 In the last few days, we closely followed the malicious software outbreak that took control of about 12,500 devices, mostly in Ukraine and Russia, demanding a $300 ransom from the infected device’s owner. Although this new attack is fascinating, we noticed that the associated stories quickly got out of hand.
In the last few days, we closely followed the malicious software outbreak that took control of about 12,500 devices, mostly in Ukraine and Russia, demanding a $300 ransom from the infected device’s owner. Although this new attack is fascinating, we noticed that the associated stories quickly got out of hand.
Within hours of the publication of a picture displaying workers sitting in front of infected computers with black screens, assumptions based on unverified statements followed. As expected, the mainstream media constructed a narrative around the attack, such as “Everything to Know About The Latest Worldwide Ransomware Attack”, with industry experts commenting on the threat even though it had not been completely reverse-engineered yet. Though the examples of these baseless assumptions were numerous, we have highlighted three particular cases that were quickly refuted.
It’s Petya! Oh no, wait, it’s nothing like Petya!
On the surface, this new malicious code looked similar to the Petya ransomware. Quick assumptions were therefore made that this new attack was a variant of the ransomware. However, once the threat was reverse-engineered by security researchers, it became clear that the two differed greatly. Though the relationship between these two pieces of malicious code was proven to be quite limited, the new threat was branded a name variant of Petya, misleading the public on the real nature of the attack.
It’s like WCry! Oh no, wait, it’s nothing like WCry!
Following previous highly publicized ransomware attacks, this new threat was quickly associated with WCry. Though the scope of WCry was global, the range of the new attack turned out to be more restrictive. The initial infection vector most likely originated from the updater of an accounting software, called MEDoc, developed by a Ukranian company. With one infected machine, the malicious software used multiple lateral movement techniques to infect other machines. Among these techniques, it used the same SMB exploit as WCry, known as EternalBlue (CVE-2017-0144). Unlike WCRy, the threat didn’t scan the Internet with the infected machines but rather focused on spreading through local networks. This explains why all exposed machines were infected within an hour.
It’s a Ransomware! Oh no, wait, it’s a Wiper!
It appeared that this week’s attack was not at all a ransomware, but rather was aimed to look like one. Disguised as a front to extort users by presenting a ransom note, the goal of the attack would have been to delete data on infected devices. This is because the malicious software was written to overwrite the Master Boot Record (MBR) and the Master File Table (MFT), creating permanent damages on the device’s disk and making it almost impossible for victims to recover their files.
Our take…
Although these three assumptions – and others – were denied by security researchers within days, the harm had already been done. The short attention span of local and national media given to this event shifted yet the wrong story remains. Instead of talking about a targeted – most likely Russian – attack that infected a few thousands of devices to wipe out their data, the mainstream media was fixated on discussing a second worldwide ransomware attack: “‘It’s like WannaCry all over again’: New ransomware attack”. This may be because once a news story is written, few local or national outlets bother to follow up new developments on the subject. It may also be because updates on news articles don’t matter and are rarely read. It is hard to beat the ratings of sensationalism.
This raises questions related to the whole cyber security industry’s responsibility towards the massive disinformation of the general public that happened over the course of these events. The marketing race of who will publish first has had an important role to play in the construction of the false narrative. Shouldn’t the industry increase its standard and be more careful before publishing quick assumptions and analogies?
Moreover, industry experts commenting on the unknown threat and making doubtful amalgams clearly amplified the falsity of the story. Local news coverage of this event has been especially disastrous. We have heard from so called experts describing this attack as a regular ransomware and advising end-users to avoid clicking links in emails, but providing no real insight into the issue. Instead of contributing to the unverified assumptions, shouldn’t industry experts wait until security researchers have published a thorough understanding of the threat?
Who cares? Well…
No one should think for a second that this is little harm done for great visibility. There are real negative consequences that arise from such disinformation. How many times a month can the media cry wolf before no one cares? By sounding the alarms for every cyber-attack, it fuels the public’s indifference. If we continue this way, we will end up like meteorologists that call for thunderstorms when there is just a little rain. Worse, managers, CEOs and CTOs may stop taking these attacks seriously, because there are too many and their company, anyway, was not affected by the latest “worldwide” attack. The way this week’s event was dealt deeply hurt our industry’s credibility.
And since the bar is so low anyway…
Well, since the bar is so low anyway, let’s mention how the industry builds marketing campaigns based on sensationalized attacks. Emails and ads offering products and services to counter the “2017 Petya threat” are being sent in mass. In Canada, to our knowledge, not a single device was infected by the malicious software. Knowing this, why advertise products and services protecting against ransomware, ironically quoting an attack that ended up not being a ransomware? This opportunistic behavior is just another strong signal that something is wrong with the industry.
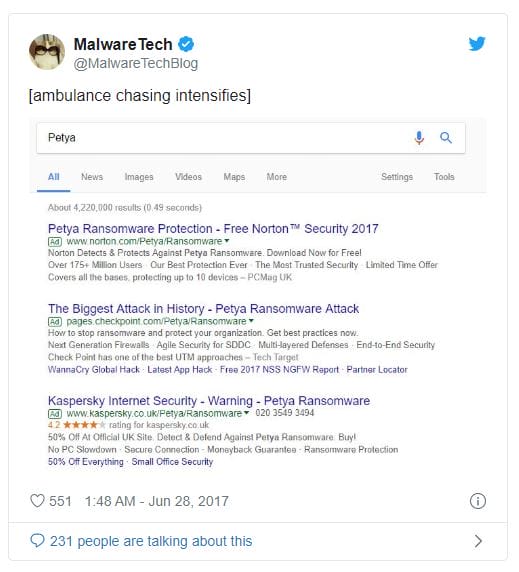
With all said and done, the cyber security industry didn’t help to increase the public’s awareness towards this malicious software. Following this week’s events, it seems rather that it contributed to the development of a false narrative and then used it to its advantage, pushing new advertising campaigns onto its clients.
And this is just the tip of the iceberg…


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Surveillance des événements liés aux informations de sécurité GoSecure TitanMC (SIEM)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC
Notre SOC
Défense proactive, 24h/24, 7j/7