Author: Philippe Arteau
Over the years, Find Security Bugs – or FindSecBugs in short – has evolved from a limited static-analysis tool to one with solid coverage of bug patterns. In this post, we will present the latest milestone from the project: arrival in the OWASP family, some figures and details regarding its new release.

Joining the OWASP foundation
The main motivation for joining the OWASP foundation is to make it clear that the project is a community effort. While GoSecure is using the tool internally for code review assessments, it does not plan to commercialize this specific product. Under the OWASP umbrella, it should be clear to the future contributors that the project is not owned by a single organization or author.
Getting new and active contributors is one of the big long-term challenges for an open-source project. At the moment, the number of external contributions is steady and of quality. This is still something to continue to watch to assure long-term stability.
Moving forward
Becoming an OWASP project is not an the end in itself. We still have plenty of new bug patterns to identify. One of our goals is to reach 2 to 3 releases a year. To provide this release cycle, more time would need to be attributed to the development of new features, but also to improve the integration testing phase. While unit tests cover the functional aspect well, the overall performance and different integration tests need to be done manually at the present time. Being an open project, we will continue to improve the developer documentation to make contributions straightforward.
Some Numbers
50 total contributors, 10 active this year
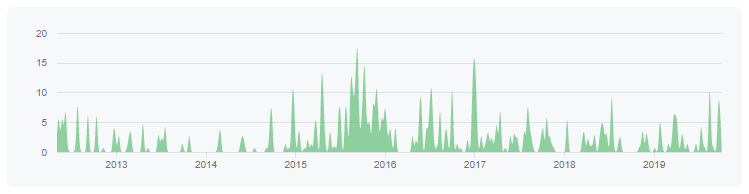
More than 1100 commits over the past 7 years
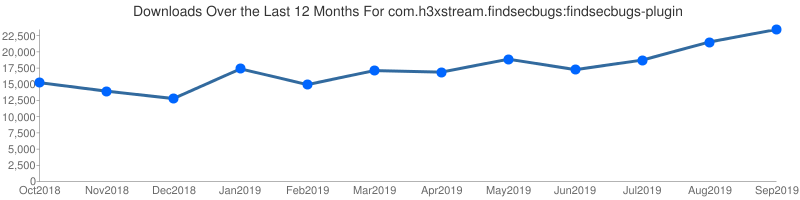
208k downloads for the past 12 months (Source: Sonatype)
There are 300 units tests with 84% coverage.
We are looking to improve the coverage to 90%
New vulnerability detectors in FSB 1.10.0
A new version will be released this week. With this release comes some bug fixes and improvements to existing bug detectors. There are also a few additions that are likely to find new vulnerability classes in your code base.
New bug detectors (or important improvements)
- Mass-assignment when using JPA or JDO entities
- Leakage from entity when using JPA or JDO entities
- Permissive CORS header allowing all origin (New coverage for Spring CorsRegistry)
- Overly permissive file permissions (code doing equivalent operation to chmod 777)
- Insecure SAML configuration affecting provider using OpenSAML API
You can view the complete list of bug patterns currently supported on the website.
Improving FindSecBugs beyond Spotbugs
The SpotBugs integration is critical to the user experience of Find Security Bugs. We are planning to make improvements to the IDE plugins (IntelliJ and Eclipse). We will be looking at language support such as Kotlin and JSP. At the moment, the IDE plugins only support Java source code correctly.
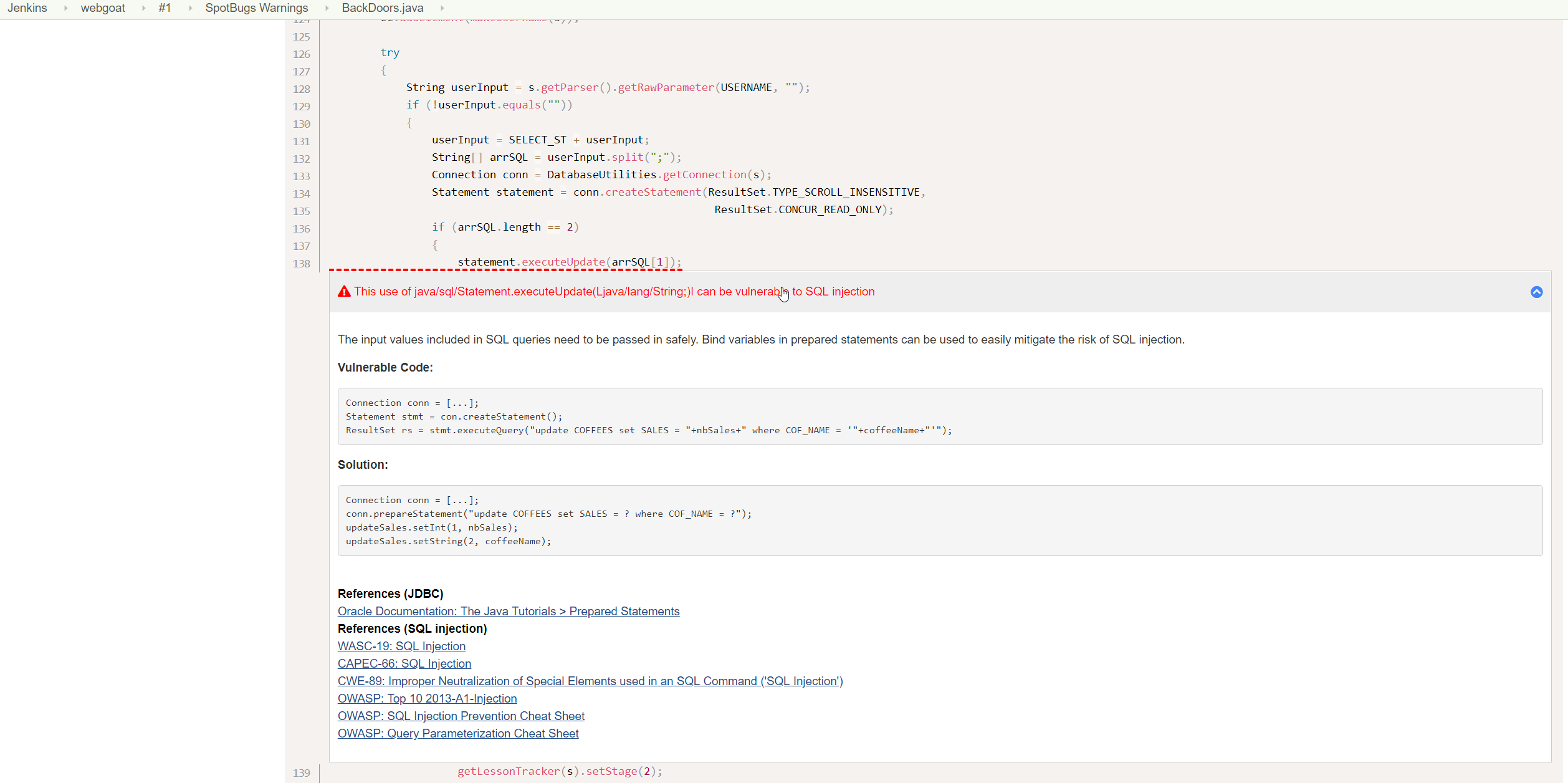
An example of an upcoming contribution to SpotBugs integration is the enhancements of the Jenkins Warning plugin to support any languages not just Java. This change will also be benefiting other static code analysis tools such as Brakeman. The new code highlighter (Prism.js) is displayed below.
Hacktoberfest is coming
If you are an existing user and would like to contribute to the project, there is no better time than the Hacktoberfest. The Hacktoberfest is taking place this month. Multiple issues were tagged in the issue tracker with the tag [hacktoberfest]. Those issue are easy to complete for newcomers. Don’t hesitate to communicate your interest in contributing on the GitHub bug tracker.

That’s all folks, until next blog happy code review !


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Surveillance des événements liés aux informations de sécurité GoSecure TitanMC (SIEM)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC
Notre SOC
Défense proactive, 24h/24, 7j/7