
Multi-factor Authentication or MFA (sometimes referred as 2FA) is an excellent way to protect your Office 365 accounts from attackers trying to gain access to them. As a second form of protection, along with passwords, it supplies another step in the process to verify the real identity of the user trying to log in. There are many MFA options including SMS, One Time Passwords (OTP) and push notifications from an app. And while the intent of these methods is to provide extra protection, attackers have also begun to look for ways to compromise what should be a security enhancing practice. In this case, we are examining MFA Fatigue by focusing on a current attack vector—Push Notification Spamming. We’ll describe what MFA fatigue is, how it is carried out and detail the steps for IT professionals to detect and mitigate it within their organizations.
Current Attack Campaigns
GoSecure Titan Labs identified new threat vectors using MFA Fatigue attacks based on recent investigations. Our team has also observed a significant increase in the number of attacks performed using this technique.
In the wild, highly motivated and known threat actors are actively using this kind of method to penetrate Office 365 accounts and compromise entire organizations. As app-based authentication mechanisms are being adopted increasingly as a safer way to authenticate a user (versus SMS or phone call) it is expected that this tendency will grow in the future, even be encouraged by Microsoft itself.
What is MFA Fatigue?
The term “MFA Fatigue” refers to the overload of notifications or prompts via MFA applications, in multiple accounts, that the user receives during the day to perform logins or approve different actions. It should not be confused with “Password Fatigue” in which the user is overwhelmed with the number of passwords or PINs they must remember for multiple accounts or events. MFA Fatigue and Password Fatigue do share a similar theme, that the user is “fatigued” (or overwhelmed by volume) and will start setting security best practices aside and become careless, putting their organization and their accounts in danger of compromise.
As previously mentioned, MFA can use a diverse set of mediums to authenticate the user, such as SMS messages or phone calls where the user authenticates their identity via a pre-configured phone number. One Time Password or OTP is another way to verify the user’s identity by generating a passcode that is updated in fixed time intervals. Another choice is push notifications from an app. This is the authentication method we are going to be focusing on, as it enables an attacker to perform a push notification spamming attack.
What is Push Notification Spamming?
This technique is simple as it only requires the attacker to manually, or even automatically, send repeated push notifications while trying to log into the victim’s account. The credentials used could be obtained via brute forcing, password reuse or spraying. Once the attacker obtains valid credentials, they will perform the push notification spamming repeatedly until the user approves the login attempt and lets the attacker gain access to the account. This usually happens because the user is distracted or overwhelmed by the notifications and, in some cases, it can be misinterpreted as a bug or confused with other legitimate authentication requests.
This attack is particularly effective not because of the technology involved, but because it targets the human factor of MFA. Many MFA users are not familiar with this type of attack and would not understand they are approving a fraudulent notification. Others just want to make it disappear and are simply not aware of what they are doing since they approve similar notifications all the time. They can’t see through the ‘notification overload’ to spot the threat.
How to Detect Multiple Push Notifications Attempts in Microsoft 365?
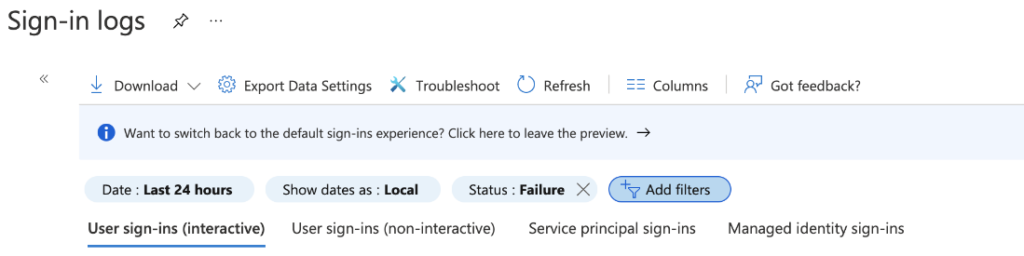
Luckily, this type of attack can be detected directly from the Azure portal by inspecting the Sign-in Logs. We highly recommend that IT professionals take the following steps:
- Go to the Azure Active Directory administration center.
- Under the Monitoring you will find Sign-in Logs, where the information about user’s sign-ins and resources are logged.
- Then filter the sign-in Status by Failure to obtain a list of MFA push notifications denied.

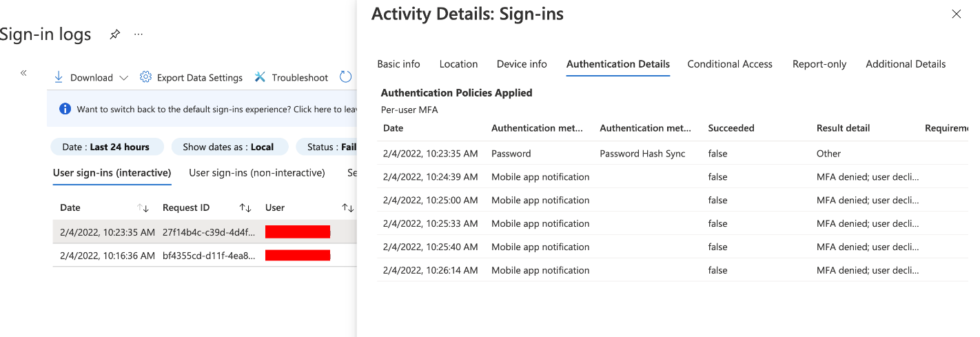
- From here, start investigating each activity individually by going to the Authentication Details.
- Multiple events should be seen as Mobile app notification under the Authentication Method column.
- Push notifications spamming should be false under the Succeed column and MFA denied; user declined the authentication under Result detail.

Log Analytics & Sentinel
Azure Log Analytics can also be used to analyze the queries in search of this kind of behavior. A query like this can retrieve a lot of information that can be used to detect these attacks:
SigninLogs | where TimeGenerated >= ago(31d) | where ResultType == 500121 | where Status has "MFA Denied; user declined the authentication"
This query should retrieve the entries found in the last month and can be customized to retrieve even more results or create alert rules to be notified based on the results of searches.
If Azure Sentinel is in use, then hunting queries can be applied to also catch, alert and even mitigate these attacks by implementing playbooks in response to matches. Some examples can be found in the Azure Sentinel hunting queries repository.
How to Mitigate Push Notification Spamming
There are many ways to mitigate this type of attack. Here, we are going to highlight some of them so that M365 administrators can choose whatever fits their needs. We are going focus on push notifications, since password complexity rules and password reuse mitigations should already be in place.
Configuring Service Limits
One effective way to protect your Microsoft 365 accounts against this attack is to configure the default limits of the Multi-Factor Authentication service. These limits, both default and maximum, can be found in Azure Resource Manager documentation.
Phone Sign-In
A user can help prevent inadvertent access to their account by using the Microsoft Authenticator’s phone sign-in verification method. In this scenario, a unique two-digit number is generated and must be confirmed on both sides. This is very hard for an attacker to compromise since the attacker is shown a number that must be guessed in the phone (which the attacker doesn’t have access to). Only the attacker will know the number and to approve access, the user would have to pick a number out of three options. This way it will diminish the possibilities of approving said access. Here you can learn more about this verification method.
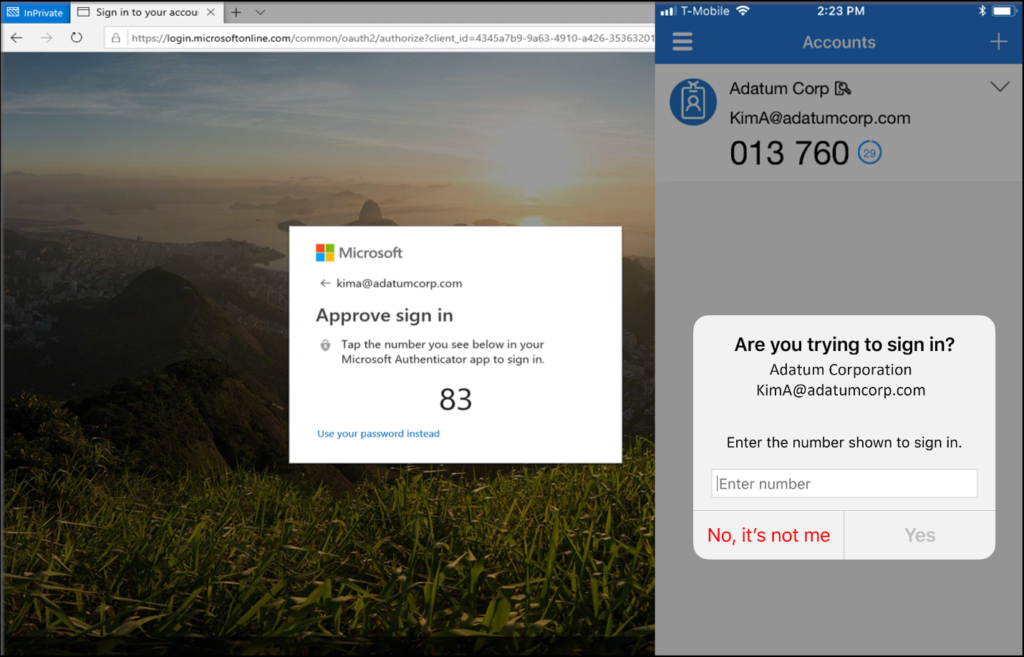
Courtesy of Microsoft.
Disable Push Notifications as Verification Method
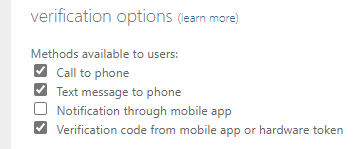
This is a radical move, but a quick solution as will disable the use of push notification as a verification method. These are the steps to make this change:
- Go to the Azure Active Directory administration center.
- Select Per-user MFA.
- Under Multi-factor Authentication at the top of the page, select Service Settings.
- On the Service Settings page, under verification options, and clear the Notification through mobile app checkbox.

- Then click Save.
Conclusion
As we discussed in this post, MFA Fatigue is a real concern with potential implications to compromise Microsoft Office 365 accounts, but there are many ways to protect ourselves from MFA Fatigue and the current rise in Push Notification Spamming attacks. To learn more about GoSecure Titan Labs latest updates and research, check this blog regularly and follow GoSecure on Twitter and LinkedIn.


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Surveillance des événements liés aux informations de sécurité GoSecure TitanMC (SIEM)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC
Notre SOC
Défense proactive, 24h/24, 7j/7