![]()
We have been investigating the phenomenon for the past two years, published two papers and presented at multiple conferences, such as Black Hat Europe and Botconf. We have tried gaining the attention of law enforcement agencies’ and politicians’ concerns on the issue, but unfortunately without success.
Links to both papers:
- Exposing the EGO MARKET: the cybercrime performed by the Linux/Moose botnet
- Can We Trust Social Media Data? Social Network Manipulation by an IoT Botnet
Thus, we must say that today, we are quite relieved to see concrete action being taken. Although the fraud involved seems innocuous, its potential to disrupt trust on social networks and manipulate public opinion is massive.
The hard part is upcoming
We believe, however, that the hard part is upcoming. The New York Times article mentioned:
These fake accounts, known as bots, can help sway advertising audiences and reshape political debates. They can defraud businesses and ruin reputations. Yet their creation and sale fall into a legal gray zone.
It is true that the creation and sales of fake likes and follows only break the terms and services of online social networks. Still, the attorney general considered that taking the case was worthy because these fake accounts also appeared to commit identity theft. Yet, there are more criminal activities taking place in this industry. Our own investigation on the matter started through the study of an Internet of Things (IoT) botnet –as inspecting malware is part of the R&D activities of our business. We discovered that the botnet was involved in a large-scale social media fraud market. Botnets are cheap because they are composed of numerous, geographically dispersed, infected devices for which the botnet master doesn’t pay electricity nor bandwidth. They represent a perfect tool for automating the creation of fake likes and follows, but they are also criminal.
 Screenshot of Devumi’s website
Screenshot of Devumi’s website
Thus, we believe that investigating Demuvi is only the tip of the iceberg; it is a small piece of the puzzle that could even be considered a low-hanging fruit: it involves targeting a small company registered on American soil.
IoT botnets have infected devices all around the world with C&C servers located in multiple countries. Taking down this criminal scheme, although a necessity, will be no piece of cake.
This market is a goldmine
If there are so many actors in this illicit industry, it is because there is a lot of money to be made through people’s greed for fame.
Considering prices advertised on websites like Demuvi, we observed that one infected device from Linux/Moose, tasked at creating fake accounts to do likes and follows on Instagram, could generate up to $13,05 per month. Estimating that one botnet owns 50,000 infected devices, up to USD$800,000 could be generated per month by this malware operation.
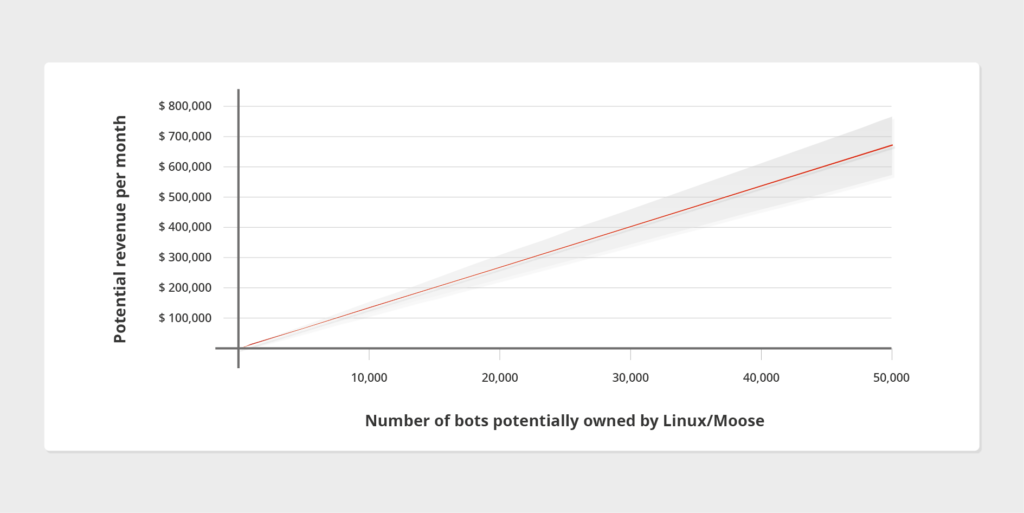 Potential Revenue per Infected Device per Month from our White Paper : « Ego Market When Greed-for Fame Benefits Large Scale Botnets »
Potential Revenue per Infected Device per Month from our White Paper : « Ego Market When Greed-for Fame Benefits Large Scale Botnets »
Such revenue only takes into account fraud conducted on Instagram. Combining these numbers with Twitter, YouTube or Facebook fraud would massively increase the potential revenue of the illicit market.
To conclude, we are pleased to see concrete actions being undertaken against this whole criminal scheme, but hope that this investigation will dig deeper into the bigger picture of the social media fraud industry.


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Surveillance des événements liés aux informations de sécurité GoSecure TitanMC (SIEM)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC
Notre SOC
Défense proactive, 24h/24, 7j/7