Author: Andréanne Bergeron
This blog post belongs to a series in which we examine various influences on password strategies. The first post in the series analyzed the macrosocial influence of a country on its citizens’ passwords. The second post was focused on the analysis of the influence of a community on password choice. In this last post, we aim to increase the strength of our readers’ passwords by influencing their password strategies using knowledge and insights from our research.
People are tired of dealing with the password nightmare. We all know we should select different passwords for every website or service we use and that each has different password requirements and policies to comply with. We are asked to have strong passwords and just when we get comfortable remembering them, they ask us to change them. It is increasingly hard to adhere to good password hygiene and strategies.
The objective of this blogpost is to explain how attackers proceed in trying to guess your passwords to further your understanding of what it means to have a strong password – or in other words, a password that is hard to crack. Suggestions and advice will be given on how to create not only strong but good passwords – those you can remember.
Figure 1 – One of the world’s most frustrating password’s policies experienced by our Research team
Let’s go back to the basics!
When you create an account on a website or service, you are required to specify a username and a password. The website or service then stores your credentials in their database to validate future login or access attempts. As no one is perfectly resistant to attackers, it is possible for this website or database to be hacked. Therefore, the best practice is for them to store the hashed value of your password so that it is not stored in clear text.
What is a hashed value and how does it work?
A hash is a unique value attributed to a virtual object like a document, a picture, a sentence or, in our case, a password. Hashing is an irreversible move. Once you have a hash value, it is impossible to “uncover” it. The only way you can identify what a hash hides is when you compare two hashes. Hackers therefore prepare a table in which they have a series of words and their attributed hash value. The first step in trying to crack your password, is to verify if the hash value attributed to your password correspond to one of the hashes in their list.
In their list, hackers have the most common password, popular names, common patterns on keyboard (keyboard walk), etc. Once they have tried their lists, they can also use brute force to crack a password. That process consists of generating a list of possibilities on-the-fly according to parameters given by the attacker. Hives Systems table show a comprehensive example of how much time it takes to brute force crack a password according to its characteristics. The time to brute force depends on many factors like the performance of the machine used to attempt the crack or the type of hash used. In the Hive System table, the machine runs with a RTX 2080 GPU, and the type of hash is MD5. It is also important to note that attackers will program their own rules which will change the performance of the cracking process. Rules are often based on users’ known behavior. For example, the rules programmed could order the cracking software to add the current year to a list of passwords, or the name of a season as we know that users frequently tend to add those types of information after their usual weak passwords. The table below is for illustrative purposes because results may vary widely.
The number of characters is the most important aspect to consider in avoiding the selection or use of easily crackable passwords. The table also highlights why it is important to have several different types of characters (including numbers, letters, and symbols or special characters) rather than a simple chain of numerals. The complexity of the characters used increases the difficulty of cracking. But why is that?
Why having a mix of character types is harder to brute force?
Imagine a password consisting of a single digit. What are the possibilities? 0 to 9 so 10 possibilities to try to guess it. If we consider a two-digit password, we have 0 to 9 times 0 to 9 (or 102) so there are 100 different possibilities. The math is straightforward: the number of characters that can be used to the power of the length of the password counted in characters. Now, if a password contains only lowercase letters, there are 26 possible characters that can be used in that position. When you mix both numbers and lowercase characters, you increase the count of possible characters to 36 possibilities that can be used in that position. If you add the set of uppercase letters, you increase the count to 62 possibilities for each position. Many password requirements in modern Web applications require passwords to include a symbol or special character. There are 32 basic symbols (“&”, “*”, “%”, etc.) on an English keyboard which will significantly increase the count of possible characters used in each character position of your password.
 |
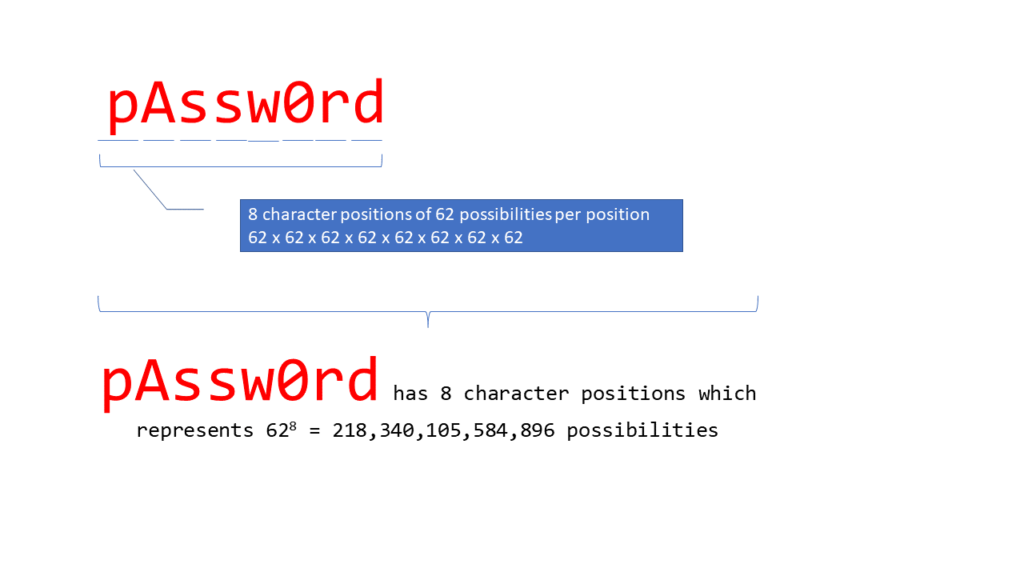 |
While it may seem that the number of possibilities noted above is quite large when using an 8 character password, given that a modern dedicated password cracking computer can typically perform up to 19,000,000,000 attempts per second we can calculate that the process of trying all possibilities up to 8 characters would only take a little over 3 hours. Note that this specific “pAssw0rd” example would take less than 1 second since it is already present in the lists of most commonly used password referenced by experienced password crackers. Now that you know what characterizes a strong (or hard to crack) password and why, let’s explore some advice for good passwords that you can easily remember.
Advice for not only strong but also, good passwords
Use a list of words:
Choose a couple of words and put them together.
Example : giraffe travel shelf empty
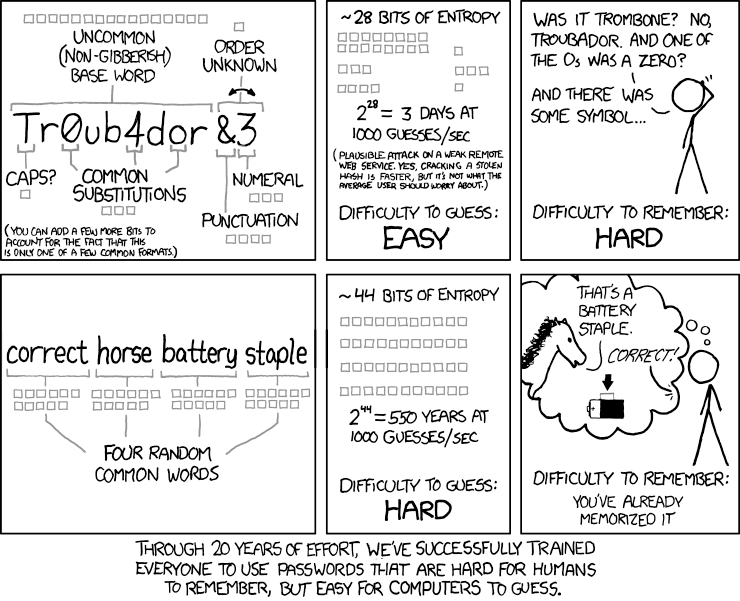
The usual advice is to avoid the use of dictionary words. However, there are more than a million words in the English language. Choosing a list of 4 words for example, dramatically increases the number of word possibilities that can be used in each word position in that type of password to 41,000,000. Even if attackers know that your strategy includes using a combination of words, the volume of possibilities is simply too immense to quickly test them all. This concept has been illustrated by the famous XKCD comic:
Cons:
It is highly unlikely however, that you would choose 4 words that will look like this:
Acetophenetidin Chincherinchee Sesquipedalian Whatchamacallum
The downside to using this strategy is the risk of choosing from the set of words that include the most commonly used words in everyday life. The solution would be to randomly generate the words selected to ensure the selection is not biased toward including only words used on a regular basis. Open source software can be used to generate truly random lists of words to be used as passwords for you.
Passphrases: Use a sentence
The use of a long sentence can be much easier to remember but still has a lot of characters.
Example: Ididnotsteelthe3gummybears,mybrotherdid.
This sentence contains uppercase and lowercase letters, a number, and two symbols (“.” and “,”). This strategy will satisfy a lot of password rules. If the website or service allows it, you can increase the complexity of the password by simply using spaces in your sentence which will often count as a symbol. Your sentence should be unique with meaning for you and should avoid popular quotes from a book or heard in a movie, as those are most likely to be added to the hackers’ list of hashes.
Bad example: “May the Force be with you.”
Cons:
Some websites, services, applications or corporate policies still have outdated password rules when it comes to setting a password or creating an account which prevent you from using a sentence as a password. For example, some policies limit the number of characters and others limit the number of repeated characters. For a good laugh – or a complete exasperation – have a look at the compilation of dumb password rules available on GitHub.
To complete your protection
We saw that one important aspect of a strong password is that it is not part of hackers’ cracking list. Hackers will use passwords from data breaches to add to their list. Using a password that is hard to crack might help avoid having it revealed even if there is a data breach. However, when your credentials are already in the possession of a hacker, you might want to consider staying vigilant and opt to change it, just in case. There are a couple of tools to help you monitor whether your data, including your credentials, are part of a breach. Have I been Pwnd (https://haveibeenpwned.com) is a website on which most known data breaches are listed and which provides the opportunity for users to enter their email address and verify if their information is still securely stored. Some tools monitor data breaches for you and send you an alert when your information is compromised. Services like this are offered by FireFox Monitor for example.
Conclusion
We hope that this explanation of how attackers crack passwords has helped you better understand how you can set strong passwords and develop good strategies around your use of passwords. We offered some insights and advice which are intended to be a starting point for developing your own strategies for selecting both strong and good passwords. As you do this, be mindful of the fact that what is prohibitively time-consuming for an attacker today, might not be as time-consuming one or two years from now.
Passwords will probably disappear in a few years. You have surely noticed the trend toward multi-factor authentication (MFA) which asks you to confirm your identity from a second factor (an external device, biometrics, etc.) is gaining popularity with many websites and services. This solution is protective but still carries the password burden and adds to a growing list of things one must do to be protected. That is why the FIDO Alliance, an industry association that specifically works on secure authentication, is working hard to develop a solution that will support passwordless environments. The objective is to make it simpler and much more secure than user password authentication. A standardized client-to-authenticator protocol will enable vendor-agnostic authentication with your biometrics encrypted on your end thus addressing privacy concerns.
In the meantime, we must still deal with passwords, so we hope that our little crash course was helpful.
If you’re wondering why we didn’t mention password managers as a possible solution to the password problem, it’s because the assessment of usefulness and user-friendliness are controversial topics that lead to an animated debate amongst members of our research team. We’ve taken note and appreciate that this suggests it ought be addressed in a future blogpost in this series on passwords. Stay tuned…
We would like to thank Olivier Bilodeau for additional research and writing.




CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Surveillance des événements liés aux informations de sécurité GoSecure TitanMC (SIEM)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC
Notre SOC
Défense proactive, 24h/24, 7j/7