 Author: Andréanne Bergeron
Author: Andréanne Bergeron
As the Holiday season upon us, a persistent narrative echo through the corridors of cybersecurity, emphasizing the critical need for organizations to heighten their vigilance and proactively shield their digital assets. While the chorus of caution is undeniable, let’s take a moment to challenge this prevailing notion. Is the Holiday season truly a breeding ground for malicious actors, preying on potential vulnerabilities left in the wake of understaffed security teams? In this blog post, we embark on a journey to scrutinize, question, and demystify the conventional wisdom that surrounds the nexus between festive cheer and cybersecurity concerns.
Cybersecurity conversations on social media seem to show a consensus concerning an increase in risks of being victims of cybercrime during Holiday season. Darktrace’s security researchers, for example, have reported a concerning trend, revealing a 30% increase in the average number of attempted ransomware attacks globally over the Holiday season each year from 2018 to 2020, compared to the monthly average. Remote Desktop Protocol (RDP) emerges as a significant attack vector for ransomware groups, underscoring the importance of fortifying this potential vulnerability. To validate these concerns about increased vulnerability, it’s worthwhile to examine brute-force attacks on our RDP honeypots during the last Holiday season, providing valuable insights into the real-world threats faced by organizations during this critical period.
Unwrapping the Cyber Shenanigans: The Yearly Trends in Brute-Force Attacks
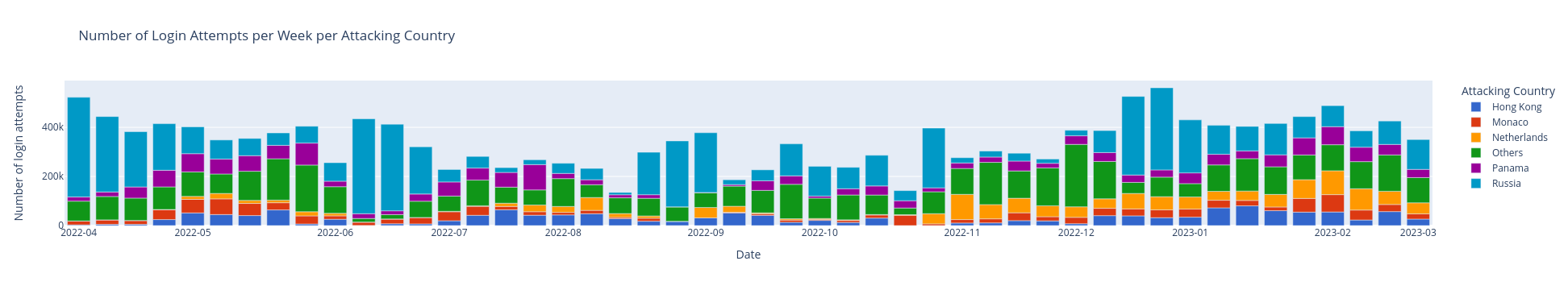
First, when aggregating all the attacks spanning from April 1st, 2022, to March 31, 2023, by weeks, the resulting graph lacks discernible trends (see Figure 1). The data portrays a dynamic landscape where the frequency of brute-force attacks fluctuates without a consistent pattern. The absence of a discernable trend underscores the unpredictability and variability in the ebb and flow of attack occurrences during the Holiday season time frame. To make the graph clearer and more detailed, the source IP addresses of brute-force attacks were grouped by countries. The 5 countries in which most attacks originate are shown and all the other countries are grouped together under “Others”.
Despite periodic fluctuations throughout the year, a surge in activity manifests in the month of December. In pursuit of a more comprehensive understanding, it is imperative to extend the scope of our investigation beyond this initial observation.
Who is the Grinch trying to brute force his way during the Holidays?
If we delve further into the analysis by examining the top five IP addresses with the highest frequency of attacks, we unveil distinctive trends based on the geographical origin of the attacks, shedding light on how patterns may vary across different locations. Four out of five IP addresses in the top five come from Russia.
IP addresses are assigned based on location, which helps identify where login attempts on honeypots originated. However, attackers often use proxies or compromised computers from different parts of the world to hide their location. So, the IP addresses used in login attempts may not tell us where the attackers were, but they can give clues about the location of the proxies or compromised computers they used.
Let’s revisit the graphical depiction of attack activities spanning over a year, as previously presented. However, in this iteration, we will exclude all activities associated with IP addresses originating from Russia (see Figure 2).
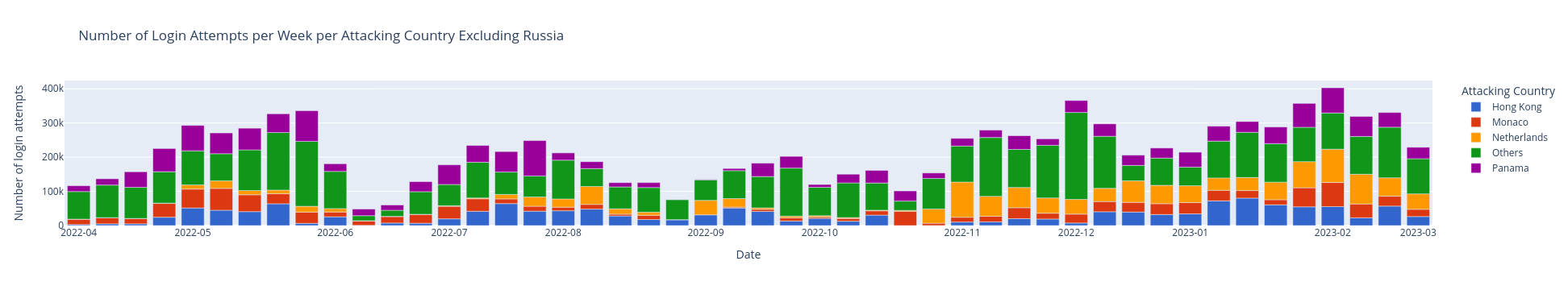
Figure 2
In Figure 2, a noticeable decline in the total number of attacks (Y-axis) is evident, dropping significantly from 700,000 to 400,000 attempt logins per week. The discernible impact of activities originating from IPs from Russia show that those attackers are notable contributors to the overall heightened attack rate on our honeypots.
However, an intriguing surge in attack activities is still observed in December. To delve deeper into the specifics of these December attacks, a detailed calendar analysis was conducted, revealing a pronounced increase at the beginning of December, followed by a subsequent decrease during the Holiday period (see Figure 3). On this graphic, one can observe on the Y-axis the day of the month and on the X-axis, the hours of the day. Each line represents attempts login to our system and the number of attacks per minute (intensity of attacks) is represented by color (see the legend on the right).
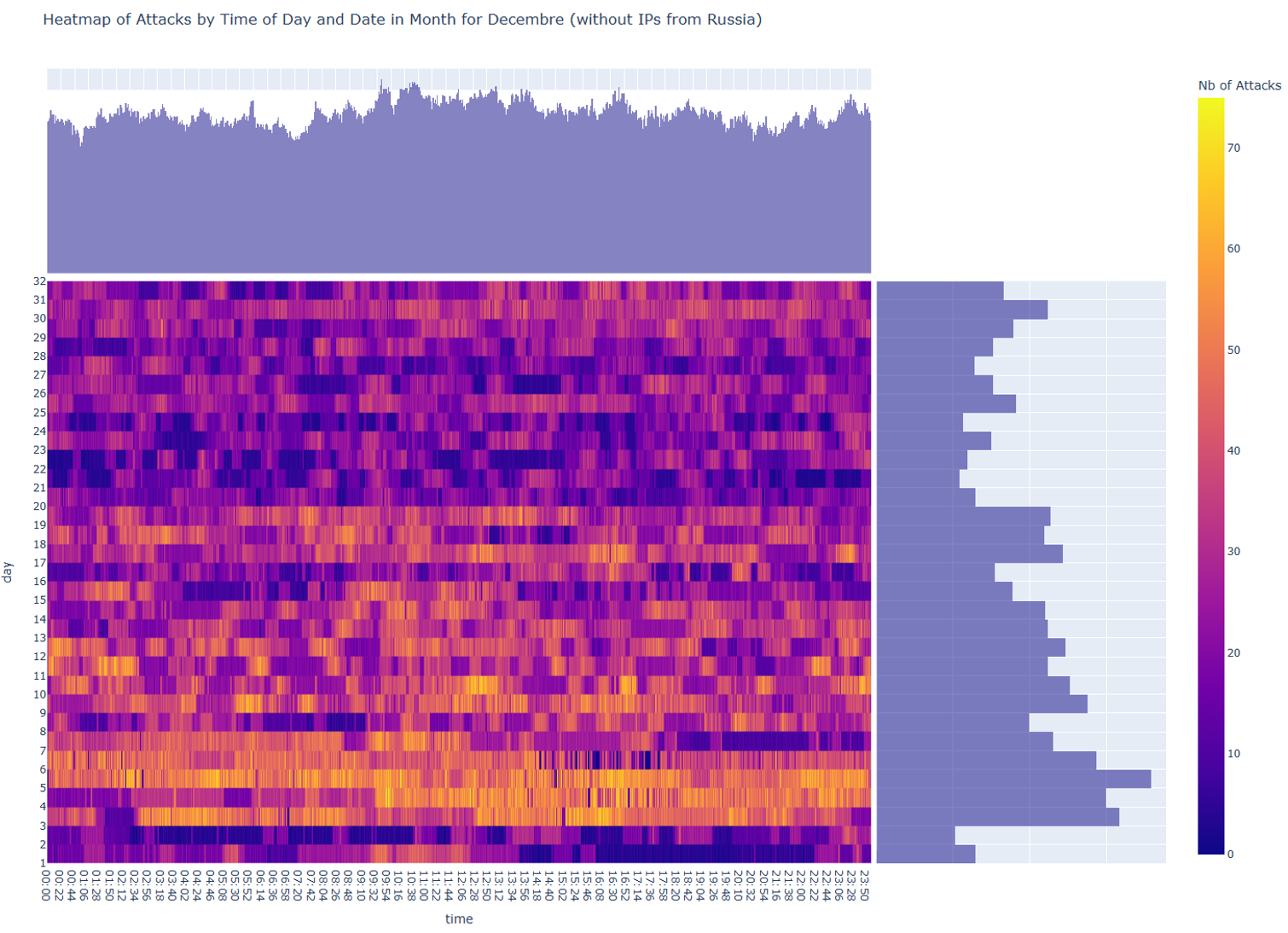
Figure 3
Looking at the results we got, we can confidently say that there is not enough evidence, when- excluding IP addresses from Russia, that our system is more under attack during the Holidays.
Wait a second… what about the Grinch’s activities then?
The graphic below illustrates the activities of attackers exclusively associated with originating IP addresses from Russia (see Figure 4). The plotted line reveals a notable surge in December; however, it is essential to note that this surge is not confined to the Holiday month. Equally significant peaks are discerned at other times of the year.
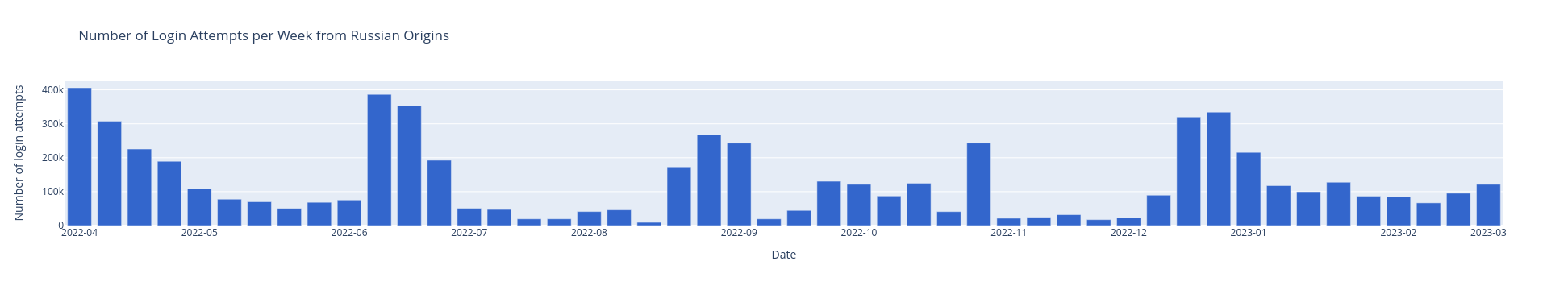
Figure 4
Below are the calendars of attack for the brute-forcing activities on our honeypots of IPs from Russia from August 2022 to January 2023. We observe an important surge of attack activities every month. It is therefore impossible to assert that these attackers are specifically targeting the Holiday period.
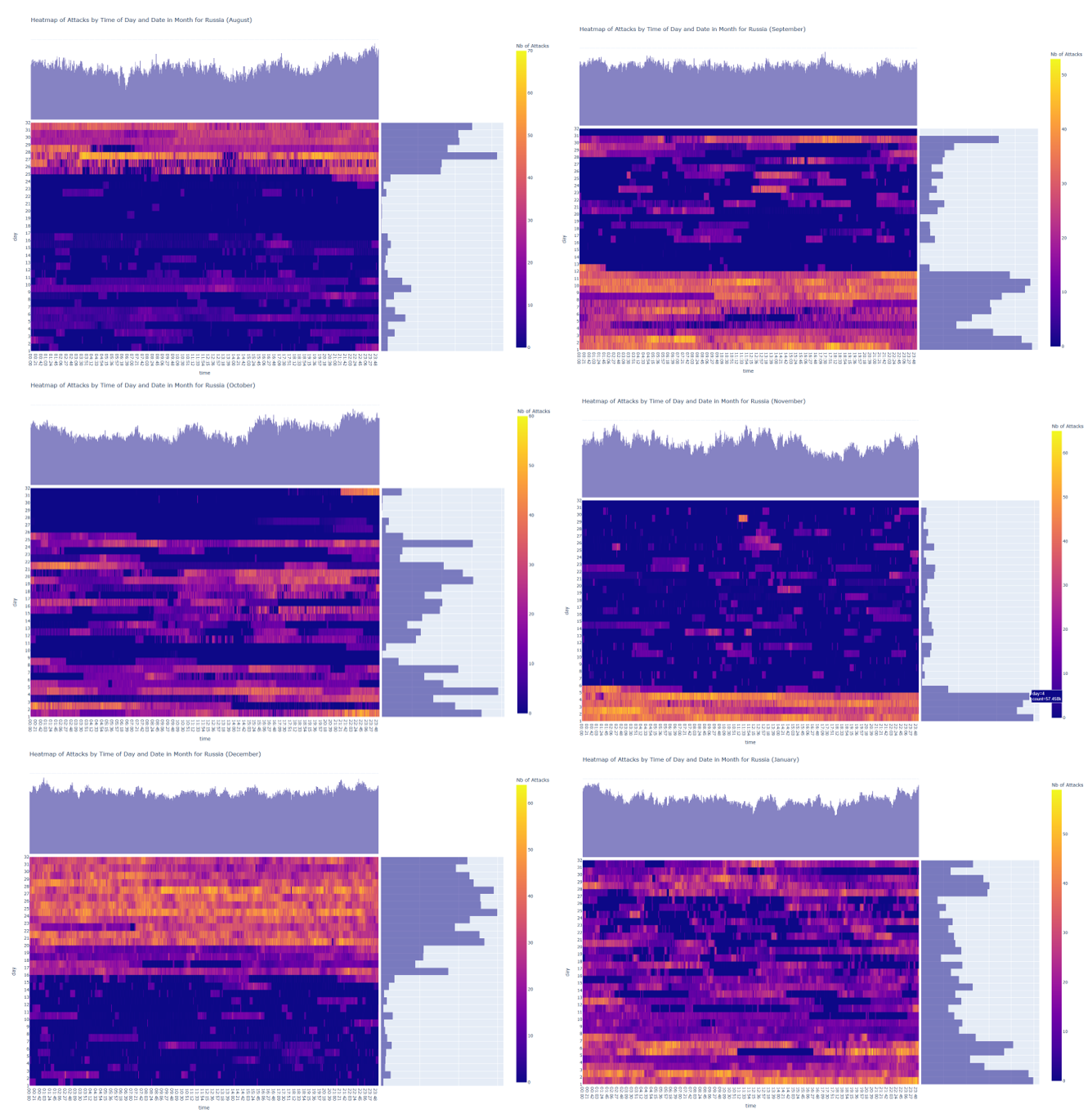
Figure 5
Wrapping Up the Mistle-Mess
After a thorough investigation, we find no tinsel of truth in the notion that the Grinch exploits Holiday understaffing. Our data, much like a tangled string of lights, lacks a clear trend pointing to festive foul play. While a surge of attacks from Russian IP addresses dances through our findings, it’s a jig that plays in other months’ merry measures as well. So, let the Holiday cybersecurity carol sing, for the Grinch’s exploits remain a yuletide mystery, wrapped in a lack of evidence.
However, the observed increase in cyber-attacks originating from Russian IP addresses exhibits a marginally longer intensity compared to other surges – except for the notable spike at the end of August 2022. To ascertain the significance of this occurrence, ongoing data collection during the 2023-2024 Holiday season will be instrumental in facilitating a comprehensive comparison and validation of potential patterns.
It is imperative to acknowledge that this conclusion is specifically derived from the analysis of brute-force attempts on the Remote Desktop Protocol of a United States-based IP address. It is advisable to exercise caution in generalizing these findings, as outcomes may vary when applied to alternative types of data. It is noteworthy to specify that the observations of our email security team were in sync with the results of this study. Based on the total blocked mails over the month of December, the team saw no difference in email borne attacks and scams. When it comes to SPAM, they even observed a decrease in activity. Do you feel more targeted then usual?


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Surveillance des événements liés aux informations de sécurité GoSecure TitanMC (SIEM)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC
Notre SOC
Défense proactive, 24h/24, 7j/7