Author – Jeremy O’Boyle
 As part of my 15-week internship within the GoSecure research team, I was given the opportunity to work on Remote Desktop Protocol (RDP) attacks. I was tasked with the codification of attackers’ behavior in RDP recorded sessions. During this part of the research, I developed an interest in the use of Command Line Interface (CLI) by attackers.
As part of my 15-week internship within the GoSecure research team, I was given the opportunity to work on Remote Desktop Protocol (RDP) attacks. I was tasked with the codification of attackers’ behavior in RDP recorded sessions. During this part of the research, I developed an interest in the use of Command Line Interface (CLI) by attackers.
In this blog, I will present my findings concerning CLI use, what my expectations were and how my perception has changed since doing this research.
Why the use of CLI?
In this research, we considered the use of any type of prompt interpreters such as Command Prompt, Powershell, Terminal, Bash, etc. by attackers to accomplish tasks as opposition to using the Windows Graphical User Interface (GUI).
The use of a CLI isn’t mandatory to accomplish most tasks, as those tasks can be done through navigating the GUI, which is often easier as it doesn’t require knowledge on how the operating system works. Experts indicate that “90% of all windows administration can be accomplished without programming languages, scripts or complicated command line-syntax”. However, the CLI provides a faster approach to accomplish tasks, and even allows a more flexible approach to completing complex and repetitive tasks.
I chose the subject of command line-syntax in terminals as I was excited to increase my knowledge on the subject. I also expected attackers to commonly use exploits through command-line syntax to effectively attack the targeted systems. This led me to expect attackers to be programming “masters”, imagining attackers as scary professionals of their craft. So, learning about how and if attackers exploited the CLI could possibly help us understand how good attackers actually are.
What does prior research say?
I was surprised to find out that there weren’t many published articles concerning hackers and the use of CLI, so I extended my horizons to blogs and guides on how to use code and programming. Gunnar Andrews summarizes well what I learned throughout the (few) articles, blogs and guides: “It’s possible to become a great hacker without coding knowledge but having coding knowledge makes it a whole lot easier”. In other words, the use of CLI isn’t required to accomplish most tasks but helps reduce the time and effort needed.
Some research tends to focus on the separation in between different types of hackers, such as those who make a professional career out of it (e.g. professional penetration testers), those who do it as a hobby, and those who do it to break the law (also known as “crackers”). Researchers indicate that while there were some common grounds between professional hackers and practitioners, professional hackers tend to use automated and repeated attacks as well as creating new tools, while practitioners use multiple tasks to minimize the effort with the aid of existing tools. Professional hackers believe crackers are lazy, irresponsible, and not very bright. We can therefore see a divide in between the different types of hackers, with signs potentially pointing towards their capacities or attitude.
I’d also like to mention that throughout the multiple guides on coding and programming that I either read or watched, using scripts or automated tools were included in the basics (or first steps) of learning code. Learning programming languages, such as Python and JavaScript, is also one of the first steps to learning code mentioned in the guides. I’ll come back to these statements later in this blog. After reading those guides, I concluded that learning programming isn’t simple and is time consuming for a neophyte.
Analyzing RDP recorded sessions
The research team watched a total of 454 sessions that have been recorded between January 2021 and June 2023. It corresponds to more than 100 hours of video footage. As one can observe in Figure 1, out of all the sessions analyzed, there were only 36 sessions that included the use of CLI. It represents only 8% of all the sessions! I was expecting a higher percentage of malicious hackers to be using CLI.
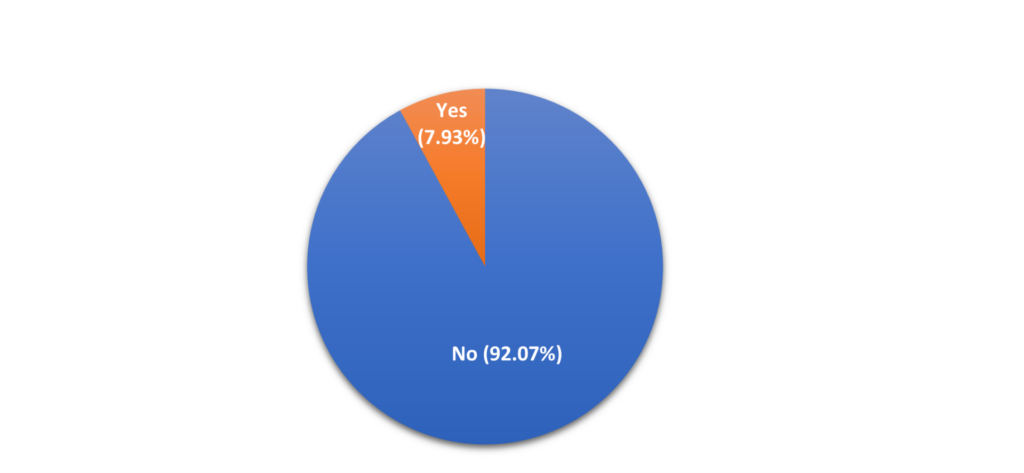
Figure 1. Percentage of sessions that use CLI
One of the most effective approaches to gaining deeper insights into the profile of attackers using CLI is to contrast their activities with those of attackers who do not employ CLI. When analyzing the actions done through CLI (see Table 1), we see that checking the CPU (53%), changing the password (44%), and checking users’ information (36%) are the actions with the higher probability to happen. Similarly, in the sessions using GUI, a high probability of actions related to checking the CPU (28%) and checking users’ information (22%) is drawn.
The bolded lines in the table indicate a high correlation between the actions and the group. Attackers using a CLI are significantly more likely to be (1) adding user, (2) changing password, (3) checking the CPU, and (4) checking IP information compared to attackers using a GUI. The strength of the relationship (Cramer’s V) is however low except for changing password which indicates a moderate strength (0.369).
Table 1. User actions using CLI VS GUI – Chi2 Analysis
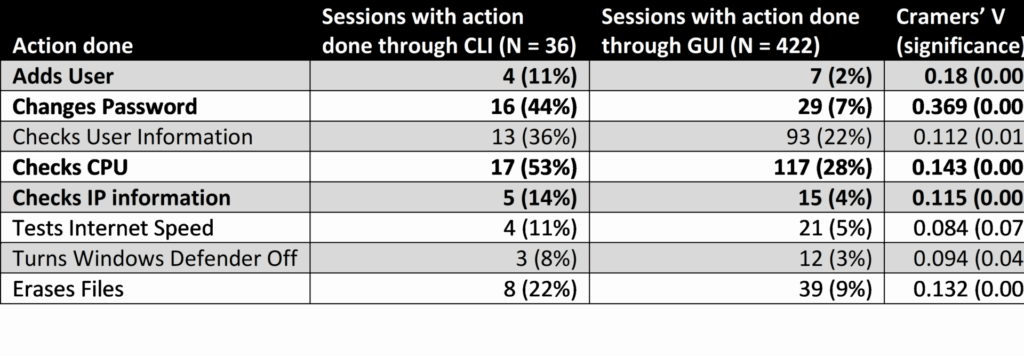
Besides using the CLI to change the password and adding a user, attackers sometime use a CLI for executing pre-written scripts. Collecting the information of the computer using a script was seen in 11% of CLI users’ sessions. Some also use scripts to generate proxies (8%) and others to use API tools (3%).
We have dived deeper into the tools used by both groups and saw a great deal of similarities. The comparison analysis didn’t reveal any trend related to one group over the other.
Grouping Sessions by Attackers
As we were analyzing the session, continuation between a couple of them became apparent. For example, some sessions seamlessly picked up where others left off, with actions initiated in one session and concluded in another. This phenomenon strongly suggested the involvement of multiple sessions by a single attacker. This notion was further fortified by the observation of sessions originating from the same IP or sessions using identical credentials to access. Consequently, we grouped the sessions based on the presumed attacker. This approach enables a more comprehensive examination of the attackers’ actions, offering a representative portrayal that avoids the fragmentation inherent in assuming disparate actions across separate sessions. Of the 36 sessions with the use of CLI, 27 unrelated attackers were identified.
The statistics concerning the number of prompts made in a CLI by the attackers were lower than expected. On average, attackers entered 2.15 total prompts during their session, and 1.62 unique prompts (if we withdraw repeated prompts). Interestingly, 52% of attackers had only 1 total prompt throughout their sessions. Among attackers using a CLI, 33% use it to only change the password while not performing other actions.
Sophistication score
To enhance our understanding of the use of the command prompt by attackers, we identified behaviors that could be associated with sophisticated or unsophisticated use of a CLI, thus creating a sophistication score. This allows us to evaluate the overall level of expertise related to the use of CLI.
Indicators of sophisticated use of a CLI
+1 Attacker does more than 10 actions through CLI throughout their session(s)
+1 Attacker does more than 4 unique (different) actions through CLI throughout their session(s)
+1 Attacker uses tools or scripts in a CLI
Indicators of unsophisticated use of a CLI
-1 Attacker fails or does not complete an action done through CLI
-1 Attacker does one of the following basic actions outside of a CLI*: Adds user / Changes password / User information / IP Information
The reason why we consider using the GUI to perform the action is unsophisticated is because those actions are done simply with a single prompt in the terminal, such as: quser, ipconfig, net user … and net user … /add. And yet, they did it through the GUI.
What is the sophistication level of attackers?
We attributed a sophistication score to each of the 27 unrelated attackers (see Figure 2). The most common sophistication score was -1, with a downward trend towards the higher sophistication scores. The perfect score of 3 was absent.
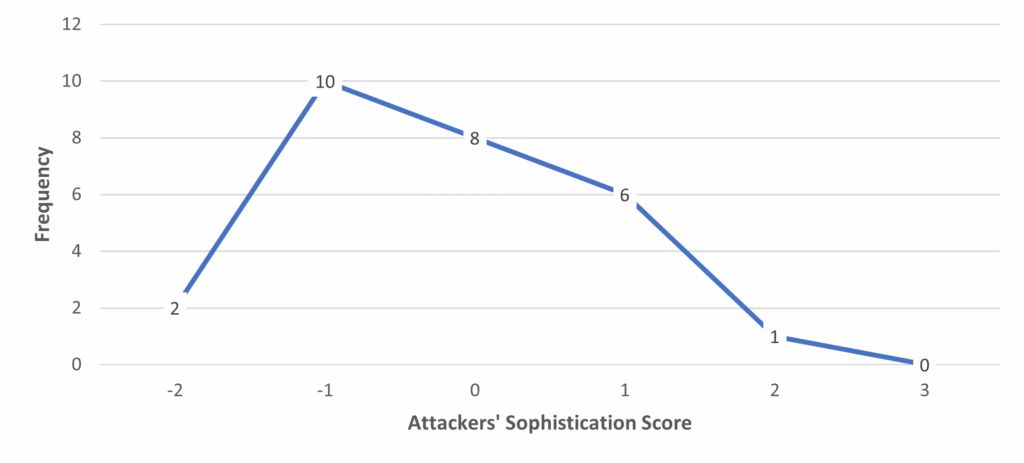
Figure 2. Frequency of Attackers’ Sophistication Score
Are hackers worse than expected?
When starting this project, I thought that I had a basic understanding of code and programming. I was expecting to see multiple sessions with complex use of CLI. Not only were there barely any sessions, but I also realized that I had a lot to learn, as the analyzed sessions did not represent my expectations of malicious hackers.
When learning the basics of coding and programming, I learned about programming language, writing and using scripts, tools and automated task completion, which I barely saw throughout the analyzed sessions. The only programming language present was Python, and the only presence of scripts was seen through already created tools. The use of the command prompt throughout the sessions even seemed to be situated “below” the basics, as it was mostly used to simply change the password or learn about the user/system information. The sophistication score also represents that the hackers present throughout the sessions don’t seem to be that great with the use of the command prompt, since the most common scores were -1 (10 users) and 0 (8 users). There was only one user who had a score of 2, and none had the “perfect” score of 3.
The actions done through CLI in our dataset were mostly simple and a lot of tasks were performed through the GUI instead of using tools and scripts. This demonstrates what was mentioned by previous researchers, simpler tasks done manually are usually related to practitioners or inexperienced hackers. Professional hackers, on the other hand, tend towards automated and reproducible attacks. After seeing the results of our analysis, it’s easy to conclude that attackers are possibly not as good or experienced as I expected. The use of CLI was too simple, didn’t require a lot of effort and often not used to its full potential.
What’s next?
One thing that I noticed while doing my analysis and research on the subject, is that there’s not many publications done about coding and programming by attackers, which possibly contributed to my potentially exaggerated expectation of the capacity of attackers. Most of the publications concerned the opinion/comparison of ethical hackers and people who hack as a hobby or to break the law.
The guides I consulted on coding and programming all seem to point in the same direction; that while knowing how to code and program isn’t necessary, it helps tremendously. When it comes to learning, I realized that it takes a lot of time and dedication, it’s not a simple craft, and gaining experience is your best ally.
The analysis of the dataset demonstrated that hackers aren’t as experienced or good with the use of CLI during system compromise through RDP, but it’s only a small sample among all the possible types of attacks. It’s also important to note that using the command prompt isn’t necessary to be a good hacker, but do the results of our analysis indicate that attackers aren’t as good or efficient in their craft overall? I believe that future research would help reveal more about the behavior and capacities of attackers.


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Surveillance des événements liés aux informations de sécurité GoSecure TitanMC (SIEM)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC
Notre SOC
Défense proactive, 24h/24, 7j/7