New results related to our research about Linux/Moose, an IoT botnet that conducts social media fraud (SMF), were published in the scientific journal, Social Media & Society, last week. The article is open-source and available at: http://dl.acm.org/citation.cfm?id=3097301. However, if you don’t want to bother reading it, we have provided below a quick summary of the main findings. In general, the study assesses the market for social media fraud.
The study gathered information on the different prices for social media fraud services available online. It investigated the operations of a supplier, an IoT botnet, that conducts SMF mainly on Instagram. Finally, it explored the demand side of the market by profiling potential customers of SMF through accounts found in the botnet communications.
What is social media fraud?
It is the process of creating false endorsements of social networking accounts in order to enhance a user’s popularity and visibility. This can be achieved by liking posts (and any similar endorsement) or following users.
How Much is Fake Popularity on Social Media?
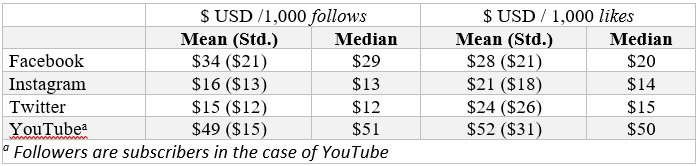
The size of a social media account’s audience – in terms of followers or friend count – is believed to be a good measure of its influence and popularity. This is challenging since a substantial amount of time and resources need to be invested to develop a large fan base. Alternatively, one can resort to buying likes, follows, and views. The table below provides an overview of the prices for such services.
Price of Follows and Likes on the Illicit Market for SMF
Cheap? Careful…
For example, on Instagram, the mean price for 1,000 follows is $16, but the standard deviation of $13 shows that the price varies greatly. One can buy 1,000 follows on Instagram anywhere from 3$ to 29$. Such price variation, found in almost all mean prices for likes and follows, could indicate that:
- The market is still young and immature.
- There are a lot of scammers in the market. Indeed, the fact that the service is fraudulent and buyers have no legal recourse when deceived may attract scammers. Scammers may price SMF services without considering the costs related to providing them, creating false signals in the market!
The Operations of a Supplier Conducting SMF on Instagram
The SMF supplier under investigation in this study is an IoT botnet called Linux/Moose. The infected IoT devices (bots) are used as proxies to relay traffic on Instagram, create fake accounts and conduct SMF.
Fake Account Creation on Instagram
The bots registered accounts either using the Instagram main website or through the Instagram mobile API. Thus, no hacking technique or security vulnerabilities were used by the SMF supplier. In fact, there was no need to develop a sophisticated technique since, to create an account on Instagram, only an email account is required. Since there is no email verification loop at registration, an email can be generated on the fly, as shown in the list below.
Sample of Emails Used by the SMF Supplier
 Fake Account Profiles
Fake Account Profiles
The profiles of fake accounts are easily detectable by anyone. In general, the fake accounts follow many users, have almost no followers, no profile description and no posts. In some cases, the fake profiles have pictures of plants, buildings or landscapes, as shown in the example below.
Example of a Fake Account
The accounts are so easily detectable that of the 1,732 fake accounts found in the botnet’s traffic, 72% were suspended by Instagram within six months. This means that buyers of social media fraud are getting ripped off! They lose the fake followers they paid for every time a bot’s account is flagged and suspended by Instagram! Thus, to keep their fan base, buyers need to buy more fake followers again every six months or so.
Performing Social Media Fraud
To avoid detection by Instagram, the SMF supplier developed scripts that mimic human activity. The mimicking involves different requests that a user would make before conducting a like or a follow, as shown in the table below.
Example of Patterns Mimicking Human Activity

Using patterns like this one, the SMF supplier successfully conduct a like or a follow, avoiding to be flagged as spam by Instagram. The service is therefore successfully provided, but will not last long as little effort is put into keeping the fake accounts alive.
Who buys Fake Online Popularity on Instagram?
Looking at potential customers’ accounts found in the traffic illustrated that buying SMF on Instagram seems to be an international phenomenon. Among the pool of 522 potential customers investigated, the language used in the profile description varied, as shown in the figure below.
Language Used in Potential Buyers’ Accounts
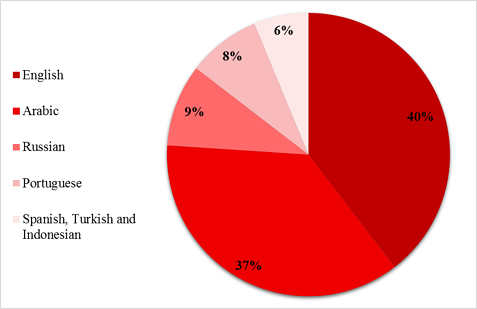
Indeed, 38% had a description in English, 35% in Arabic, 9% in Russian, 8% in Portuguese, and 6% in Spanish, Turkish and Indonesian. This suggests that SMF customers have very diverse origins.
In terms of types of accounts, we found that 20% of the sample consisted of accounts owned by individuals from the entertainment industry, such as (actor/actresses, singers, TV presenters) while 21% consisted of shops selling all sorts of products from jewelry to bikes or protein for hair.
The most striking fact was that 26% of the sample consisted of private users, users who posted pictures about their everyday life, their friends and their activities. More than one quarter of the sample consisted of accounts owned by individuals wanting to boost their popularity on Instagram, mainly for what seemed to be ego purposes.
Example of Private User Account
The remaining accounts had various purposes and varied greatly; they could not be categorized precisely. For example, we found designers, but also social media fraud ads, magicians, hypnotists, accounts for religious purposes, politicians, etc.
Possible Solutions to Deter SMF
Looking at the supply and the demand for SMF illustrated that many types of actors are part of the problem, from SMF suppliers to customers and to online social networks (OSN) themselves. Social network data manipulation creates disinformation, which in turn may be damaging to the online ecosystem. Taking measures against SMF facilitated by botnets is essential to ensure that trust is preserved among members of the social network community. Below, we provide possible solutions to deter this type of fraud.
Email Verification Loop
The supplier is capable of registering fake accounts on Instagram due to the lack of identity validation. Adding email verification loops at the time of registration could significantly increase the challenges faced by SMF suppliers and reduce their ability to massively create fake accounts. Although not insurmountable, this would harden the process of conducting SMF and likely increase the price of the fraudulent service.
Decreasing Availability of SMF Services
The market price analysis showed that SMF services are easily accessible through online searches. Customers can easily find the service they are looking for. Concrete actions against these websites’ availability could be taken. In an ideal world, OSN, hosting services and law enforcement agencies could collaborate to close websites offering SMF services. Such as a strategy was used in the global effort in 2015 to shut down 37,000 websites selling counterfeit goods.
Raising Awareness
The demand analysis showed that those that contribute to the falsification of social network data are not only the suppliers of the fraud, but also those that buy the service. A first step to combating the fraud could be to approach potential buyers and offer them strategies to gain a large legitimate fan base at low cost. OSN could also communicate that SMF services are fraudulent and contribute to online crime when provided by botnets. Raising awareness that such fraud exists could, in turn, indirectly influence the OSN community to be more vigilant when assessing an account’s popularity.
The research results are published in the scientific journal Social Media & Society. The article is open-source and available at: http://dl.acm.org/citation.cfm?id=3097301.


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Surveillance des événements liés aux informations de sécurité GoSecure TitanMC (SIEM)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC
Notre SOC
Défense proactive, 24h/24, 7j/7