 GoSecure Titan Labs team has discovered a significant number of fake banking websites through samples obtained from the GoSecure Titan Inbox Detection & Response solution. Unlike conventional phishing websites which impersonate specific banks to steal user’s login details, these sites attempt to portray themselves as the website and/or portal of a fictitious bank.
GoSecure Titan Labs team has discovered a significant number of fake banking websites through samples obtained from the GoSecure Titan Inbox Detection & Response solution. Unlike conventional phishing websites which impersonate specific banks to steal user’s login details, these sites attempt to portray themselves as the website and/or portal of a fictitious bank.
In this blog, the GoSecure Titan Labs team will detail their “Operation Bankroll” investigation, expose several fake bank websites, explain the expanding problem with fake bank domains and provide practical tips to avoid falling victim to the scams.
The purpose of these fake banking websites is not entirely clear and may vary, but some likely motives include:
- Attempting to take the credentials provided by a victim and use them to sign into the victim’s legitimate banking websites. (This is known as credential stuffing).
- Stealing funds from a victim’s bank account when they attempt to link them or transfer funds out of the fake account.
- Use the personal details provided by a victim to steal the victim’s identities.
- Use the fake bank accounts to facilitate investment scams. For example, Crypto investment scams are being spread widely on social media platforms with a focus on Twitter and Instagram. The threat actor will gain trust of willing investors possibly leading them to one of these many fake financial websites and after getting capital, will vanish. GoSecure Titan Labs researchers recently came across one such scam where it appears that at least a few dozen victims invested in a Facebook Crypto buying scam.
- It is also possible that some of these fake financial websites are being used in a much larger scale scam, such as a Ponzi scheme.
After observing some emails between a customer and a fake bank called « Universal Financial Bank, » we decided to dig a little deeper into this activity and see what was going on with these fake bank sites.
Universal Financial Bank
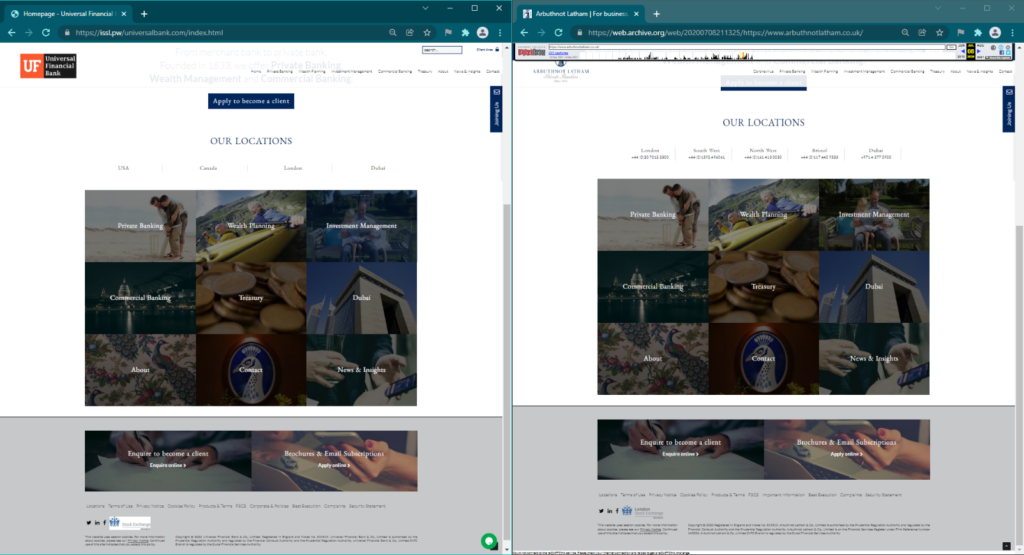
We found one bank calling itself « Universal Financial Bank » (UFB) at the URL hxxps[://]issl[.]pw/universalbank[.]com. This site and its contents were cloned from the website of the legitimate bank Arbuthnot Latham (AL) in mid-to-late 2020. Below is a screenshot showing UFB’s website side-by-side with an archived copy of AL’s website taken in July of 2020.
Besides adding their logo (and doing a poor job of photoshopping their logo onto a photo of one of AL’s buildings), the threat actor made only a few notable changes to the cloned site.
Tawk.to
The threat actor added a real-time chat and contact form app called Tawk.to using the id 5f2e6d455c885a1b7fb753f1. We left a message with them indicating our interest in opening an account, but they have yet to respond.
Changed Phone Numbers
All the phone numbers on the site were adapted from the original numbers listed on AL’s website by changing an arbitrary four-digit section to the letters « ARTH ». For instance, « +44 (0)1392 496061 » was changed to « +44 (0)ARTH 496061 ». This was likely done to prevent victims from calling the numbers without making them look fake, though it’s unclear why the attacker didn’t change them to something resembling their brand like « UFBK ».
The threat actors also added an entirely new phone number « +44 1632 690 668 ». Unfortunately, calls to this number were unsuccessful and a « not in service » tone was played.
Account Signup Forms
The threat actor also added forms where victims could sign up for a bank account. These forms were fairly short, but asked for some invasive details and information, including:
- Name
- Address
- Occupation
- Next of Kin name and address
- Copy of the victim’s passport
Once these forms were filled and submitted, the victim was redirected back to the same form with the text « Account Registration Successful. » However, we have yet to receive our account ID, and so we cannot log into this fake bank. We reached out to UFB’s provided email address at universalfinbank[@]issl[.]pw for assistance.
Attack Infrastructure
The domain issl[.]pw was registered via Namecheap on 09/14/2021. The fake banking site uses shared hosting with Namecheap on the IP address 198.187.31[.]121. The domain uses Namecheap’s Jellyfish service as its mail exchanger.
International Commerce Finance Bank
Another bank calling itself « International Commerce Finance Bank (ICFB) » (and sometimes « International Business Finance Bank ») was found at the URL hxxps[://]icbnk[.]com.
Original Content
Unlike UFB, ICFB didn’t seem to have copied its content from the website of a legitimate bank. Its content was more generic and was most likely part of the template that this threat actor was using at the time. We searched Google for one of the sentences found on the page, « We provide the best solution to your financial needs » [sic] and found more fake banks:
- SwedRegion Bank (hxxps[://]swedregionbk[.]com)
- RSWACU (hxxps[://]rswacu[.]com)
- British Finance Bank (hxxps[://]britishfinancebnk[.]com)
Although these fake bank sites contained that same sentence, they were actually using a different template with the sentence found in a different place. Searching again for another sentence from the site, « Save your money with us to enjoy great benefit of », we found more fake banks using the same template as ICFB’s site:
- International Business Finance Bank (hxxps[://]ifbnk[.]com)
- International Business Finance Bank (hxxps[://]ibfinancebk[.]com)
Opening an Account
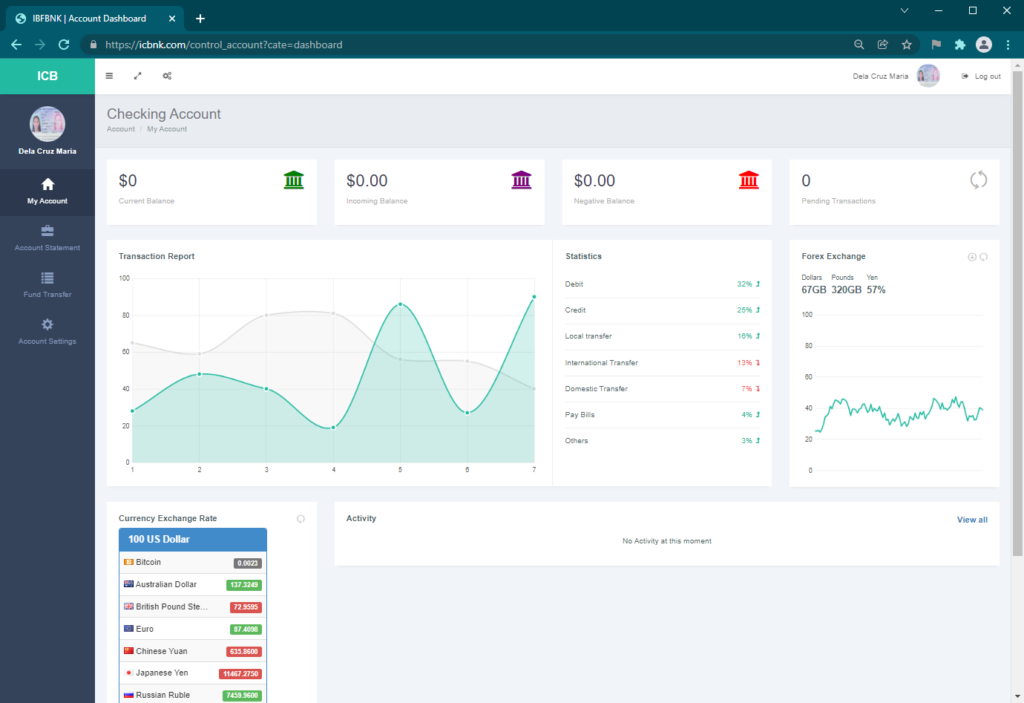
Like UFB, ICFB provided an account signup form, so we invited ourselves in to look around. Once we were logged in, we saw some pretty, though meaningless, graphs and a currency exchange rate table.
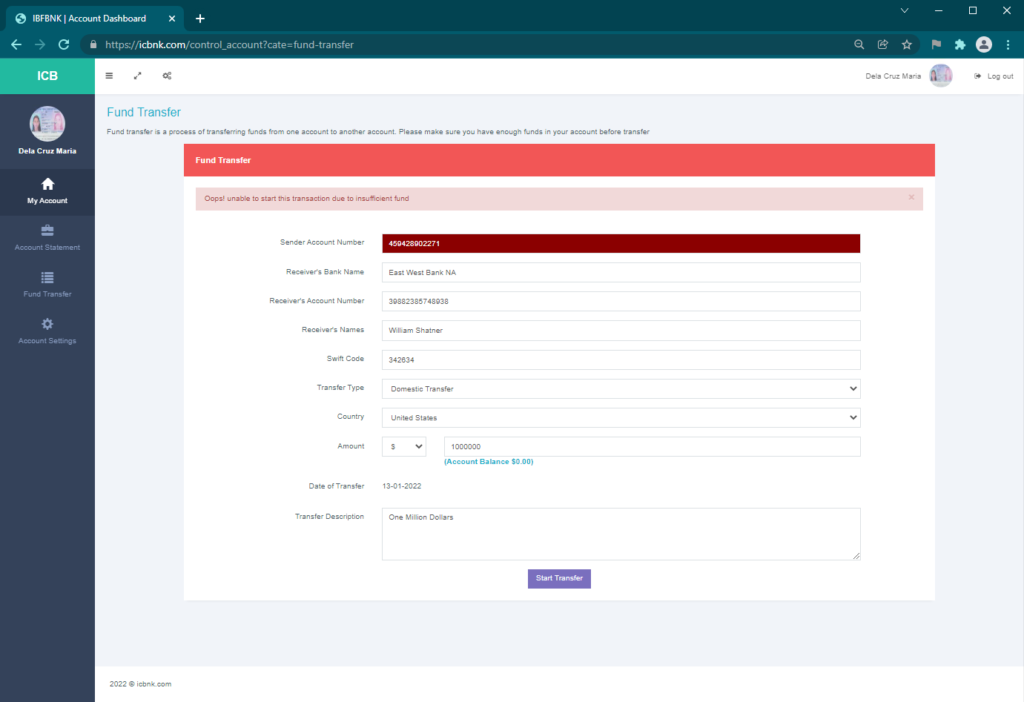
Once opened, the account contained $0.00. It might have been a good idea for the threat actor to have put a small amount of money in the account to entice new account holders to attempt to transfer it to their real account. Interestingly, the Fund Transfer page only seemed to support transferring funds out, but there were no funds to transfer.
International Business Finance Bank
We dug into the International Business Finance Bank (IBFB) to see what else we could find.
Fake Address
IBFB provided an address of « 1824 Brannon Street, Los Angeles, California, United States », which Google Maps insisted was not a real address. We dropped the address into Google and found several other fake banks and financial institutions:
- International Finance Bank (hxxps[://]intfinancebk[.]com)
- APN Financial Bank (hxxps[://]apnfinancebk[.]com)
- Gold Piece Management (hxxps[://]goldpiecemanagement[.]com)
- Apex Finance Bank (hxxps[://]apexfinancebnk[.]com)
- Airstro Finance Bank (hxxps[://]airstrofinance[.]com)
These were all using the same website template with a different logo. All of these institutions came up in a search for the Brannon Street address. However, Gold Piece and Apex were using different addresses: « 1435 Stockton St San Francisco, CA 94133-3816 » (a US Bank location) and « 9150 Elk Grove Florin Rd, Elk Groove, CA 95624 » (a PNC Bank location), respectively. Even stranger, Airstro listed the Stockton Street address as theirs, immediately followed by an address in Istanbul: « Giz Plaza No:3 K: 14, Maslak Istanbul 34396 » (the address of a shared office building.)
ICBNK (International Commerce Bank) lists an address of Shawnee Mission 10302 W 62nd ST Shawnee Mission, KS 66203 which shows to be the address of Oakside Apartments. If just a search with the words International Commerce Bank in Shawnee, KS a person would stumble onto a listing for Commerce Bank in Shawnee on Mission Parkway. The domain was registered at the well-known purveyor of questionable domains, NAMECHEAP in July of 2021. It is interesting that the domains are setup in order to get Google search results, so when searched, they appear to have even more legitimacy.
An Expanding Problem
We took a look at all domains registered between 07/22/2021 and 07/25/2021 and found hundreds of domains with the words « bank » or « bnk. » Most had already been taken down, but at least a dozen were still up when we looked:
- Trust Capital Finance Bank (hxxps[://]trustcapitalfinancebnk[.]com)
- Global Capital Bank (hxxps[://]www[.]capitaltrustbnk[.]com)
- Interbank Clearing House (hxxps[://]interbankclearinghouse[.]com)
- Mogano Safe Bank (hxxps[://]moganosafebank[.]com)
- Batrix Bank (hxxps[://]batrixbank[.]com)
- BDC Private Banking (hxxps[://]bdcprivatebanking[.]com)
- Geckobank (hxxps[://]geckobank[.]net)
- Moon Commercial Bank (hxxps[://]mooncommercialbank[.]com)
- Mi Heritage Bank (hxxps[://]miheritagebank[.]com)
- Pedcobank (hxxps[://]pedcobank[.]com)
- TD Inter Bank (hxxps[://]tdreservedbank[.]com)
- Heritage Forest Bank (hxxps[://]heritageforestbank[.]com)
It appears that multiple threat actors or groups have been creating hundreds of these fake banks every single day, often reusing the same template. Most are taken down in short order, but many remain online for months. We recommend that registrars look more closely at anyone trying to register a domain name containing the word « bank. »
According to the data we could find, over 5,000 domains were registered in December 2021 containing the words « bank » or « bnk. » While not all of them were fake banks, the majority of these domains have already been taken down or are back up for sale by domain brokers, suggesting that they were not originally purchased for legitimate purposes.
Tips: 8 Easy Ways to Spot a Fake Bank Website
1. Check for legitimate addresses
Many fake banks will provide invalid addresses which you can’t find on a map, or the address of a legitimate bank under another name. Always check the addresses they provide on a map like Google Maps to see what’s really there.
2. Invalid social media links
Almost all banks these days have active social media accounts. If the online bank you’re looking at doesn’t have any social media links, or if the links they provide don’t go anywhere, there is a good chance that they’re not a legitimate bank.
3. Not an FDIC or NCUA member
Almost all legitimate banks will be members of the Federal Deposit Insurance Corporation (FDIC). You can enter the name of an online bank in the FDIC’s BankFind Suite to check if it is registered with the FDIC. For credit unions, you can check the NCUA’s Research a Credit Union tool. International or foreign banks should be registered with a governing body in whichever country they’re headquartered in. For Canada, this is the Canada Deposit Insurance Corporation (CDIC), which provides its list of members. If you are unable to verify a government charter or registration with an online bank in question, chances are it is a fake bank engaged in some kind of fraudulent activity.
4. Unbelievable terms
Many fake banks will try to lure you in with unbelievable terms, such as “no interest” or an offer to give you money just for opening an account. Always keep the adage in mind: if it seems too good to be true, it probably is.
5. Inconsistent or poorly made websites
Most banks, especially online-only banks, put a lot of money and care into their websites. After all, these websites are an extension of the bank’s physical locations, or possibly the bank’s only way to make an impression. If the website is full of inconsistent design elements, misspellings, poor grammar, missing images, broken links, etc., there is a good chance that it isn’t a legitimate bank.
6. Links that don’t go anywhere
Many fake banking websites will have a page full of links to the programs they offer, but when you click on them, you’re not taken anywhere. They do this to appear as if they’re a full-featured bank without having to maintain a lot of bogus pages.
7. Recently registered domain names
Many fake online banks will have domain names which were registered in the last few months. You can enter the domain name into a ‘whois’ site like the one provided by ICANN. If the registration date is less than a year old there is a good chance that the bank is fake, especially if the website has text claiming to have « 15 years in business. »
8. Common sentences
One way you can spot a fake online bank is to pick a sentence on their home page and Google it, surrounded by quotes. If multiple unrelated banking sites come up in the search results, the bank you’re looking at is likely one of many fake banking sites using the same template.
Key Takeaways
As the use of digital and online banking continues to grow, threat actors have embraced this as an opportunity to expand their method of targeting by creating fake banking websites to steal user information. The number of fake sites has increased significantly over the past few years and typically this deception goes unnoticed. Thanks to samples collected through the GoSecure Titan Inbox Detection & Response solution, GoSecure Titan Labs has been able to expose several sites and share this a guide to spotting new fakes as they are created. Be sure to follow GoSecure on Twitter and LinkedIn for more security news and investigations.
This blog was authored by GoSecure Titan Labs researchers Paul Neuman and Jonathan Gregson


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Surveillance des événements liés aux informations de sécurité GoSecure TitanMC (SIEM)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC
Notre SOC
Défense proactive, 24h/24, 7j/7