
Tax season is upon us, and with it comes the annual increase in targeted threat tactics. While there are many steps you should take to protect yourself and your company, it starts with knowing what to look for. In this article, the GoSecure Titan Inbox Detection & Response (IDR) team shares insights about current tax-related phishing and malware threats, and what you should be on the lookout for. We’ll cover the top two tax season threats we’ve observed—attacks targeting tax preparers and attacks targeting individuals or businesses who are seeking professionals to prepare their taxes. We’ll also share examples and tips to combat these threats.
Attack #1 – Targeting Tax Preparers
One common attack during tax season targets tax preparers and CPAs. These attacks start out as an ordinary request with the attacker asking if the victim is accepting new clients. The first email will usually include a bit of a text – explaining where they found the victim’s contact information, that the tax situation is a bit unusual, or asking for the tax preparer’s rates. They include this text to add legitimacy to their request and to gain the trust of the victim.
If the victim replies confirming that they are accepting new clients (and sometimes even if they decline the offer) the attacker replies with a document or a link to a document, and another paragraph or two to add legitimacy, often urging the victim to review the attached “prior-year tax return.” Sometimes the document or link sometimes leads to phishing, but usually, it is a malicious document and results in a subsequent malware infection.
Warning Signs
These threats can be especially difficult for the victim to pick up on since they start out just like any other business request. Often the attacker sets up a fake business website or pretends to be affiliated with a legitimate business. Still, there are some signs you can look for if you are a potential victim of this type of threat.
Unusual language
These malicious requests are usually translated from a foreign language, and often include unusual words and phrasing. If you are thinking “who uses that word?” or “that’s an odd way to say that” it should be taken as a red flag.
Different reply-to
Attackers will often send their first message impersonating a real person at another company. However, since they aren’t really that person, they can’t receive replies to that address. To get around this, they set a reply-to address for an email account that they control. If you see a different reply-to address, that’s a red flag.
Not reading the previous message
These attacks often use canned responses and may be carried out by a robot rather than a real person. As such, their replies may seem like they didn’t even read your previous message. For instance, if you reply saying that you are not accepting new clients and then they reply thanking you for accepting them, that’s a red flag.
Password-protected documents
Attackers in these scenarios will often send password-protected documents, such as Office and ZIP files, and then provide you with the password in the same email. This is a big red flag and doesn’t make sense from a security perspective. If the password for the document is included in the same email, then anyone who got ahold of the email with the protected document would also be able to read the password in the email and open the document. Threat actors do this to prevent virus scanners from seeing the malware inside of a zip file or contained in the document.
Real-World Examples of Tax Preparation Attacks
An example of this attack was recently identified by the GoSecure Titan IDR team. The attack started out as an email from a prospective client asking if the recipient was accepting new clients.
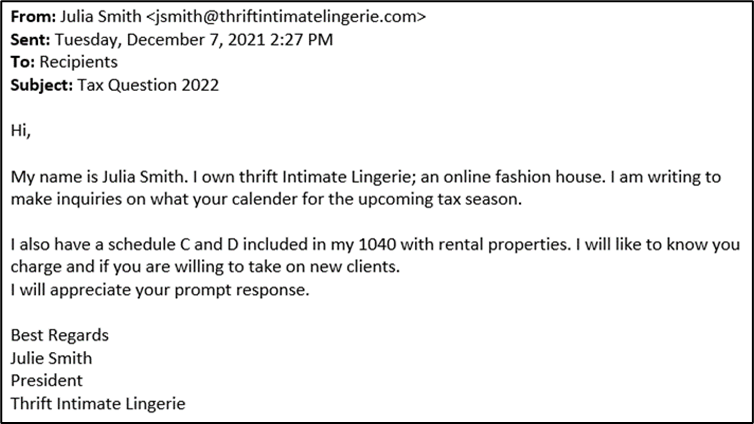
This initial email contains numerous red flags. First, the text has several misspellings and oddly worded sentences, such as “I will like to know you charge” when asking what the target charges for tax services. Second, the sending domain “thriftintimatelingerie[.]com” was registered the same day the email was sent. Third, the recipient was “Recipients,” meaning the email was Bcc’d to an undisclosed list of recipients. Attackers often do this as a “shotgun” approach, where they send a message to a list of targets and wait for a reply, then continue the attack targeting anyone who takes the bait.

One of the targeted CPAs replied stating that they were not taking new clients at the time. The attacker may have replied after this. However, we don’t have a copy of that exchange. But three months later, the attacker replied again.
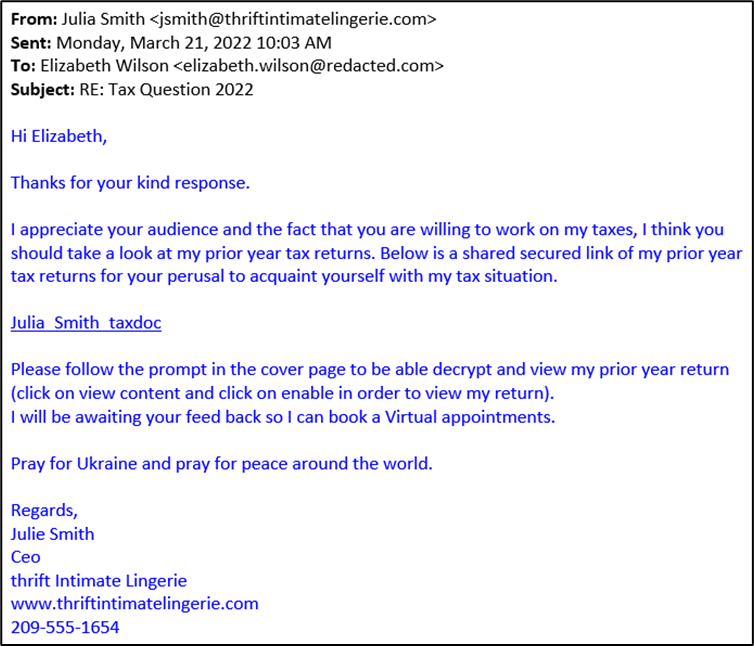
Again, this reply had numerous red flags. The first one that jumps out is that the reply seems to have ignored the original answer that the target is not accepting new clients. Second, the reply contains strange words and oddly worded sentences. A reference to current events is thrown in to make the request more believable. But most concerning was a link to a .doc file. When opened, this doc file (a9e5020fc2591d229defa48995a18f7ad17527cbaf944ccf744124f081976cb4) would use VBS macros to download a trojan.
How to Protect Yourself
There are steps individuals and businesses can take to combat attacks that target tax preparers. The steps below can help protect you and your organization from these threats.
Direct new client requests to a web form
One approach to defend against this threat would be to direct all new customers to fill out a web form before you agree to work with them. This might add some unwanted traction when it comes to acquiring new clients, but it will also prevent most of these attacks as the automated system will not know how to react.
Be cautious of risky documents
Tax returns from clients will usually be in PDF format. While PDFs can contain threats, they are usually considered safe if you keep your software up to date. If a client sends a document type you don’t recognize, or a document type that’s often abused, you should scan the document for malware before opening it. This is a good habit to get in in general.
You should be especially cautious of documents with two extensions, like “document.pdf.exe,” or any of the following extensions: htm, html, xls, xlsm, xlsb, xll, doc, docm, docb, zip, iso, img, rar, cab, exe, lnk, vbs, js.
It is also important to keep protections enabled when your computer or software blocks something that it considers a threat. Many malicious Office documents are blocked from installing malware, but then the malware shows a message telling you to disable the protection to view the document. If something urges you to click “Enable Editing,” a smarter choice would be to close the document and send it to your security team for inspection before proceeding.
Keep your software up to date
File types that are generally considered safe (such as pdf, docx, and xlsx) can pose significant security risks if your software is not kept up to date. This is because programs that open these files are sometimes found to have security holes that are fixed with updates. If you keep running the old versions with unpatched security holes, you’re giving attackers an opportunity to exploit them and install malware on your computer. It is also critical to keep your operating system, PDF viewer/editor, web browser, and Office software up to date.
Attack #2 – Targeting Individuals and Businesses Seeking Tax Preparers
The second common threat we find is to individuals and businesses seeking professional tax preparers. Threat actors posing as fake tax preparers can pose a big risk. This threat is especially significant in the pandemic era, as businesses seek guidance on pandemic relief tax benefits such as the Employee Retention Tax Credit.
Scammers have set up hundreds of fake CPA and tax consultancies offering to help businesses and individuals file taxes, including taking full advantage of these programs. From the outside, it isn’t clear what the motives are for each of these fake tax consultancies, but a likely goal is to defraud businesses of tax refunds they were entitled to. We’ll leave it to your imagination to determine what else a malicious entity could do if handed your personal or corporate tax and financial information.
Case Study
One such fake tax preparation site (employeetaxrefunds[.]com) was found in a phishing email by our GoSecure Titan IDR team.
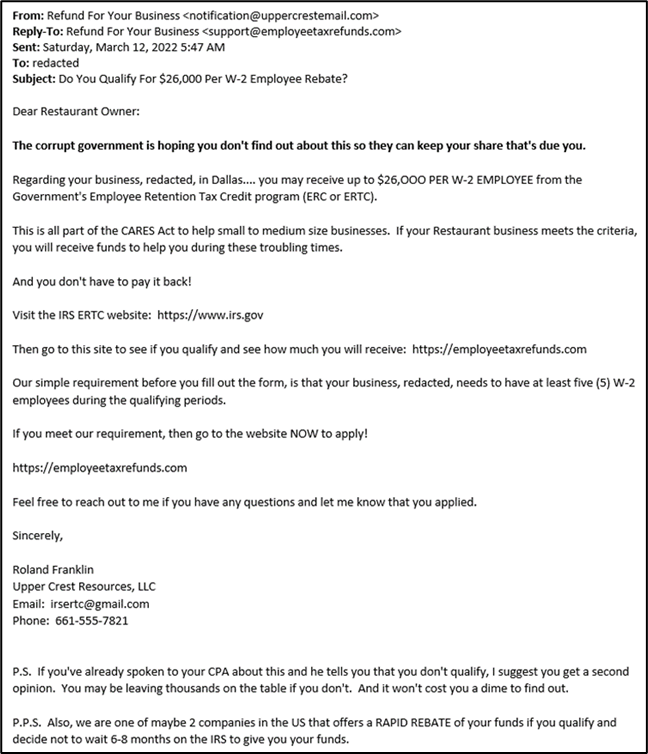
This site was asking for financial information from businesses under the guise of helping them claim an Employee Retention Tax Credit.
We selected a sentence found on the website and searched for it on Google, which revealed over 100 sites using the same or a similar template:
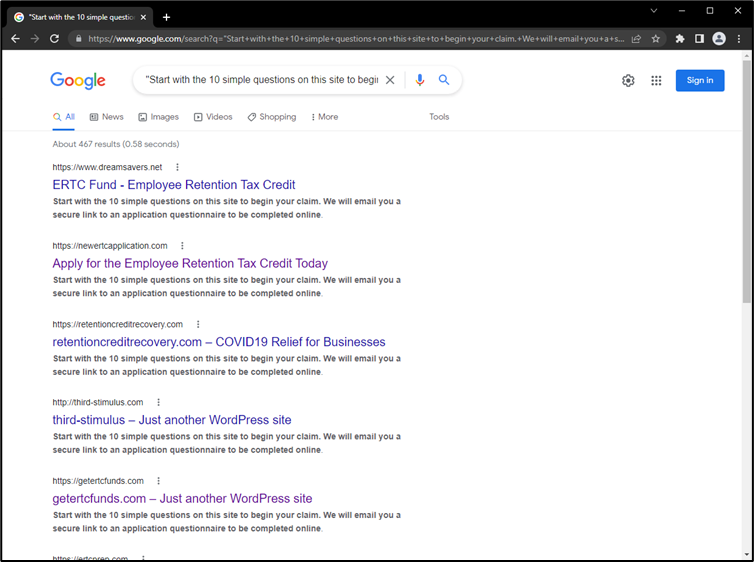
Among many others, these sites included:
- business-ertc[.]com
- eazyertcrefund[.]com
- erc[.]claims
- ercsubsidy[.]com
- getpandemicfunds[.]com
- myertc[.]net
- third-stimulus[.]com
- yourrecoverycash[.]com
Each of these sites included a different business name at the bottom of the site:
- Business ERTC
- Vipity Media Group
- ERC Claims
- ERC Subsidy
- TADCO Group dba: Get Pandemic Funds
- net
- TRICCO DIVERSIFIED SERVICES
- TransMedia Powerhouse
It’s not clear what these fake tax preparers would have done if they were given the information that was requested. Some actions they may have taken include opening a business line of credit in the company’s name, filing an ERTC claim with the IRS and taking the refund for themselves, or even filing a false ERTC claim and leaving the company to deal with the audit, or to pay back the refund.
How to Protect Yourself
There are several things to look for when hiring a new tax preparer or consultant. The safest choice would be to use a local CPA or financial institution, but if you decide to shop around online, keep an eye out for the following red flags.
Check for legitimate addresses
Many fake consultants will provide invalid addresses which cannot be found on a map, or the address of a legitimate business under another name. Always check the addresses provided on a suspicious website on a map program, like Google Maps, to see if the address exists and what is located there.
Not a licensed CPA or Enrolled Agent Check for legitimate addresses
You should only trust a certified or licensed representative to handle your personal or business tax information. Certified Public Accountants can be verified using a US state registry, or cpaverify.org. In Canada, you can verify the credentials of a Chartered Professional Accountant using their province’s CPA portal, such as cpaquebec.ca, cpaontario.ca, and cpaalberta.ca.
An Enrolled Agent can be verified with the IRS. Canada’s Canada Revenue Agency does not have an Enrolled Agent program, but the National Association of Enrolled Agents offers a listing of Enrolled Agents who also operate in Canada.
While you can trust an uncertified individual to prepare your taxes, you should at least ask for proof that they’re licensed to do business in their state or province. A person or company who is not certified or licensed to perform tax representation should be avoided. Also, keep in mind that a malicious actor can provide somebody else’s details to trick you, so while having credentials is critical, you should continue to scrutinize the business until you’re completely satisfied with their legitimacy.
Recently registered domain names
Many fraudulent tax preparers will have domain names that were registered in the last few months. To check for this, you can enter the domain name into a ‘whois’ site like the one provided by ICANN. If the registration date is less than a year old, the business could be fraudulent and should be vetted, especially if the website has text claiming to have “10 years in business!” or other similar claims.
Common sentences
One way you can spot a fraudulent tax preparer is to pick a sentence on their home page and Google it, surrounded by quotes. If multiple unrelated tax preparation sites come up in the search results, the site you’re looking at is likely one of many fraudulent sites using the same template.
Other Scams to Watch Out For – Fax Tax Notices
While we’ve identified the two top attacks we’ve been seeing lately, there are other threats to be wary of related to taxes and tax preparation. One of the most common year-round threats is fake notices from the IRS. Scammers often send emails claiming to be from the IRS. These emails might contain links to phishing or malware, and may use the following wording to try and lure you into clicking the links:
- “You are going to be audited by the IRS”
- “A warrant has been issued for your arrest due to tax fraud”
- “Your return was rejected”
- “There was an issue processing your refund”
- “Somebody else filed a return in your name”
If You Think You’ve Been Scammed
There are several steps you should take to avoid being scammed or if you find yourself the unfortunate victim of one of these attacks.
Report Financial and Identity Theft Immediately
If you find that your tax refund has been stolen, report the theft to the authorities immediately. If your identity is being used to open accounts, you should report the theft of your identity and/or financial information immediately as well. In the US, you can use the identitytheft.gov website, which will also provide an action plan for you. If you’re in Canada, you can report fraud here: https://www.antifraudcentre-centreantifraude.ca/ and here is a good resource for reporting in French: https://www.clinique-cybercriminologie.ca/
Monitor and/or Freeze Your Credit
If you suspect that your identity or financial information has been stolen, you should set up credit monitoring and look for any suspicious accounts that you don’t recognize. This can be done for free using services like Credit Karma. Consider placing a freeze on your credit if you don’t plan to open any accounts or take out loans in the near future. To do this, you would need to contact each of the major consumer credit bureaus. This will prevent an identity thief from opening any new accounts in your name and save you from the headache of fighting debt collectors and clearing your record.
Request an IP PIN
The IRS provides an Identity Protection PIN which you can use to protect your tax return. With this in place, an identity thief won’t be able to file tax returns in your name unless they also know your IP PIN.
Conclusion
These types of attacks happen every year and with each passing year, the attackers seem to become a bit more sophisticated. We hope by sharing this advice you’ll be better equipped to scope out the scammers and won’t fall victim. At the same time, phishing attempts are on the rise and can often be difficult to recognize. A solution like GoSecure Inbox Detection and Response (IDR) empowers users to submit suspicious emails right from the inbox so malicious attacks can be avoided.
Be sure to check this blog regularly for research, threat intelligence and security updates from the team at GoSecure Titan Labs. You can also follow GoSecure on Twitter and LinkedIn.
This blog was authored by GoSecure Titan Labs researchers Paul Neuman and Jonathan Gregson.


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Surveillance des événements liés aux informations de sécurité GoSecure TitanMC (SIEM)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC
Notre SOC
Défense proactive, 24h/24, 7j/7