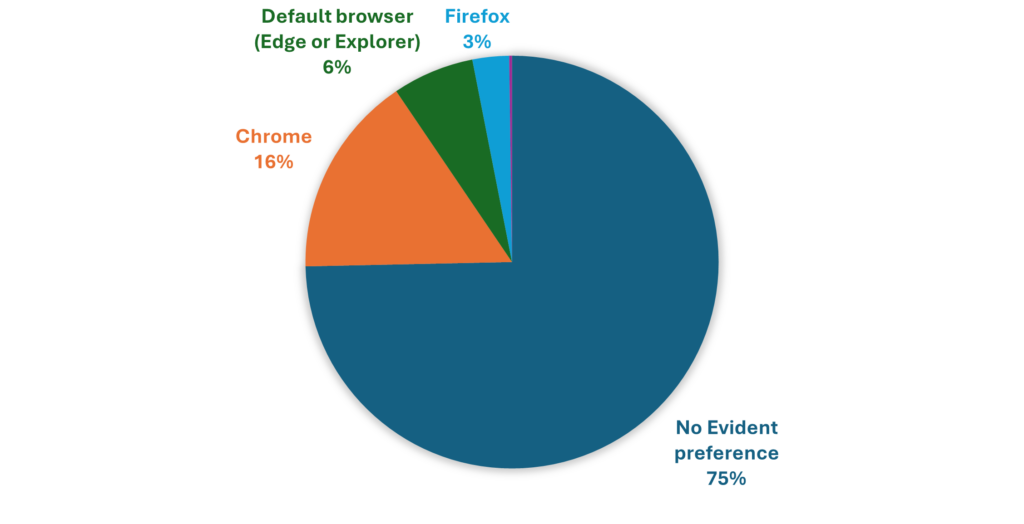
Figure 1. Frequency of preferred browser (N = 454)
Figure 1 shows that in the majority of cases (74.7%), attackers do not download or use any browser. However, among the 115 sessions where a browser choice was evident, Chrome was the most preferred (15.9%). It was followed by the default browser that is already installed on the session (that is Explorer or Edge). Two other browsers were observed: Firefox (2.9%), and Netbox (only one instance – 0.2%).
Despite being unaware of their surveillance, we can see that no attacker decided to download Tor, and two primary hypotheses can explain this behavior.
- Existing Anonymity Measures:
Malicious hackers might not feel the need to use Tor because they already mask their identities through the systems they use to gain access. By employing multiple computers as relays, they can effectively hide their identity, making Tor unnecessary.
- Tor Being Potentially Blocked:
Tor is frequently blocked by IT administrators. If malicious hackers were to download Tor, it could trigger alerts and lead to detection of unauthorized activity. Consequently, the risk of being caught increases if they opt for this option.
What is the relationship between preferred browser and attackers’ activities?
One of the objectives of this research project was to see if we could do a portrait for attackers depending on their preferred browser. We therefore observe the actions performed by the attackers during their session on our system and see if they could be predicted by their preferred browser. We tested 31 different types of actions but most of them were not statistically significant. In the tables below, we present the variables that were interesting and significant.
Certain actions performed by attackers, such as testing the internet power of our system, are not adequately predicted by the choice of browser. As observed in Graph 1, the strength of the relationship is similar for all browsers, leading to no conclusive insights from this variable.
Graph 1. Chi-Square Test for Attackers Testing Internet Power of Our System
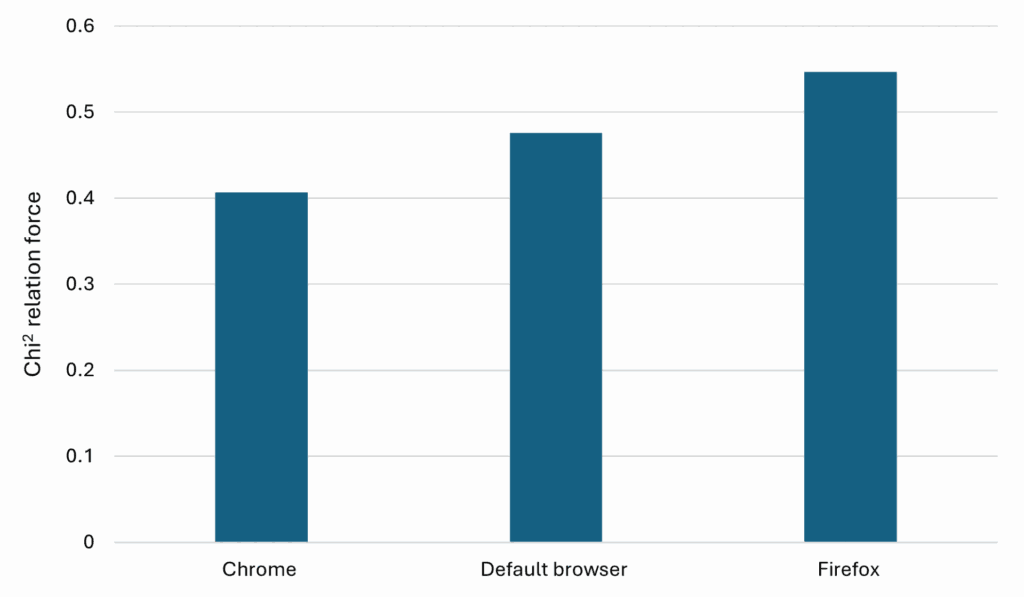 p < 0,001
p < 0,001
Other variables showed more promising results. For example, using the default browser is a predictor for the action of checking the IP, as shown in Graph 2. It is well understood that that the reconnaissance phase performed by attackers is mainly passive and aims to limit system interactions to avoid detection. Consequently, using the system’s default browser minimizes detection risks while efficiently gathering system information.
Graph 2. Chi-Square Test for Attackers Checking the IP of Our System
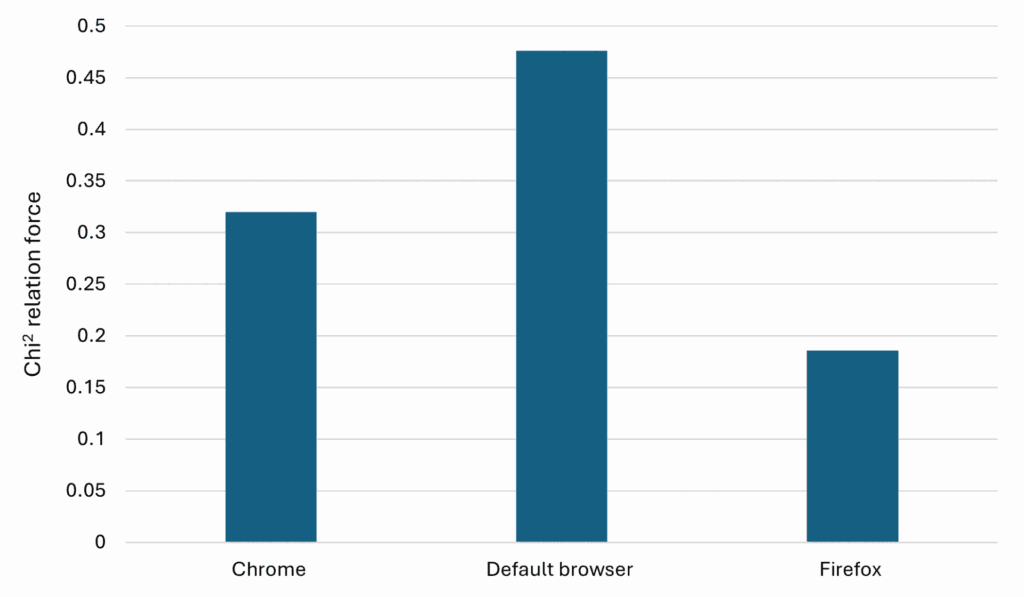 p < 0,001
p < 0,001
Graph 3 reveals that using Chrome is a predictor for attackers downloading tools during their session on our system. This behavior indicates a different approach compared to attackers using the default browser. Those using the default browser appear to focus more on reconnaissance, whereas Chrome users are likely present for a longer duration and engage in a broader range of actions. This result align with the behavior classifications of attackers previously hypothesized in a previous blog post.
Graph 3. Chi-Square Test for Attackers Downloading Tools to perform actions
 p < 0,001
p < 0,001
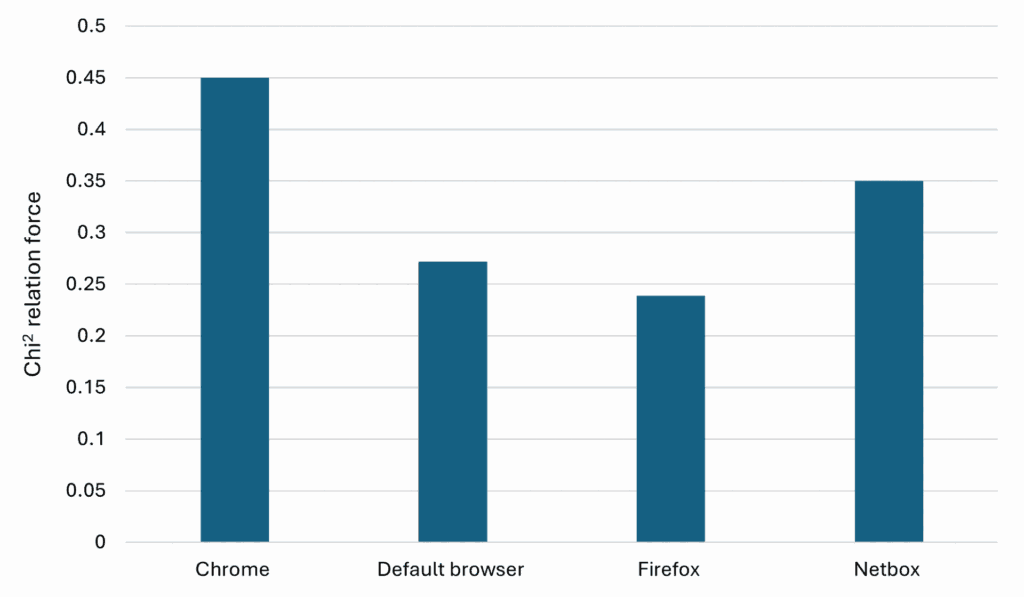
Lastly, Graph 4 presents an interesting observation regarding the skills of attackers. Users of Chrome and the default browser tend to fail at completing certain actions, whereas Firefox and Netbox users do not exhibit the same issue. This suggests a potential difference in skill levels among attackers using different browsers, warranting further investigation into the skills of these attackers.
Graph 4. Chi-Square Test for Attackers Failing to complete their action
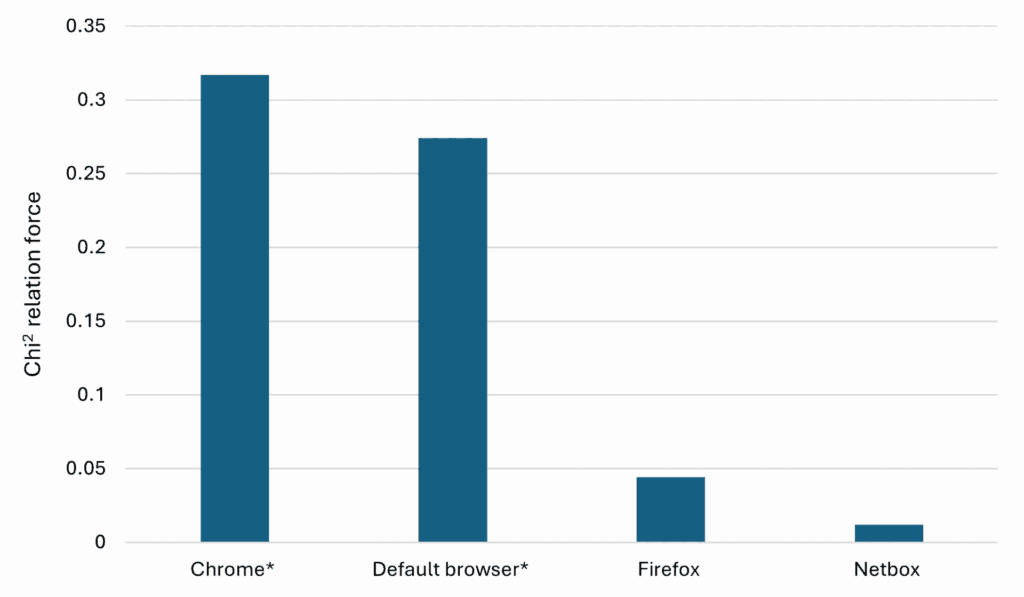 * = p < 0,001
* = p < 0,001
Does the preferred browser predict the type of tools attackers use?
Our comprehensive analysis of the types of tools used by attackers and their preferred browsers indicates that the choice of browser does not markedly influence the types of tools employed (e.g. monetizing; brute-forcing tools; etc.). However, several nuanced observations warrant attention. Notably, Netbox exhibits a stronger relationship with the use of monetization tools than other browsers. It is important to point out Netbox’s capability to generate cryptocurrency through web navigation. The use of this browser already underscores a financial motivation among its users.
Additionally, although the relationship is only marginally significant and the strength of the correlation is weak, Firefox also appears to predict, to some extent, the use of monetization tools when compared to other browsers.
In summary, while the overall impact of browser choice on the selection of attack tools is limited, the specific associations observed with Netbox and Firefox highlight intriguing patterns that merit further investigation into the financial motivations and operational methodologies of attackers.
Conclusion
The primary objective of this study was to describe the browser preferences of malicious hackers. The findings reveal two significant insights. Firstly, attackers do not use the Tor browser. The context of the study led to two possible explanation: 1) Attackers might consider that their identities are already protected by the systems they infiltrate, and 2) Attackers wants to avoid the risk of detection by IT administrators associated with downloading Tor. The second insight is that attackers’ choice of browser is related to their overall strategy rather than only their preferences. If they are doing reconnaissance, they typically use the default browser, Internet Explorer, but prefer Chrome when performing other activities, reflecting the preferences observed in non-criminal population.
This study fills a notable gap in the literature, as no prior research had evaluated malicious hackers’ browser preferences and their impact on their activities. The results allow for generalizing conclusions from the general population’s browser preferences to malicious hackers, confirming that browser choice is dependent on user preferences and needs, consistent with existing literature.
Author: Sophie Marchand
We would like to thank Andréanne Bergeron for the supervision of this research project and for further writing and reviewing of this blogpost.


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Surveillance des événements liés aux informations de sécurité GoSecure TitanMC (SIEM)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC
Notre SOC
Défense proactive, 24h/24, 7j/7