
Download the complete Cybersecurity Perceptions Versus Reality report, also available in French.

Download the complete Cybersecurity Perceptions Versus Reality report, also available in French.
Defenders: Patch management matters, but…
Patch management has been, in the past years, a security measure at the center of the industry dialogue: patch your systems! Something that any cybersecurity advocate recommends. Obviously, with new vulnerabilities being disclosed every day, patching should always be a priority. When asked how important they believed patch management was for the security of their systems, over 90% of respondents said important or very important.
Asking how long it takes for their organizations to apply a security update once made available is where things get interesting. As shown in Figure 1, 18.42% said within hours, 28.95% within days, 33.33% within weeks, 15.79% within months, and 3.51% within years (yes, years!). With over 52% of respondents saying it take weeks, or longer, to apply patches. It’s no wonder that attackers are having a field day with things like ransomware or bitcoin miners exploiting recently disclosed vulnerabilities.
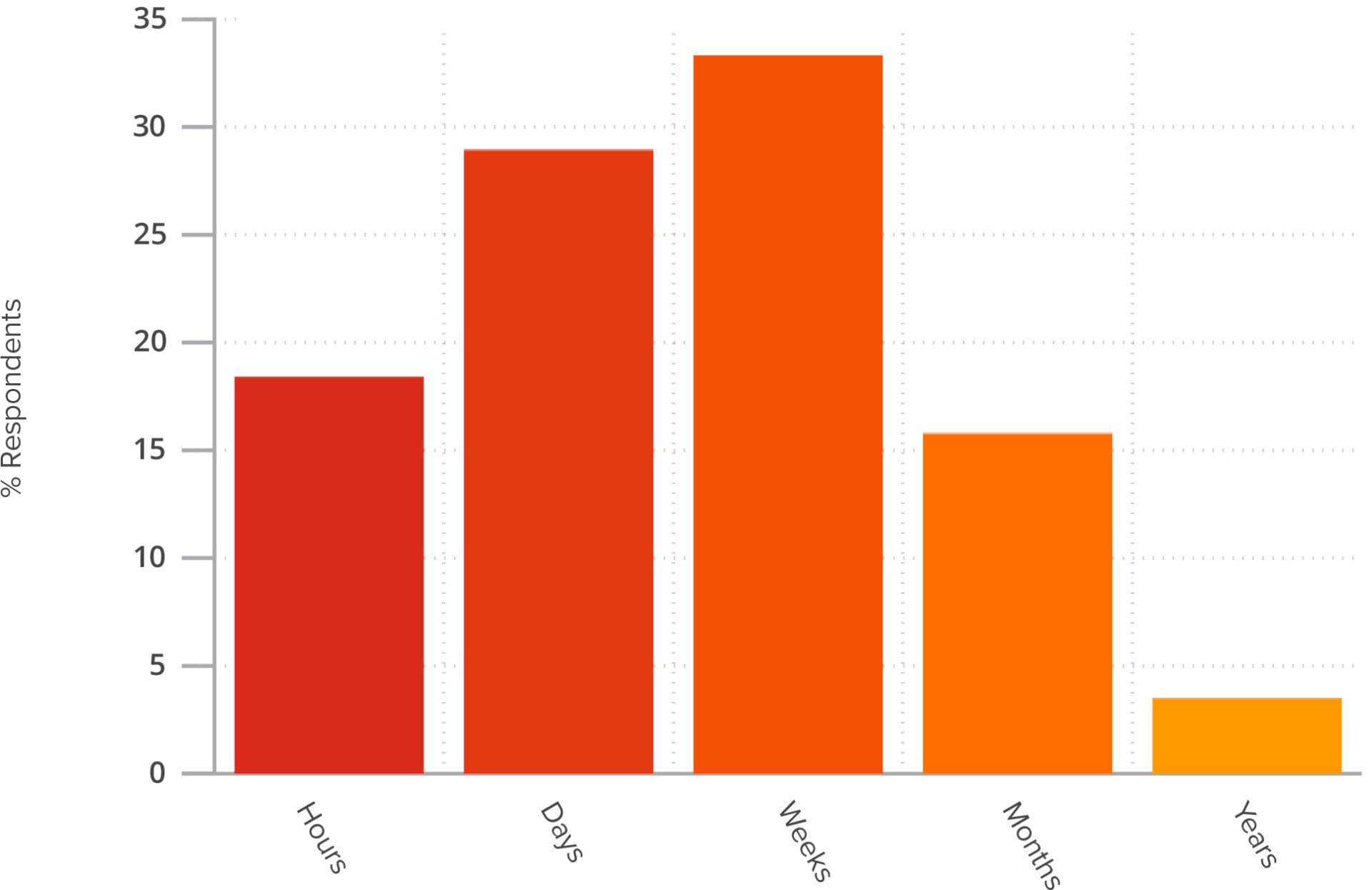
Figure 1 – Time required before patch management
Pentesters’ Experience: Watch for non-Windows patches as well!
Coming as no surprise, GoSecure penetration testers mentioned that the results expressed above are in line with their experience (although they have never been aware of an IT service responding within hours to a new security update). They stressed that most of the organizations they tested had a good patch management policy for Windows updates. However, other crucial applications, such as Java, Flash or Firefox, are usually less well maintained. They can sometimes create important vulnerabilities in systems when not kept up-to-date – vulnerabilities that testers are aware of and ready to exploit.
Lastly, they still find critical vulnerabilities such as EternalBlue (MS17-010), a vulnerability patched by Microsoft in 2017, in some of the systems they test. Before engaging in a pentest, it is recommended that you perform a thorough review of all available patches (including non-Windows patches) and apply as many as possible for your organization.
Pro Tips on Patch Management
As a reference for readers, we provide some pro-tips related to patch management on corporate networks.
- Consider standardizing the tools used by your employees. For example, if your employees use Chrome, Firefox, Edge, and Opera, it is hard to patch all these browsers. Thus, in this situation, limiting the users’ accessibility to a single browser could facilitate the patch management process.
- Develop a vulnerability management process that allows to identify, among others, missing patches and configuration issues.
- To minimize downtime risks caused by problematic patches, performing a gradual roll-out is the current best practice. This is called a phased deployment in Microsoft’s terminology.
- Use a vulnerability scanner to assess all the subnets on a regular basis to help identify and keep track of vulnerabilities on the corporate network. An open source one is OpenVAS.
Conclusion
These findings are part of the Cybersecurity Perceptions Versus Reality report that highlights the key results of a two-year long study that aimed at understanding a disconnect that exists between how defenders perceive the value of their implemented security controls, and the most common attack vectors leveraged by penetration testers acting as potential attackers. The report is available in French and the microdata of the survey is available online.


CAS D'UTILISATION
Cyberrisques
Mesures de sécurité basées sur les risques
Sociétés de financement par capitaux propres
Prendre des décisions éclairées
Sécurité des données sensibles
Protéger les informations sensibles
Conformité en matière de cybersécurité
Respecter les obligations réglementaires
Cyberassurance
Une stratégie précieuse de gestion des risques
Rançongiciels
Combattre les rançongiciels grâce à une sécurité innovante
Attaques de type « zero-day »
Arrêter les exploits de type « zero-day » grâce à une protection avancée
Consolider, évoluer et prospérer
Prenez de l'avance et gagnez la course avec la Plateforme GoSecure TitanMC.
24/7 MXDR
Détection et réponse sur les terminaux GoSecure TitanMC (EDR)
Antivirus de nouvelle génération GoSecure TitanMC (NGAV)
Surveillance des événements liés aux informations de sécurité GoSecure TitanMC (SIEM)
Détection et réponse des boîtes de messagerie GoSecure TitanMC (IDR)
Intelligence GoSecure TitanMC
Notre SOC
Défense proactive, 24h/24, 7j/7