As part of our research on Cybersecurity Perceptions Versus Reality, we developed a survey in collaboration with Serene-risc, a knowledge mobilization network in cybersecurity based in Canada, on the perceptions and practices of cybersecurity professionals. The survey aimed at understanding how defenders perceive specific security measures and whether these measures were implemented in their respective organizations. We then combined the survey results with our penetration testing experience to confront two perspectives: the defenders’ and the pentesters’, the latter standing as proxies for real attackers. This blog post summarizes the results related to endpoint visibility.


As part of our research on Cybersecurity Perceptions Versus Reality, we developed a survey in collaboration with Serene-risc, a knowledge mobilization network in cybersecurity based in Canada, on the perceptions and practices of cybersecurity professionals. The survey aimed at understanding how defenders perceive specific security measures and whether these measures were implemented in their respective organizations. We then combined the survey results with our penetration testing experience to confront two perspectives: the defenders’ and the pentesters’, the latter standing as proxies for real attackers. This blog post summarizes the results related to endpoint visibility.
Download the complete Cybersecurity Perceptions Versus Reality report, also available in French.
Defenders: Asset Inventory Matters
Endpoint visibility represents visibility on all devices at the edge of a network, such as laptops, desktops, mobiles phones, tablets, etc. We asked how much endpoint visibility respondents have on their entire organization. As shown in Figure 1, we find that 68.4% said high and very high visibility, 23.9% said moderate visibility, and 7.7% said no or low visibility.
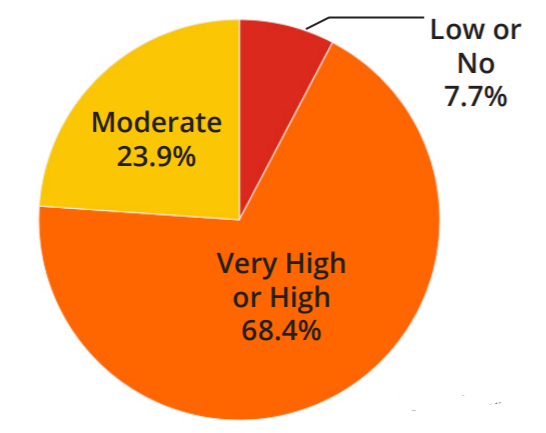
Figure 1 – Endpoint Visibility
Pentesters’ Experience
The fact that 68% of the respondents said that they had high endpoint visibility was surprising to penetration testers, who usually experience the opposite. They mentioned that the discrepancy may be explained by the idea that endpoint visibility perceived by the respondents is based on more traditional threats instead of more recent techniques using in-memory payloads and weaponized operating system features. In addition, based on pentesting experience, when compared with the tactics, techniques, and procedures frameworks (TTPs) like the Mitre Att&ck framework, the client’s endpoint visibility usually covers only a fraction of the known tactics and techniques.
Pro Tips on Endpoint Visibility
As a reference for readers, below are some pro-tips related to maintaining endpoint visibility on corporate networks.
- Consider an Endpoint Detection and Response (EDR) provider to increase effective endpoint visibility and prevent sophisticated attacks
- Also, tools like Sysmon and Windows Event Forwarding (WEF) / Windows Event Collector (WEC) are free and, when well configured, are a good replacement/complement/addition to an EDR solution
Conclusion
These findings are part of the Cybersecurity Perceptions Versus Reality report that highlights the key results of a two-year long study that aimed at understanding a disconnect that exists between how defenders perceive the value of their implemented security controls, and the most common attack vectors leveraged by penetration testers acting as potential attackers. The report is available in French and the microdata of the survey is available online.


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Surveillance des événements liés aux informations de sécurité GoSecure TitanMC (SIEM)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC
Notre SOC
Défense proactive, 24h/24, 7j/7