 Author: Andréanne Bergeron
Author: Andréanne Bergeron
Discover the evolving Remote Desktop Protocol (RDP) security environment through our insightful exploration of using Network Level Authentication (NLA) rather than keeping the basic Transport Layer Security (TLS) only. Join users, organizations, and researchers in navigating the dynamic cybersecurity landscape, contributing to a safer digital future.
Transport Layer Security (TLS) has historically served as the primary security protocol for Remote Desktop Protocol (RDP) since its introduction in 2003 with RDP version 5.2. TLS encrypts RDP sessions, ensuring secure communication between client and server. Network Level Authentication (NLA), introduced later, adds an additional layer of security by requiring users to authenticate before establishing a remote desktop connection. Both TLS and NLA contribute to the overall security of RDP, with TLS focusing on encryption and NLA emphasizing user authentication. This article aims to shed light on the results of comparative analyses between attacks on RDP honeypots using NLA and those using only TLS.
Divergent attack rate and origin depending on the security protocol
For this part of the research, we based our observations on a year period, from April 1st, 2022 to March 31st, 2023. Over the observed time period, attackers have targeted our NLA-secured server a staggering 16,837,987 times, while the TLS-only-secured counterpart experienced a comparatively meager 282 login attempts, constituting a mere 0.00002% of all login attempts. TLS-only secured system, being an older security infrastructure, seems to attract significantly less attention. This discrepancy challenges the conventional wisdom that people are, without a doubt, more protected by newer security measures. This phenomenon may stem from two assumptions: 1) that attackers might consider TLS systems as abandoned or outdated, prompting them to focus their efforts on potentially more lucrative targets—those that are actively used or have up-to-date security measures in place; and 2) NLA communication protocol facilitates the use of automation to try to brute-force their entry.
Different origins of attacking IP addresses
The divergent trends in the geographical origin of IP addresses behind the attacks on NLA and TLS paint a fascinating picture of the global cybersecurity landscape as presented in Figure 1.
Figure 1: Origin of attacks according to the security protocol
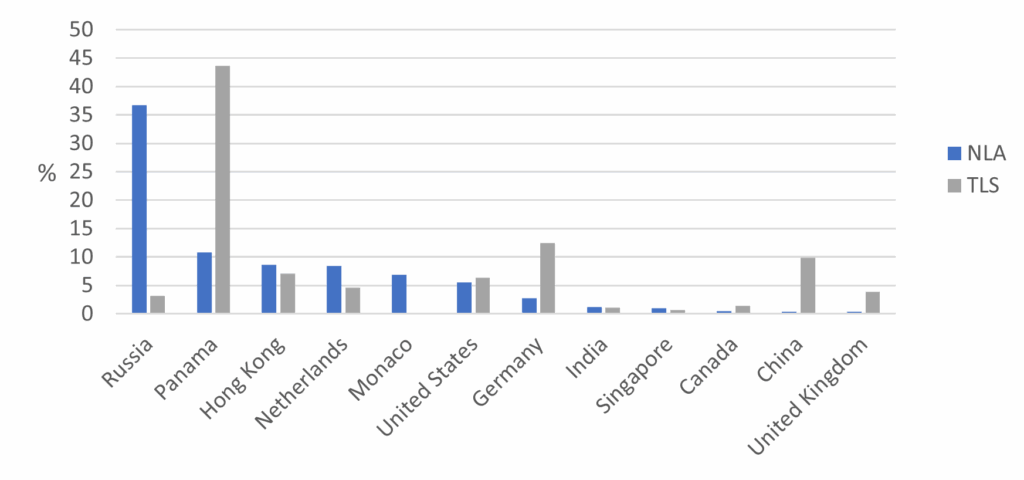
Notably, Panama emerges as a hotspot for attacks on TLS, constituting a significant 43.6% of such incidents, while its involvement in NLA attacks stands at a comparatively lower 10.8%. The same observation can be made for Germany and China (although not the case for Hong Kong) which exhibit a more prominent presence in TLS attacks, underscoring the nuanced strategies employed by attackers based on the target system. Conversely, Russia exhibits a noteworthy inclination towards NLA attacks, commanding 36.7% of the share, while contributing a low 3.2% to TLS attacks. Remarkably, Monaco stands out as a unique case, abstaining entirely from TLS attacks. The shifting dynamics from country to country further highlight the fluid and adaptive nature of cyber threats.
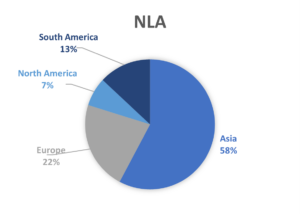
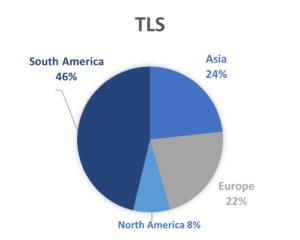
In Figure 2, the origin of IP addresses was grouped by continent to present the differences. While TLS-only secured honeypots are mostly attacked by South America, NLA is mostly attacked by Asia. While the origin of IP addresses provides valuable insights, it’s essential to acknowledge the inherent complexity of attributing attacks to specific countries. Attackers often employ proxies or compromise computers to mask their true locations, rendering IP origin an imperfect indicator. Nevertheless, the observed trends in attacks on NLA and TLS in RDP shed light on intriguing patterns. It draws a nuance which prompts consideration of the cybersecurity landscape in a given country. Some countries have been documented to show disproportionate aggressive behavior in terms of cyberattack, others may exhibit characteristics indicative of proxy-centric internet traffic redistribution, and other countries may experience a higher frequency of cyberattacks, potentially leading to an increased prevalence of compromised computers within their digital infrastructure compared to other nations. As we navigate that information, it becomes crucial to balance geopolitical insights with an understanding of the evolving tactics employed by attackers.
Figure 2: Origin of attack on NLA and TLS by continent
The overlapping in IP addresses
The discovery of eight overlapping IP addresses engaging in brute-force attacks on both NLA and TLS adds a fascinating layer to our study. Surprisingly, these IPs account for 11% of the total attacking IPs on the TLS-secured server, indicating a notable intersection of interest between the two security protocols. What’s particularly intriguing is the lack of discernible trends in terms of geographical origin, date correlation, or attack rate per IP. This suggests a degree of unpredictability and perhaps a level of randomness in the selection of targets and methods employed by these attackers. It reminds us that the motivations and strategies of malicious actors are multifaceted.
The discrepancies in brute-forcing strategies
For this phase of the investigation, it is still imperative to align the time frames for data collection on both NLA-protected and TLS-only protected honeypots. However, the challenge is that to analyze NLA-protected honeypots, we need to crack the attempted logins’ passwords because they are hashed. Since it requires more resources to do this part of the investigation, we concentrated on a sub-sample of 1 month of attempts logins. The selected sub-sample encompasses all login attempts on both types of honeypots occurring in September 2022. Within this timeframe, there were 1,216,305 login attempts on NLA-protected honeypots and 49 attempts on TLS-only protected honeypots. Given the significant difference in login activity, it is important to present the results in percentage form to ensure a meaningful and equitable comparison.
Figure 3: Username trend on brute-forcing NLA and TLS
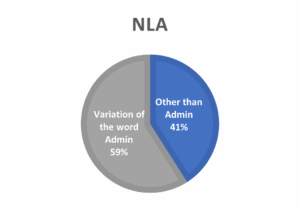
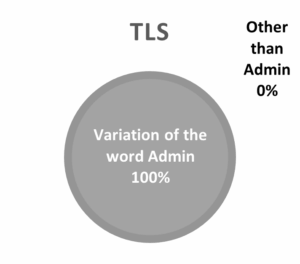
In Figure 3, one can observe that the majority (59%) of the username used in attempt logins on honeypot protected by NLA is the word Administrator or a variation of this word (ex. Admin). The same can be observed on the honeypot protected by TLS except, it is 100% in this case.
Concerning the passwords used in login attempts (see Figure 4 below), the trends are different. The most noteworthy commonality observed across both security types is the prevalence of attacks executed with weak passwords, defined as those containing fewer than 10 characters. It is essential to emphasize that a robust password policy recommends a minimum of 16 characters.
Figure 4: Passwords used in RDP brute-forcing for NLA and TLS security levels
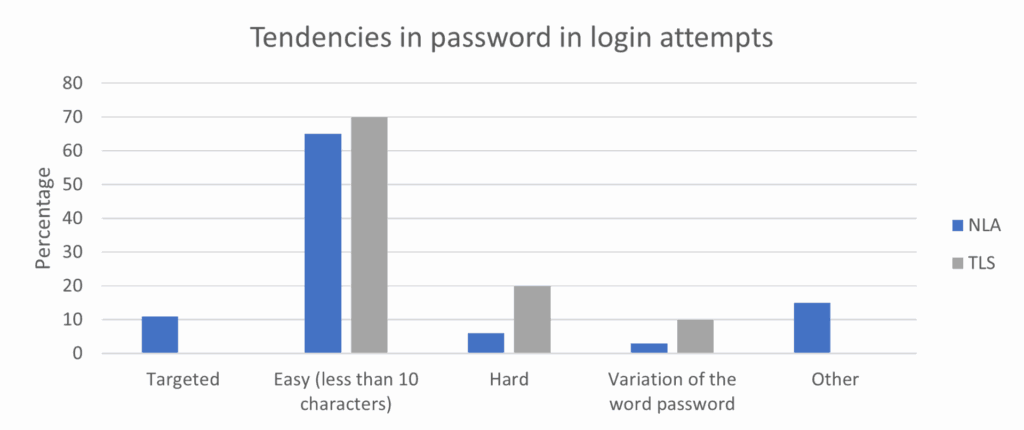
Beside this similarity, the two security types mostly show differences. Logins attempts on TLS-protected honeypots are characterized by a higher proportion of strong passwords. Furthermore, TLS honeypots exhibit a higher number of passwords related to different variations of the word “password” (ex. Pass000; p@ssword; PaSswOrD”). Finally, a distinctive observation pertains to NLA honeypots, where targeted attacks were identified, a phenomenon absent in TLS honeypots. These targeted attacks involve malicious actors leveraging specific information from our system, mainly in the RDP TLS certificate, to formulate passwords. Examples include incorporating our domain name or RDP certificate name into their password structures. This insight sheds light on the sophistication and tailored nature of attacks encountered in NLA-protected environments, highlighting the idea that being more secure also means being the target of more sophisticated attacks.
What’s your pick between the two security protocols?
Ensuring the security of computer systems is paramount and employing NLA is undoubtedly a crucial step forward. According to Censys, out of the 4,768,460 exposed RDP servers at the time of writing, 67% were protected by NLA. However, the conclusion from the analysis shows that using NLA might expose users and organizations to more advanced threats that exploit system information to craft sophisticated attacks. Users committed to NLA typically prioritize their security, diligently staying abreast of evolving security measures to safeguard their valuable assets. Understandably, this heightened sense of security makes them attractive targets for attackers seeking unauthorized access. The other, even more important, reason to explain that NLA-secured systems are more attacked than TLS-only is that the communication protocol facilitates automated scripts to brute-force their logins. Nevertheless, the associated risks of being attacked on NLA can be effectively mitigated through conscientious password and username practices.
For researchers, turning to NLA honeypots is a strategic approach. It not only offers a more realistic representation of security challenges but also provides valuable insights. NLA honeypots, by virtue of being more frequently targeted, yield a wealth of information about the tactics employed by attackers. More precisely, from a criminological standpoint, NLA unveils valuable insights into the human element behind these actions. Previous blogs have extensively documented the human-centric nature of attacks on NLA. This criminological perspective not only enriches our comprehension of cybersecurity threats but also guides future research and development efforts toward creating even more secure environments.


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Surveillance des événements liés aux informations de sécurité GoSecure TitanMC (SIEM)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC
Notre SOC
Défense proactive, 24h/24, 7j/7