 Rampant inflation is driving an increase in email-based threats – both as threat actors feeling the pinch find it harder to pay their bills and as desperate recipients experiencing financial hardships of their own fall prey to their tactics. Learn what to watch for to protect yourself from these “too-good-to-be-true” schemes.
Rampant inflation is driving an increase in email-based threats – both as threat actors feeling the pinch find it harder to pay their bills and as desperate recipients experiencing financial hardships of their own fall prey to their tactics. Learn what to watch for to protect yourself from these “too-good-to-be-true” schemes.
With inflation soaring to all-time highs worldwide, everyone seems to be dealing with the effects and finding themselves needing a little more money to cover gas, rent, groceries, and bills. Despite wage increases, earnings have not gone up fast enough to keep pace with inflation. So, what happens in the cyber world when a critical world event is occurring? Threat actors are opportunistically setting their traps to take advantage of needy and unwitting victims.
GoSecure analysts have seen a surge in the number of these, easy money scams with the biggest difference between these and other text-based scams being that they no longer seem to have to involve a large sum of money to grab the victim’s attention. Analysts have seen numbers as low as $300 a week being effective in drawing in targets.
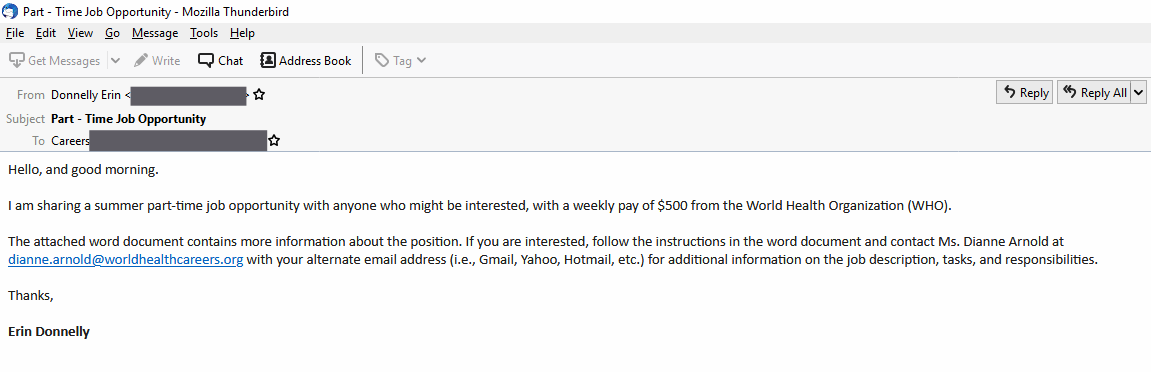
Let’s set the stage: The victim is in a “not enough money to make ends meet job” and they receive an email like this from a co-worker or classmate:
Attached is a letter explaining the work which appears to be on WHO letterhead:
Hello,
I am Dianne Arnold, Director and Clinical Counselor of Supply Division of World Health Organization (WHO).
I provide individual and group therapy, coaching, assessment, and academic screenings to support Students and educational workers with disabilities (Physical, Chronic, Psychiatric, & Invisible) registered with World Health Organization (WHO). A large percentage of the students and adult educational workers served by the mental health unit have psychiatric disabilities or co-morbid psychiatric disabilities and need mental health support to be successful at the educational institutions.
In addition, many University Students with academic difficulties and no prior diagnosis are seen and assessed through the academic screening and assessment process. I also am the director of supervision, training and coordination of counseling psychology and clinical psychology graduate students in the United States who have practicums at World Health Organization (WHO) and APA-accredited school psychology pre-doctoral interns.
Since the start of the COVID-19 outbreak, World Health Organization (WHO) has been delivering health supplies to many University Students and adult educational workers with academic difficulties to help in their response to the pandemic. You have received this email because you have an offer to work with me in your university as a temporary personal assistant to help deliver essential products and services to Students and educational workers with disabilities.
This is a very easy job. You will only help me purchase some Items online when needed and drop-ship to the assigned Student or educational worker with disabilities. This employment only takes about 1-2 hours per day and 3 times a week with a weekly pay of $500.00.
I am unable to call you for an interview because I am currently away in Singapore, and helping the disabled students in the Asia-Pacific region. You will be paid weekly for all tasks done on my behalf. As soon as I got back from my trip, we will discuss the possibility of making this job a long-term employment.
My arrival in the States is scheduled for Monday, August 22 2022.
To confirm your interest, kindly email me with your Full Name | Age | Address | your Yahoo, Gmail or Hotmail Email Address and your mobile number to my work email dianne.arnold@worldhealthcareers.org
I will send you more details on the job description, your duties and responsibilities as soon as I receive from you.
Sincerely,
Dianne Arnold
Director, Supply Division
dianne.arnold@worldhealthcareers.org
These types of fake employment scams can motivate the victim across many levels:
- Immediate, sometimes desperate need for extra income
- Appearing to come from World Health Organization (WHO), an organization which became well known during the Covid-19 pandemic
- Tugging at heartstrings by indicating the position will be helping disabled students or educational workers
- Appearing to be very easy to get started. Initially, there is no need to fill out a long form (YET!) nor do they ask for any personal information (YET!)
One might be inclined to be more confident in the offer if they received this from a colleague, classmate or maybe a friend, and additionally that the sender wouldn’t share it with me unless they’d already investigated it.
THINK AGAIN! Threat actors leak 5.5M email addresses a day and are experts at spoofing, concealing the actual sending, making targets believe it was sent from a trusted source. It is always considered best practice when it comes to any request involving money or personal information to contact the sender by means other than email to confirm that the email request is legitimate.
Things to look for which indicate potential threats:
- Domain names that are unfamiliar, overly long or complex, or that do not match those of the organization being referenced, such as
worldhealthcareers.orgwhich isn’t the WHO. - The job offer seems too good to be true, 1-2 hours a day, 3 times a week. So, in theory, if this was a legitimate job, a person would make between $83 and $166 an hour. It may seem like a great offer, but it is 100% fake.
- Does the language, grammar or spelling within the email or any attachment being sent or included seem off?
- Does the Reply To address match the from address?
GoSecure IDR routinely checks similar emails for these and other indicators that might call the legitimacy into questions, detecting threats before they become a problem. Industry leading technology along with expert human analysis adds a layer of security that protects you, your colleagues and your company from email borne threats.
Top Threat Subject Lines (look for variations):
- Free Piano Giveaway
- Memo From HR
- Email Portal Login
- You have a new voicemail
- You’ve received a document for signature
- Documents shared via Teams
- Payroll Statement
- UPS Pending Delivery
- I need help
- Please Read – Important from HR
Top Threats Blocked:
- Credentials Phish – Attached .html or link to a login page
- Password protected attached Zip – Password is included in body of email. Zip file may contain .exe, .img or similar type files
- BEC Phish – Email that appears to come from a superior in the need of help. The Sent-From email may be compromised or spoofed
- Malware Link – This could come in the form of a waiting document or a work-related document. It can also be seen as a business contact sending a request for a quote or business proposal.
- Funds Phish – This could come in many forms such as a package held in customs or a sum of money that is unclaimed.


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Surveillance des événements liés aux informations de sécurité GoSecure TitanMC (SIEM)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC
Notre SOC
Défense proactive, 24h/24, 7j/7