 Author: Andréanne Bergeron
Author: Andréanne Bergeron
Even automated attacks are driven by humans, but the level of engagement we observed may surprise you! When the human or an organization behind an automated attack shows higher levels of innovation and sophistication in their attack tactics, the danger increases dramatically as they are no longer simply employing an opportunistic “spray and pray” strategy, but rather more highly evolved strategies that are closer to a so-called targeted attack.
Hackers Take Control of Information Systems With Brute-Force Attacks
A brute-force attack consists of trying to guess valid user credentials (username and password) for a particular system by trying a large number of different credentials. Usually, many attempted logins per second. These attacks can be automated by leveraging specific tools. Furthermore, the tools and tactics used in these types of attacks can be (and often are) shared between malicious actors.
To gather information for our study of brute-force credential attacks, we launched a set of high-interaction honeypots on the internet exposing a Remote Desktop Protocol (RDP) access – RDP is a Microsoft protocol allowing users to access the graphical interface of remote computers.
We monitored attacks on our research honeypot from July 1 to September 30, 2022, and collected 3,427,611 login attempts. The data collected about each login attempt include: 1) timestamp; 2) IP address; and 3) the credentials tried by the attacker. The attacks were then grouped by IP addresses to study the behavior of attackers. There was a total of 1529 different IP addresses involved in the attacks.
In an effort to enhance our understanding of attacker profiles, we used behavioral profiling based on complex characteristics. We were able to identify several different behaviors associated with automated attacks but also characteristics indicating human-like behavior. Those indicators are presented in the next section. The addition of each of those elements gives us an engagement score to evaluate the level of implication of the human behind the attack.
Indicators of Machine-Like Behavior
 |
A high number of attacks is the first indicator of automated attacks. Each threat actor made between 1 and 114,882 attacks against our honeypot. It is impossible for a human to try hundreds of thousands of different login attempts. We determined that a threat actor doing more than 50 login attempts must be relying on some sort of automation. |
 |
Attackers frequently use an available list of credentials based on data leaks to perform their attacks. The second indicator of machine-like behavior, and one often used in a less tailored attack, is the fact that the attack will consist primarily of credentials sourced through leaks. The biggest list of credentials formed from several data leaks is RockYou2021. It contains 8.4 billion passwords. For 50.8% of the attackers in the dataset, most of the passwords utilized are included in RockYou2021. The other half of the attacks might utilize some passwords included on the list, but they do not constitute the majority of their login attempts. |
 |
The third indication of machine-like behavior is the consistency of attacks. As mentioned, the dataset has been collected over a period of three months. The fact that activity associated with an attacker is found in the dataset over an extended period indicates that the attacks are most likely conducted by a machine. |
 |
In order to be efficient, brute forcing includes committing many attacks per second. Since it is physically impossible for a human to enter more than one set of credentials in one second, this behavior indicates machine-like behavior associated with automation of the attempts. |
Indicators of Human-Like Behavior
| We observed a pattern in which threat actors launch a sequence of login attempts, indicating they are likely leveraging a limited list of credentials. When this sequence of login attempts finishes and does not achieve a successful login, another block of attack using a different list of credentials, is launched. There is an identifiable pattern of repeated sequences between rapid login attempts followed by a long pause which indicates the moment a human intervened to launch or initiate another round in the block of attack using a new list of credentials. Therefore, we can conclude that the presence of a long pause preceding a block of attack is an indicator of human intervention. |  |
| Another aspect of an attack that indicates human involvement is how the attacks are “thought out” by the attackers – or the level of creativity included in the iterative steps. Interestingly, a subset of attackers seemed to be more creative as evidenced by their tendency to adapt the set of credentials using the specific domain name or certificate name of the honeypot. The information leveraged for the tailored attack has been collected – either by using specialized tools or by human intervention. In both cases, the fact that the attack is then customized for its target using this information indicates a level of sophistication typically associated with human engagement. |  |
| System administrators are encouraged to use configurations which require extra time between authentication attempts in order to make automated attacks less efficient. This is an effective technique against brute-force attacks. Indeed, attackers, who want to avoid detection or lockout, need to impose a delay of a few seconds between each login attempt. A threat actor implementing this behavior is interpreted as more sophisticated and therefore associated with human behavior. |  |
Engagement Score
To visualize the estimated level of human intervention, a score has been attributed to each attacker. One point was added for each indicator of machine-like behavior observed, and one point was subtracted when an indicator of human behavior was observed. The result forms a score of engagement from -3 to 4, and the frequency rate of the score is shown below.
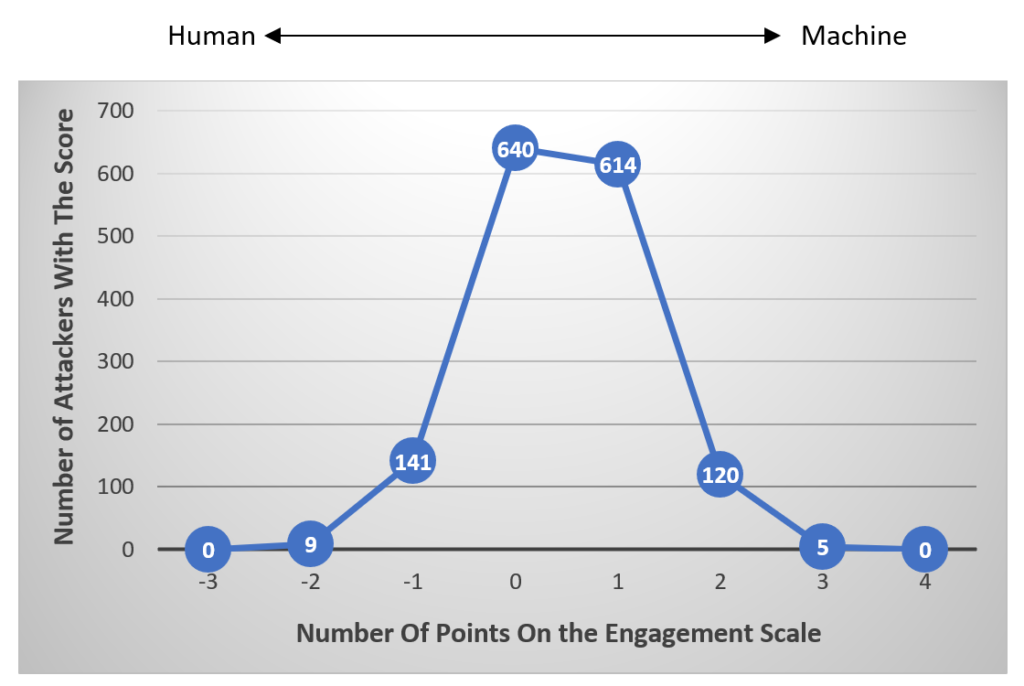
Figure 1. Frequency rate of engagement score
Most attackers scored 0 or 1 points and no attackers rank as “fully” human (i.e., -3 points score) or “fully” machine (i.e., 4 points score). This outcome is likely the result of the fact that sophisticated strategies like customizing attacks or even imposing a delay between login attempts to avoid detection are associated with high volume of attacks and, conversely, attackers with a small volume of attacks seem to be unrefined in their strategies. Of course, we know that while there is always a human behind an attack, the level of engagement indicated may be more than was expected.
An example showing attacker sophistication is the observation that the credentials used in the attempted logins are not taken from known data leaks readily available on the internet. As reported by DARKReading, Rapid7 researchers stated that 99.997% of passwords used by attackers on their honeypots were included in Rockyou2021 list. However, our results show that only half of the credentials (49%) captured in our dataset are included in the Rockyou2021 list. One factor that could at least partly explain this difference in data collected is the large number of customized attacks included in our dataset. In our exercise, 13.7% of attackers use credentials customized with the target system’s information, all of which are less likely to be part of RockYou2021 list. We suspect that Rapid7’s researchers data skewed to this outcome because their honeypots ran an older version of RDP without Network Level Authentication (NLA), which doesn’t expose information required for the customization efforts used by the attacker. Indeed, without NLA there is no way for an attack tool to extract the machine name or certificate name of the attacked server which is the source of the information used in the more custom attacks. Furthermore, our own non-NLA honeypots received fewer attacks as well. This corroborates Rapid7’s findings which are orders of magnitude less than on our NLA-enabled systems.
Customized attacks toward the RDP certificate name and hostname of the target were an element associated with automated attacks in the dataset of the present study. Several researchers have observed similar results. Contrary to what is conveyed by certain media outlets about attackers taking the easy road and not being creative, customizing attacks to the targeted victim seems to be a rather popular strategy that is frequently used by attackers. Since customized attacks are associated with automation, we hypothesize there may be a tool used to enable this form of attack. It would be interesting to determine whether such a tool is available publicly or on the Dark Web or if this would be a closely guarded tool used primarily by a single actor. More in-depth signal analysis of these attacks might help us reveal additional insights.
Conclusion
Evidence for human engagement, even in automated attacks, is strongly supported by our data. Even among the most heavy attackers, human-like behaviors are observed. The data indicates the majority of attacks are well thought out, and do not consist of simply trying a long list of leaked credentials in a fully automated attack. We draw two important conclusions from this work.
1. Increasing the cost to attack – in time, effort or funds – is likely an effective deterrent.
One of the observed strategies used by attackers was to avoid detection was to impose a delay of few seconds between attempted logins. To make things more difficult for attackers, new practices are being implemented by software vendors. For example, Windows 11 enables the Account Lockout Policy by default which automatically locks user accounts after 10 failed sign-in attempts. The account is blocked for 10 minutes, which will serve to decrease the efficiency of brute forcing significantly and will result in much more time-consuming attacks even if they leverage automation to try with new credentials after the 10-minute lockout has expired. The first important conclusion of this work is that prevention and detection efforts should focus on increasing the cost to attack for the attackers. Since most internet-exposed RDP systems are the result of a lack of understanding or sufficient resources to employ VPN technologies, we would encourage Microsoft to introduce the same account lockout policy they are deploying on Windows 11 on previous operating systems.
2. Additional research revealing the technology, tools & techniques used by attackers is required.
This second important conclusion drawn from our work indicates that additional research is required to reveal the precise tooling and strategies employed by opportunistic attackers as the data and subsequent analysis from our exercise revealed that attackers might be using automated tools to customize their attacks. We believe that exposing some of the groups responsible for the development, distribution and those using these tools may cause them to exercise more caution before performing opportunistic brute-forcing of RDP systems on the internet.


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Surveillance des événements liés aux informations de sécurité GoSecure TitanMC (SIEM)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC
Notre SOC
Défense proactive, 24h/24, 7j/7